HTML_FAKEVID.B
Windows 2000, Windows XP, Windows Server 2003


Threat Type: Trojan
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
When visited, this HTML displays a certain message.
It then redirects to a specific URL. This then leads to other site redirections, which then displays a fake video.
Clicking anywhere on the webpage displays a window asking for Facebook login credentials.
Once the user enters the login credentials, the window is closed. A wall post in the user's profile is automatically created together with a liked in a certain link.
Users that click the link is also redirected to a malicious URL. This may result into unwanted spamming of the fake video link.
This Trojan may be hosted on a website and run when a user accesses the said website.
TECHNICAL DETAILS
Arrival Details
This Trojan may be hosted on a website and run when a user accesses the said website.
NOTES:
This malware may be hosted on the following site:
- http://{BLOCKED}6.club96.info/wepay.html
When visited, it displays the following message:
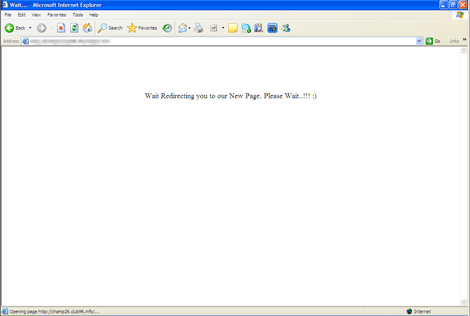
It then redirects to the following URL:
- http://{BLOCKED}6.club96.info
The said URL then redirects to the following website:
- http://{BLOCKED}r.video96.info/
The following fake video is displayed:
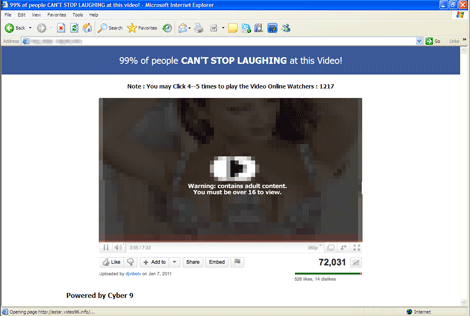
Clicking anywhere on the webpage displays a window asking for Facebook login credentials:
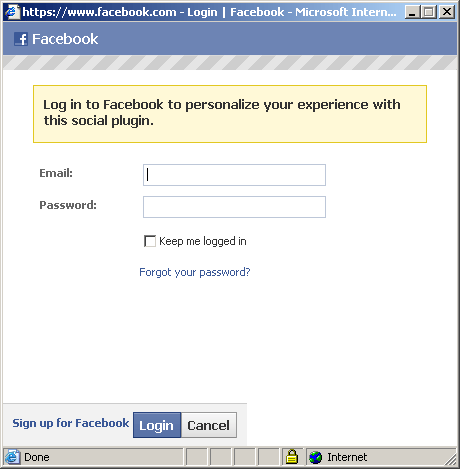
Once the user enters the login credentials, the window is closed. A wall post in the user's profile is automatically created together with a liked in a certain link, as shown below:
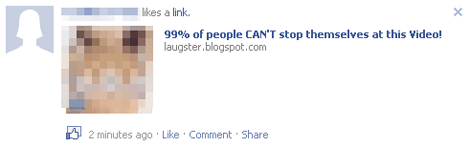
Users that click the link is also redirected to http://{BLOCKED}r.video96.info. This may result into unwanted spamming of the fake video link.
SOLUTION
Step 1
Close all opened browser windows
Step 2
For Windows XP and Windows Server 2003 users, before doing any scans, please make sure you disable System Restore to allow full scanning of your computer.
Step 3
Scan your computer with your Trend Micro product to delete files detected as HTML_FAKEVID.B. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.

