WORM_VOBFUS: A Polymorphic Downloader
November 29, 2012
The VOBFUS family of worms is known for their download and propagation routines, which allowed them to gain prominence, as can be seen in the family’s increasing number of variants over time. These worms are known for taking advantage of the Windows OSs’ AutoRun feature in order to spread via removable drives. These are also known for exploiting the .LNK vulnerability. Like other prominent malware families (e.g., ZBOT), these worms have polymorphic capabilities that enable them to add garbage code at every iteration and to modify the code in order generate new variants.

Cybercriminals can also employ WORM_VOBFUS variants to install other malware onto already-infected systems, rendering these unusable for certain periods of time. In effect, business operations may be disrupted, which can potentially lead to financial losses.
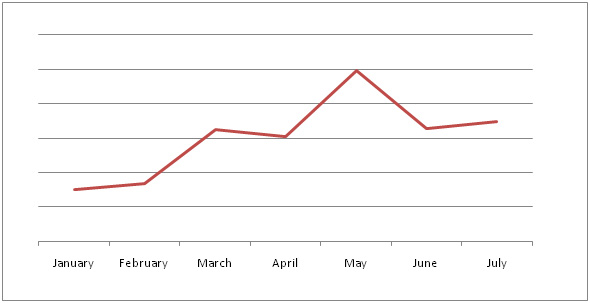
Figure 1. WORM_VOBFUS variants volume trend in the first half of 2011
Below is the number of infection related to WORM_VOBFUS starting November 23 - November 26, 2012, generated from the Smart Protection Network:

What are WORM_VOBFUS variants’ common infection vectors?
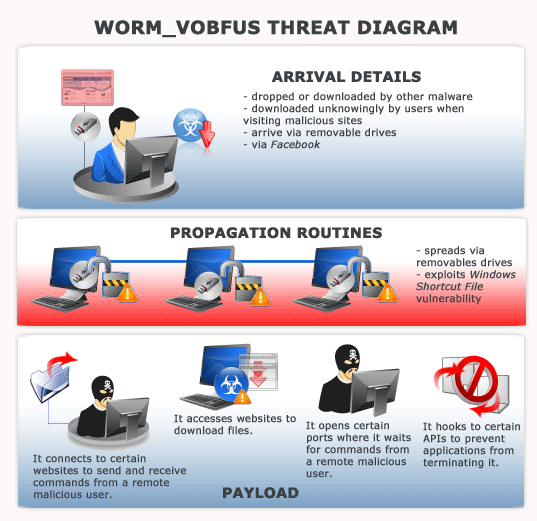
WORM_VOBFUS variants may be dropped or downloaded by other malware onto users’ systems or may be unknowingly downloaded by the users themselves when visiting malicious sites. These may also arrive via removable drives.
This malware also spreads via social networking sites, specifically on Facebook. Variants are typically bear sexually suggestive filenames.
How do WORM_VOBFUS variants propagate?
WORM_VOBFUS variants spread by dropping copies of themselves onto all removable drives connected to infected systems. These also drop an AUTORUN.INF file and shortcut files (i.e., those with .LNK file name extensions) onto infected systems so these can execute the copies they dropped. These .LNK files normally use the following file names:
- Documents.lnk
- Music.lnk
- New Folder.lnk
- Passwords.lnk
- Pictures.lnk
- Video.lnk
Note, however, that these .LNK files make use of default Windows file names instead of names with random characters so affected users won’t notice their existence. Some WORM_VOBFUS variants such as (WORM_VOBFUS.AI) use the Windows Shortcut File Vulnerability, the same one that STUXNET exploited. It does so by dropping the following files into removable drives that are connected to infected systems:
- z{random characters}.lnk
- xxx.dll
WORM_VOBFUS variants also use the names of already-existing folders and files in order to execute instead of folders and files these spoof. Some of these files and folders�use the following extension names:
- avi
- bmp
- doc
- gif
- jpeg
- jpg
- mp3
- mp4
- mpg
- png
- tif
- txt
- wav
- wma
- wmv
- xls
Moreover, WORM_VOBFUS variants change the affected folders’ attributes to Hidden and System in order to avoid detection and consequent removal.
What happens when users execute WORM_VOBFUS variants on their systems?
When executed, WORM_VOBFUS variants drop copies of themselves, aka %User Profile%\{random file name}.exe, onto the affected users’ systems. These also create AutoStart registry entries so they can execute every time an infected system boots up. These also connect to several sites to wait for commands from remote malicious users hence compromising the systems’ security.
A typical communication between an infected system and a malicious server would results in the latter sending packets that contain URLs that WORM_VOBFUS variants access to download files. As such, the files’ malicious routines are also exhibited by the infected systems.
Last but not least, these WORM_VOBFUS variants hook certain application programming interfaces (APIs) preventing applications such as Task Manager and Process Explorer from terminating their malicious routines.
What URLs do WORM_VOBFUS variants access to download files?
When executed, WORM_VOBFUS variants may access any of the following servers:
- server.{BLOCKED}et.com
- ns3.{BLOCKED}geparlour.net
- ns4.{BLOCKED}chhere.netnet
- ns2.{BLOCKED}turehut.net
- ns1.{BLOCKED}1253.com
- ns1.{BLOCKED}ll.net
- ns1.{BLOCKED}ll.org
- ns1.{BLOCKED}hares.org
Based on tests we conducted, the said servers may send the reply with the following download URLs in response:
- counterstrike.{BLOCKED}ain24.com:992/data/a
- counterstrike.{BLOCKED}ain24.com:992/data/c
- counterstrike.{BLOCKED}ain24.com:992/data/d
- {BLOCKED}udio.co.cc:992/data/a
- {BLOCKED}s.chello.pl/i.lemecha/index.png
- {BLOCKED}res.org:992/data/a
- {BLOCKED}res.org:992/data/c
- {BLOCKED}res.org:992/data/d
- {BLOCKED}res.org:999//ggg/a
- {BLOCKED}res.org:999//ggg/c
- vids.{BLOCKED}razy.cx.cc:992/data/a
- www.{BLOCKED}g.org:992/data/a
How do WORM_VOBFUS variants affect users?
WORM_VOBFUS variants function as downloaders of other malware such as VIRUX and FAKEAV variants onto the affected users’ systems. Further infections can put affected users' information at risk of being stolen by cybercriminals. Remote malicious users can send and receive information via/from infected systems, allowing the attacker to perform malicious activities without the users’ knowledge and to steal information that they can use for future attacks.
What makes WORM_VOBFUS variants noteworthy?
Expert Insights:
WORM_VOBFUS variants can easily be modified to come up with new variants identified by new MD5 hashes by simply adding garbage code to old ones. These also pose great risks to users, as these can download other malware with far more dangerous payloads onto already-infected systems. Finally, because these use effective code obfuscation techniques, they are very difficult to detect and even analyze.
Are Trend Micro customers protected from WORM_VOBFUS variants?
All Trend Micro products detect all known WORM_VOBFUS variants with the help of the Trend Micro™ Smart Protection Network™. Web reputation Reputation Technology, in particular, blocks user access to all related URLs in order to prevent the download of the malware and their malicious components onto systems. Users are advised to keep their system patches up- to- date and to protect their removable drives by disabling their AutoRun feature.
“WORM_VOBFUS variants are notable because these can easily be modified to come up with new variants with the aid of their polymorphic routines. Cybercriminals can use these to download nastier malware onto already-infected systems, putting users at even greater risk of losing not just their critical data but also their hard-earned money. " —Jessa Dela Torre, Threat Response Engineer