Ransomware Recap: Threats from Open Source Code on the Rise
 Cybercriminals from around the world are still abusing Hidden Tear, which was originally released to educate and enlighten people about ransomware. This week we’re seeing the continuation of ongoing trends, not only with the use of open source code but with ransomware diversifying and getting regional variants. Ransomware developers are also diverging from the usual threat behavior, now including entertainment and public service announcements with their malware.
Cybercriminals from around the world are still abusing Hidden Tear, which was originally released to educate and enlighten people about ransomware. This week we’re seeing the continuation of ongoing trends, not only with the use of open source code but with ransomware diversifying and getting regional variants. Ransomware developers are also diverging from the usual threat behavior, now including entertainment and public service announcements with their malware.
The increase of Hidden Tear variants
Hidden Tear has been a problem since July of 2016, when we first detected variants based on the open source ransomware. The activity of Hidden Tear variants peaked in October 2016, but dropped quickly after. However, activity has picked up again in 2017, with a 142% increase in March compared to January.
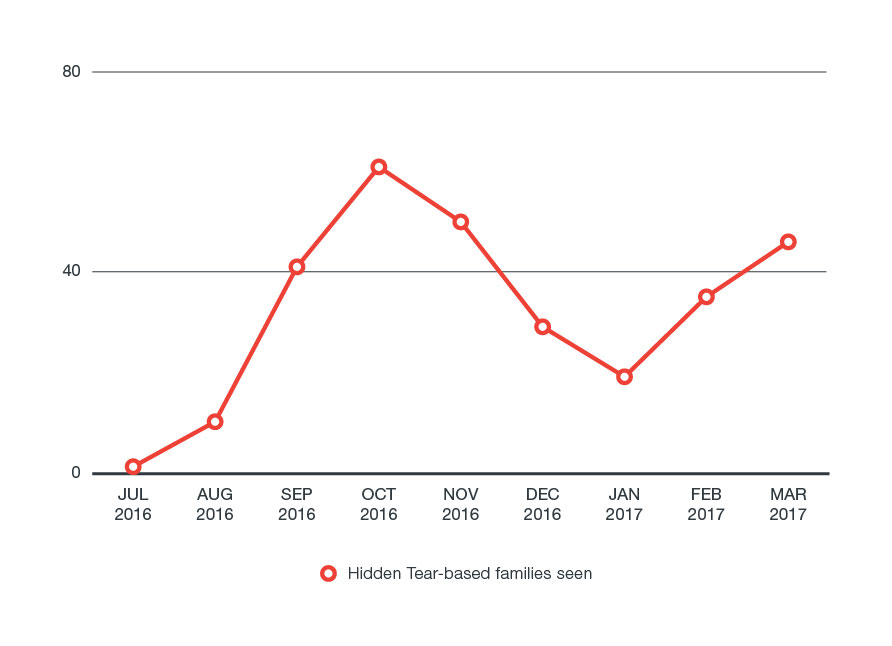
One of the main problems of open source ransomware is that it allows even novice hackers to develop more dangerous versions of the original and launch sophisticated attacks. The proliferation of Hidden Tear variants we’ve been seeing only emphasizes the hazards of releasing this type of code.
D3evilH0rn ransomware (detected by Trend Micro as RANSOM_HIDDENTEARANONFIVE) is one newly detected Hidden Tear variant. D3evilH0rn sets the ransom at .5 Bitcoin, or around US$600, and attaches .anonfive to encrypted files. It is still being developed.
Another Hidden Tear variant called Dikkat (detected by Trend Micro as RANSOM_HIDDENTEARDIKKAT.A) that targets Turkish speakers is also in development, as well as the Gembok ransomware (detected by Trend Micro as RANSOM_HIDDENTEARGEMBOK.A) which targets Indonesian users. Gembok targets only nine file types and asks victims to contact a Gmail address for more details.

Figure 1. The ransom note of the Hidden Tear-based Turkish ransomware Dikkat
The ransomware XYZware (detected by Trend Micro as RANSOM_HIDDENTEARXYZ) is a variant that possibly originates from Indonesia. The source code is copied from another Hidden Tear-based ransomware called Mafiaware (covered by Trend Micro as RANSOM_CRYPTEAR.SM), which was created by an Indonesian hacker. XYZware's ransom is set at only .1 Bitcoin (around US$120), and the developers ask that proof of payment be sent to a Gmail address.
Hidden Tear game changers
Every ransomware developer has different demands, but this one is particularly unusual. Instead of demanding money, they demand participation. Dubbed RensenWare (detected by Trend Micro as RANSOM_HIDDENTEARRENSEN.A), this Hidden Tear-based variant forces the victim to play “TH12~ Undefined Fantastic Object” and meet a certain score to recover the files. It’s unclear what the motive behind this ransomware is, but the developers seem to be invested in this game.
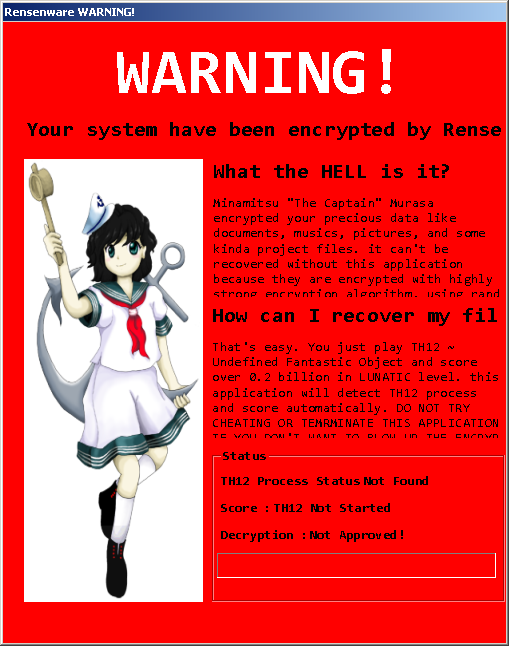
Figure 2. The RensenWare ransom note includes a mascot
Like RensenWare, another ransomware that forgoes the ransom payment is the Hidden Tear-based variant Kindest ransomware (detected by Trend Micro as RANSOM_HIDDENTEARKINDEST.A). Once a device is infected with “the Kindest ransomware ever” they are given a link to more material teaching them about ransomware, without demanding a cash ransom. Though this is unusual, it isn’t the first educational ransomware that teaches victims through experience.
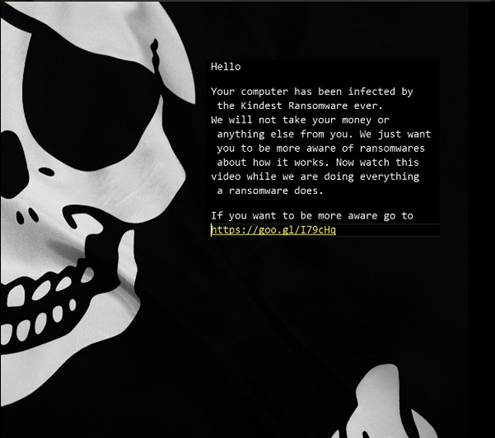
Figure 3. The Kindest ransomware includes a link to a YouTube video on ransomware
Multi-alias Chinese ransomware
A departure from all the Hidden Tear variants this week is a Chinese ransomware with a lot of aliases: LLocker, lucky88, ruFucker, 003Lock, lambdaE-speakingNC, AlphaE, BloodCrypt, TrueFucker (all detected by Trend Micro as RANSOM_LAMBDALOCKER.A). Written in Python and compiled to an .exe file, this particular ransomware demands .5 Bitcoin, or roughly US$600, and gives its victims a top ten list of Bitcoin trading sites for easier payment. The authors call themselves the LambdaAntiSocietyTeam (LASTeam) and NukeScriptTeam.
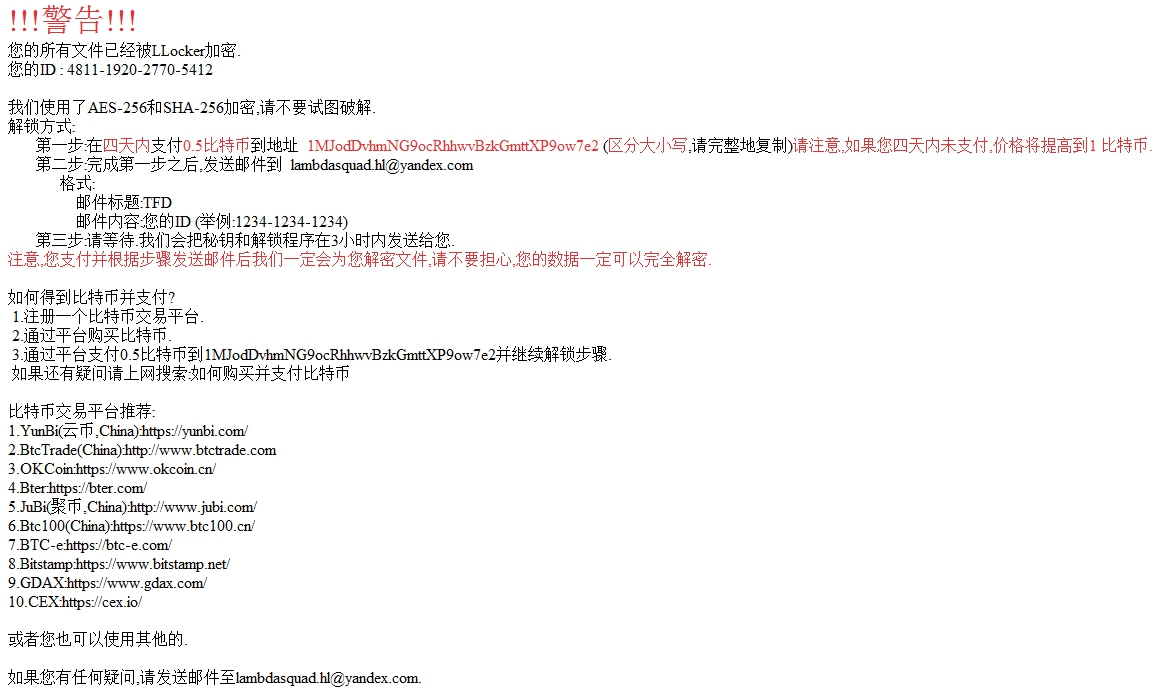
Figure 4. LLocker ransom note
This week we see that ransomware is a global problem, which is only exacerbated by resourceful developers who take advantage of any new technology or code. Users from different countries have to be aware that these threats continue to grow, and they can come from cybercriminals that may be familiar with local social engineering lures, vulnerabilities, and weak points.
Ransomware Solutions:
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks