New Spam Campaign Use Microsoft Branding to Deliver MirrorBlast
We observed a spam campaign that has been using Microsoft-related templates such as Office 365 and SharePoint notifications to spread new malware since September 2021. Along with usual lures like COVID-19, these spam emails trick users to open malicious HTML attachments or click malicious links, both of redirects unwitting users to download a malicious XLS file. The said XLS file contains macro code that leads to malware dubbed as MirrorBlast.
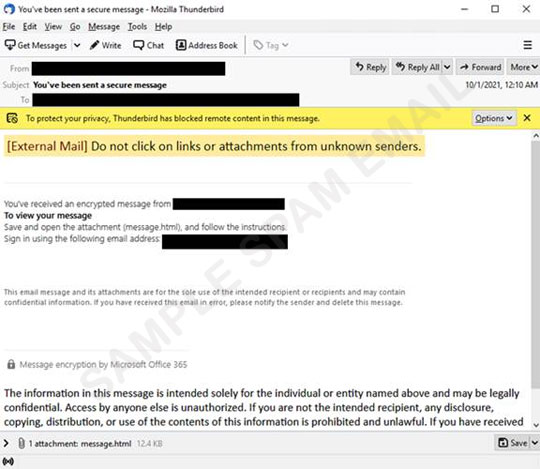
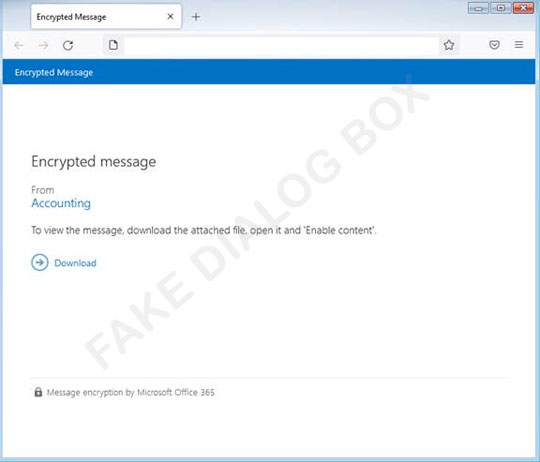
One spam email, using Microsoft Office 365 branding, deceives users that they received an encrypted message from their accounting department and they have to save and open an HTML attachment (detected as Trojan.HTML.DLOADR.VWGW) to view the message. The HTML contains more Microsoft branding to trick users to click the download button, which will then redirect to download an XLS file detected as Trojan.X97M.MIRRORBLAST.YXBJB.
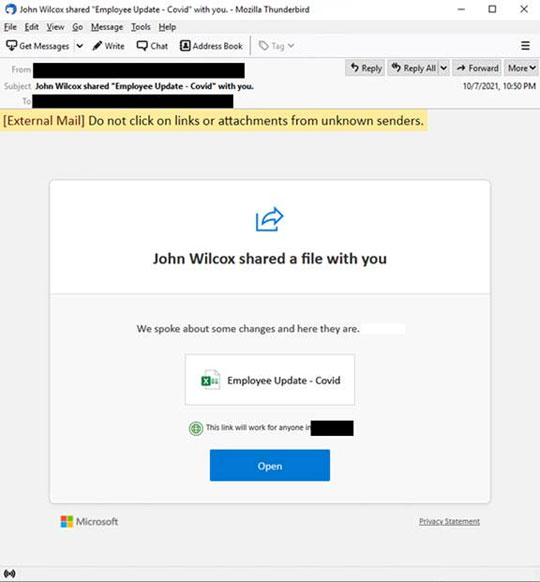
Another spam mail uses SharePoint notification and COVID-19 to manipulate users into clicking the malicious link, which leads to a similar XLS file downloaded in the previous spam mail. The XLS file downloads an MSI installer detected as Trojan.Win32.STARTER.UIIBHBP. This MSI installer drops other malware as well as a legitimate REBOL interpreter and scripts that can lead to C2 connections and, possibly, deployment of other dangerous malware such as ransomware.
As always, not opening email coming from unknown sources avoids further losses. Using anti-spam tools on your computers adds a layer of protection from these unwanted spam mails.
- ENGINE:8.6.1018
- PATTERN:6482
