TROJ_SPNR.03CK11
http://about-threats.trendmicro.com/Malware.aspx?language=us&name=TROJ_SPNR.02CT11


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
Trojans or Trojan horse programs refer to a family of malware that carry payloads or other malicious actions that can range from the mildly annoying to the irreparably destructive. They can also contribute to information-stealing attacks by other malware. Trojans may also modify an infected system's settings to automatically execute during startup. Restoring infected systems may require procedures apart from scanning with an antivirus software.
Trojans may be downloaded off the Internet. These may also be dropped by other malware onto systems or may be unknowingly installed by users into their systems.
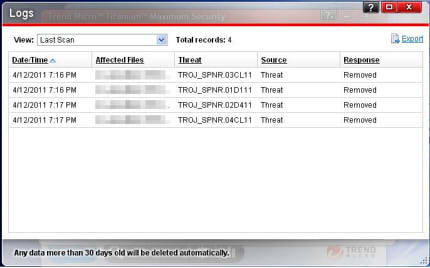
Leveraging the power of the Trend Micro™ Smart Protection Network™, Trend Micro products detect and consequently remove malicious files classified as Trojans if these are found in locations where malware are usually installed and if the files exhibit common malware characteristics.
SOLUTION
NOTES:
For Trend Micro Customers
Scanning your system with your registered Trend Micro security solution removes this malware.
Trend Micro products are powered by the Trend Micro™ Smart Protection Network™, a technology designed to protect you from all kinds of online security threats, regardless of type, attack vector, or behavior.
If you suspect a false positive (i.e. you believe the detected file to be non-malicious), kindly submit a sample of the detected file through the following channels for analysis:For Non-Trend Micro Customers
You may download, install, and scan your system with HouseCall, our highly popular and capable on-demand scanner for identifying and removing viruses, Trojans, worms, unwanted browser plug-ins, and other malware.Did this description help? Tell us how we did.

