HTML_FAKETUBE.A
Windows 2000, Windows XP, Windows Server 2003


Threat Type: Trojan
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This HTML script Trojan uses the Japan earthquake and tsunami tragedies in order to lure users to access a malicious website.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
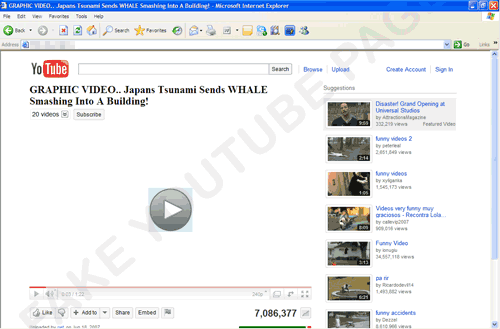
This is the Trend Micro detection for malicious HTML scripts that points users to visit a spoofed YouTube page upon clicking certain sites on a Facebook spam page. It displays a page that closely resembles the said video page. The loaded clip bears the title GRAPHIC VIDEO.. Japans Tsunami Sends WHALE Smashing Into A Building!. As of this writing, however, the said Web page contains errors.
It also displays a window that asks for the affected user's Facebook credentials, which may be used in accessing the account, clicking the Like button on the spam page, and posting malicious URLs on the walls of the user's contacts.
This Trojan may be hosted on a website and run when a user accesses the said website.
TECHNICAL DETAILS
Arrival Details
This Trojan may be hosted on a website and run when a user accesses the said website.
NOTES:
This is the Trend Micro detection for malicious HTML scripts that points users to visit a spoofed YouTube page upon clicking the following sites on a Facebook spam page:
- http://{BLOCKED}h.tk
- http://{BLOCKED}e.tk
- http://{BLOCKED}0111.tk
- http://{BLOCKED}p.tk
- http://{BLOCKED}n2011.tk
- http://{BLOCKED}-woot.tk
- http://{BLOCKED}crash.tk
- http://{BLOCKED}z.tk
It displays a page that closely resembles the said video page. The loaded clip bears the title GRAPHIC VIDEO.. Japans Tsunami Sends WHALE Smashing Into A Building!:
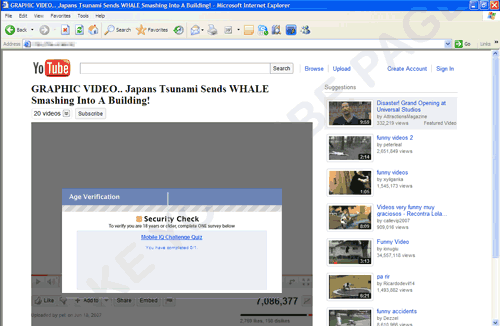
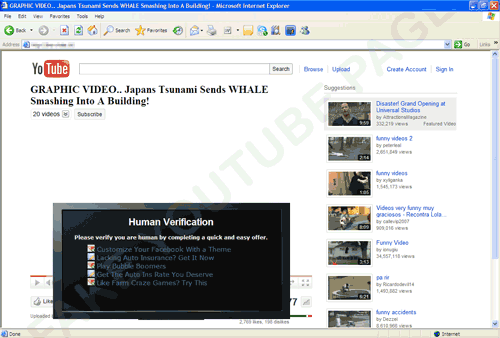
Once users click the video, it displays any of the following prompts that require users to fill out a survey:
Clicking the survey then redirects users to a Web page that asks for user mobile numbers:
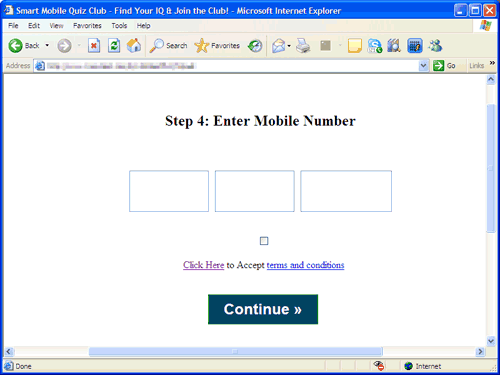
The said Web page is found to contain errors.
This script also displays the following window that asks users for their Facebook credentials, which may be used in accessing accounts, clicking the Like button on the Facebook spam page, and posting malicious URLs on the walls of affected users' contacts:
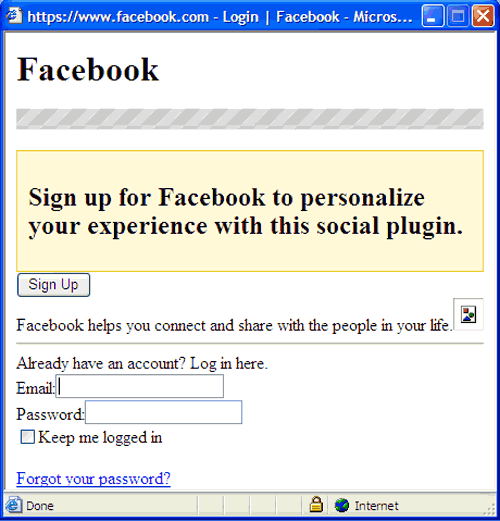
The said page is no longer available.
SOLUTION
Step 1
For Windows XP and Windows Server 2003 users, before doing any scans, please make sure you disable System Restore to allow full scanning of your computer.
Step 2
Close all opened browser windows
Step 3
Scan your computer with your Trend Micro product to delete files detected as HTML_FAKETUBE.A. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


