Dealing with the Mess of DRIDEX
Updated October 13, 2015
Online banking, while convenient and widely used, is not without its threats - and in terms of notoriety and effectiveness, DRIDEX is right up there with the worst of them.
DRIDEX is one of the notable online banking malware that has multiple information theft routines such as form grabbing, clickshot taking, and HTML injections or the ability to ‘inject’ malicious code into certain websites that the affected user is currently viewing. Instead of a login page sending the entered credentials to the organization, it sends the information to the cybercriminals.
Considered to be the successor of GameOver ZeuS (GoZ) malware, DRIDEX uses an improved version of GoZ peer-to-peer architecture to secure their C&C servers against detections. First spotted around July 2014, DRIDEX also has semblances to another online banking malware CRIDEX. However, unlike CRIDEX that leverages vulnerabilities, DRIDEX uses macro, a feature in Microsoft Office applications.
While DRIDEX mainly targets major online banking/financial institutions based in Europe, our recent data shows that it also hit the US. A testament to its prolific spread in the Internet, DRIDEX ranked 7th in the top 10 online banking Trojans for the first half of 2015, in terms of infection counts.
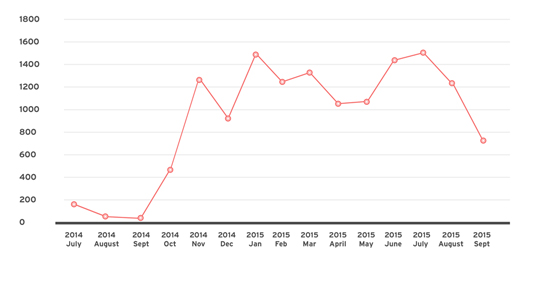
Figure 1. DRIDEX detections (using DRIDEX related hashes) from July 2014-Sept 2015
In addition, it also operates a botnet as a service (BaaS) business model—infected systems become part of the botnet and at the same time, other cybercriminals and threat actors also become affiliates to DRIDEX.
Entry points
DRIDEX variants arrive onto users’ systems through spammed email messages. The spam samples we’ve gathered purport themselves to be notices of the financial nature and sent by legitimate companies. These spammed messages invariably come with a malicious attachment: a Microsoft Word document that contains malicious macro code (detected as TROJ_WMSHELL.A). The attachment pretends to be invoices and account documents to lure users into thinking that this is a legitimate document instead of a macro malware.
Should the recipient open this Word document, the macro code then executes, downloading DRIDEX malware onto the affected system.

Figure 2. Sample screenshot of spammed message
Note that macros in Microsoft Word document are disabled by default. The code will execute once this feature is enabled by users. In this instance, the effective use of social engineering comes into play to lure users into enabling it thus executing the malware without their knowledge.

Figure 3. Users need to enable the macros in Microsoft Word to run the malware.
Following the DRIDEX trails
When the malicious macro is executed on the system, it downloads the DRIDEX loader that serves as stage 1 malware. It then points to the DRIDEX .DLL file that contains the information-stealing and man-in-the browser routines.
Once installed and executed in infected systems, DRIDEX variants are capable of the following information-stealing routines:
- Browser screenshot taking
- Form-grabbing
- Clickshot taking
- Site injections
In form-grabbing, the contents of HTML forms, particularly of log-ins are gathered. Similarly, the browsing activities of the victims—sites that they frequently visit and the personal identifiable information (PII) or credentials that they use while browsing these sites may end up in the hands of these cybercriminals. They can either sell it in the cybercrime underground or launch other nefarious attacks against these individuals and financial institutions.
When users access one of the monitored websites indicated in the configuration file, it will execute the information theft routines mentioned earlier. Part of DRIDEX’s C&C routine is to get information on the configuration file regarding what routines to do—i.e. if form grabbing, site injections etc. In addition, it may also download other modules such as VNC for remote control. All stolen information on the infected system is sent to the C&C servers.
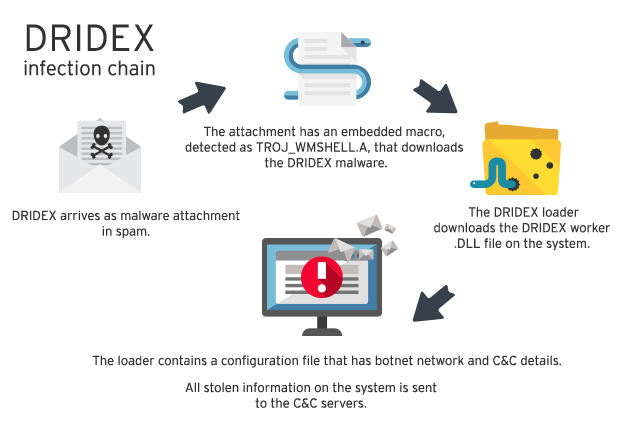
Figure 4. DRIDEX infection chain
The prevalence of this malware does not solely rely on its various information theft routines but also on several factors. For one, DRIDEX is capable of hiding its trails and tracks on the infected system by creating an autostart registry upon system shutdown as well as deleting the configuration file in the registry. Second, it uses a better version of the P2P network used by GameOver ZeuS malware.
Impact to users and banking/financial institutions
DRIDEX affects users by stealing their personal information (online banking account credentials) through its many personal information theft/browser monitoring routines.
It can also violate their privacy, as the login credentials stolen may also lead to the users’ other online accounts, such as social media, being broken into and/or hijacked. The screenshots taken may also inadvertently expose more of the user’s personal information.
To reiterate, the stolen information can be sold in the cybercrime underground and may possibly be used for launching other attacks. On the other hand, financial/banking organizations are also affected since security threats like this can tarnish their brand reputation, given that the spammed emails that DRIDEX sends out pretend to come from these legitimate organizations.
As mentioned earlier, DRIDEX operates on BaaS business model, which enable it to get more affiliates that can propagate this malware in other attacks and campaigns.
Mitigations and recommendations
To check your systems for DRIDEX malware presence, use Trend Micro HouseCall, our free online scanner. On the other hand, Trend Micro customers can use the Trend Micro™ Smart Protection Complete which offers a comprehensive solution with its multiple layers protection. It can detect the malicious macro file (TROJ_WMSHELL.A) as well as the DRIDEX variants. With its Email Reputation Service, it can block and detect all-related spammed messages thus preventing users from executing the malware at the entry point. All related C&C URLs are also blocked with its Web Reputation Service. Our solution also has data loss prevention feature to protect crucial information.
Users can protect themselves by adhering to the following best practices:
- Delete any suspicious-looking emails, especially if they sport links and/or attachments. Don’t even open them, just delete them. If they purport to come from legitimate organizations, verify with the organization in question first.
- Install an antimalware solution that also covers email in its protective scope. This should remove the chance of accidentally opening malicious email/malicious attachments in the first place.
- In case of a DRIDEX infection, immediately change online banking account passwords via a different (and hopefully uninfected) system, and touch base with the bank to alert them for any fraudulent transactions taking place. Users should do the same for any account that they may have accessed using their infected system.