AZORULT
Windows


Threat Type: Trojan Spy
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
The AZORULT malware was first discovered in 2016 to be an information stealer that steals browsing history, cookies, ID/passwords, cryptocurrency information and more. It can also act as a downloader of other malware. It was sold on Russian underground forums to collect various types of sensitive information from an infected computer. A variant of this malware was able to create a new, hidden administrator account on the machine to set a registry key to establish a Remote Desktop Protocol (RDP) connection.
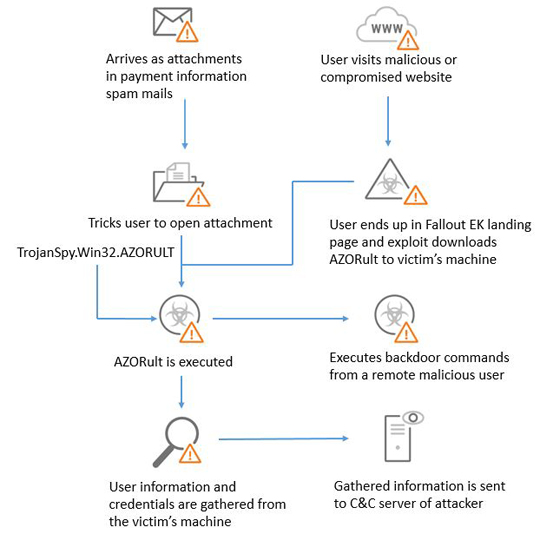
Exploit kits such as Fallout and phishing mails with social engineering technique are now the major infection vectors of the AZORULT. Other malware families such as RAMNIT and EMOTET also download AZORULT. The current spam and phishing emails use fake product order requests, invoice documents, and payment information requests. AZORULT connects to command and control (C&C) servers of attacker to send and receive information.
It is capable of the following:
- Steals computer data, such as installed programs, machine globally unique identifier (GUID), system architecture, system language, user name, computer name, operating system version
- Steals stored account information used in different installed File Transfer Protocol (FTP) clients or file manager software
- Steals stored email credentials of different mail clients
- Steals user names, passwords, and hostnames from different browsers
- Steals bitcoin wallets - Monero and uCoin
- Steals Steam and telegram credentials
- Steals Skype chat history and messages
- Executes backdoor commands from a remote malicious user to collect host Internet protocol (IP) information, download/execute/delete file
AZORULT typically follows the infection chain bellow: