ANDROIDOS_CURIOUS.HRX
Information Stealer, Click Fraud, Malicious Downloader
Android OS


Threat Type: Trojan
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This Trojan gathers device information. It downloads malicious files. It sends SMS messages to premium numbers, resulting in unwanted charges billed to you. It drops and runs other files on the device. It displays pop-up advertisements. It uses common file icons to trick a user into thinking that the files are legitimate. This is the Trend Micro detection for Android applications bundled with malicious code.
TECHNICAL DETAILS
Mobile Malware Routine
This Trojan is a file that collects the following information on an affected mobile device:
- phoneNumber
- iMEI
- iMSI
- channel
- chargeKey
- cityInfo
- location
It gathers the following device information:
- imei
- imsi
- phone number
It downloads the following malicious files:
- porn apps
It accesses the following malicious URL(s) to download file(s):
It sends text messages to any of the following premium-rate numbers resulting to unnecessary high phone charges:
- 106566660020
It accesses the following website(s) to send and receive information:
- http://sdk.{BLOCKED}me.com:8880/sdkpay/login
- http://{BLOCKED}t.iread.com.cn:6106/appstore_agent/unistore/servicedata.do?
- http://{BLOCKED}t.iread.com.cn:6106/appstore_agent/getverifycode.do?
- http://{BLOCKED}t.iread.com.cn:6106/appstore_agent/getpassword.do?
- http://{BLOCKED}.{BLOCKED}.196.82:9008/servicedata.do?
- http://{BLOCKED}.{BLOCKED}.227.243:9098/servicedata.do?
- http://{BLOCKED}3rd.iread.com.cn:9055/servicedata.do?
- http://{BLOCKED}.{BLOCKED}.195.14:8089/servicedata.do?
- http://{BLOCKED}d.wo.com.cn/
- http://{BLOCKED}.{BLOCKED}.15.19:8088/servicedata.do?
- http://{BLOCKED}t.iread.com.cn:6106/appstore_agent/unistore/servicedata.do?
- http://{BLOCKED}t.iread.com.cn:6106/appstore_agent/getverifycode.do?
- http://{BLOCKED}t.iread.com.cn:6106/appstore_agent/getpassword.do?
- http://{BLOCKED}.{BLOCKED}.196.82:9008/servicedata.do?
- http://{BLOCKED}.{BLOCKED}.227.243:9098/servicedata.do?
- http://{BLOCKED}3rd.iread.com.cn:9055/servicedata.do?
- http://{BLOCKED}.{BLOCKED}.195.14:8089/servicedata.do?
- http://{BLOCKED}d.wo.com.cn/
- http://{BLOCKED}.{BLOCKED}.15.19:8088/servicedata.do?
- http://{BLOCKED}.{BLOCKED}.4.157:9900/dorecharge3.do
- http://{BLOCKED}.{BLOCKED}.155.254:8080/recharg/itf/getUrlCnf?seriaNo=XX
- http://x.{BLOCKED}o.cn/
- http://{BLOCKED}g.ogengine.com
- http://{BLOCKED}.{BLOCKED}.132.133
It drops and executes the following file(s):
- d_data_wimipay.dat
- LMD.dat
It acts as an SMS relay which receives SMS to be forwarded from a remote URL. As a result, affected users may be charged for sending SMS without their knowledge
It blocks the received SMS, not allowing the user to read the received message.
It displays the following:
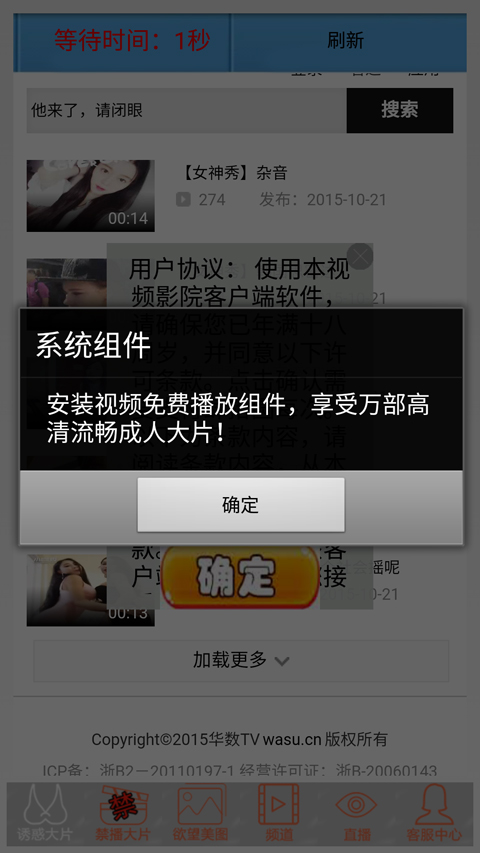
- some porn pictures and videos
Once the app is used, it displays the following screen:
- adds and porn pictures
It arrives as a file downloaded from remote sites offering free download of the following apps:
- some porn apps and 360 browser
It displays pop-up advertisements.
Upon installation, it asks for the following permissions:
- android.permission.ACCESS_ASSISTED_GPS
- android.permission.ACCESS_COARSE_LOCATION
- android.permission.ACCESS_FINE_LOCATION
- android.permission.ACCESS_GPS
- android.permission.ACCESS_LOCATION
- android.permission.ACCESS_MOCK_LOCATION
- android.permission.ACCESS_NETWORK_STATE
- android.permission.ACCESS_WIFI_STATE
- android.permission.BROADCAST_STICKY
- android.permission.CALL_PHONE
- android.permission.CAMERA
- android.permission.CHANGE_CONFIGURATION
- android.permission.CHANGE_NETWORK_STATE
- android.permission.CHANGE_WIFI_STATE
- android.permission.DISABLE_KEYGUARD
- android.permission.FLASHLIGHT
- android.permission.GET_ACCOUNTS
- android.permission.GET_TASKS
- android.permission.INTERACT_ACROSS_USERS_FULL
- android.permission.INTERNET
- android.permission.KILL_BACKGROUND_PROCESSES
- android.permission.MOUNT_UNMOUNT_FILESYSTEMS
- android.permission.READ_CALL_LOG
- android.permission.READ_CONTACTS
- android.permission.READ_EXTERNAL_STORAGE
- android.permission.READ_LOGS
- android.permission.READ_PHONE_STATE
- android.permission.READ_SMS
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.RECEIVE_MMS
- android.permission.RECEIVE_SMS
- android.permission.RECEIVE_WAP_PUSH
- android.permission.REORDER_TASKS
- android.permission.RESTART_PACKAGES
- android.permission.RUN_INSTRUMENTATION
- android.permission.SEND_SMS
- android.permission.SET_PROCESS_FOREGROUND
- android.permission.SIGNAL_PERSISTENT_PROCESSES
- android.permission.SYSTEM_ALERT_WINDOW
- android.permission.VIBRATE
- android.permission.WAKE_LOCK
- android.permission.WRITE_APN_SETTINGS
- android.permission.WRITE_EXTERNAL_STORAGE
- android.permission.WRITE_SETTINGS
- android.permission.WRITE_SMS
- com.anddoes.launcher.permission.READ_SETTINGS
- com.android.launcher.permission.INSTALL_SHORTCUT
- com.android.launcher.permission.READ_SETTINGS
- com.android.launcher.permission.UNINSTALL_SHORTCUT
- com.android.launcher.permission.WRITE_SETTINGS
- com.android.launcher2.permission.READ_SETTINGS
- com.android.launcher3.permission.READ_SETTINGS
- com.android.mylauncher.permission.READ_SETTINGS
- com.ebproductions.android.launcher.permission.READ_SETTINGS
- com.fede.launcher.permission.READ_SETTINGS
- com.htc.launcher.permission.READ_SETTINGS
- com.huawei.android.launcher.permission.READ_SETTINGS
- com.huawei.launcher2.permission.READ_SETTINGS
- com.huawei.launcher3.permission.READ_SETTINGS
- com.lenovo.launcher.permission.READ_SETTINGS
- com.lge.launcher.permission.READ_SETTINGS
- com.oppo.launcher.permission.READ_SETTINGS
- com.qihoo360.launcher.permission.READ_SETTINGS
- com.sec.android.app.twlauncher.settings.READ_SETTINGS
- com.tencent.qqlauncher.permission.READ_SETTINGS
- net.qihoo.launcher.permission.READ_SETTINGS
- org.adw.launcher.permission.READ_SETTINGS
- org.adw.launcher_donut.permission.READ_SETTINGS
- org.adwfreak.launcher.permission.READ_SETTINGS
It uses common file icons to trick a user into thinking that the files are legitimate.
Based on analysis of the codes, it has the following capabilities:
- push unwanted adds
- download unwanted apps
- intercept sms
- silent install shortcut
This is the Trend Micro detection for Android applications bundled with malicious code.
NOTES:
Once the users open it, the app sets the screen luminance to the highest. The app then displays ads, porn pictures, and videos. The app tricks users into thinking that there are security problems with the mobile device and thus need to install patch. In actual, this is a malicious device admin and pushes users to activate it. In effect this pushes ads on the device.
The device admin integrates the assets of the APK. Once you activate the device admin, it locks the screen once users want to deactivate it. The app also downloads unwanted apps from a remote server and creates shortcuts in the desktop. Once users clicked it, it reminds them to install it. If users clicked to see the porn video, the app asks for money and pushes the following malicious pay app, wimipay.
SOLUTION
Step 1
Trend Micro Mobile Security Solution
Trend Micro Mobile Security Personal Edition protects Android and iOS smartphones and tablets from malicious and Trojanized applications. It blocks access to malicious websites, increase device performance, and protects your mobile data. You may download the Trend Micro Mobile Security apps from the following sites:
Step 2
Scan your computer with your Trend Micro product to delete files detected as ANDROIDOS_CURIOUS.HRX. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


