Ransomware Spotlight: Cuba
Top affected countries and industries
according to Trend Micro data
This section will examine Cuba ransomware’s attempts to compromise organizations based on Trend Micro™ Smart Protection Network™ country and regional data. Note that these encompass only Trend Micro customers, and do not include a list of all the victims found in Cuba ransomware’s leak site.
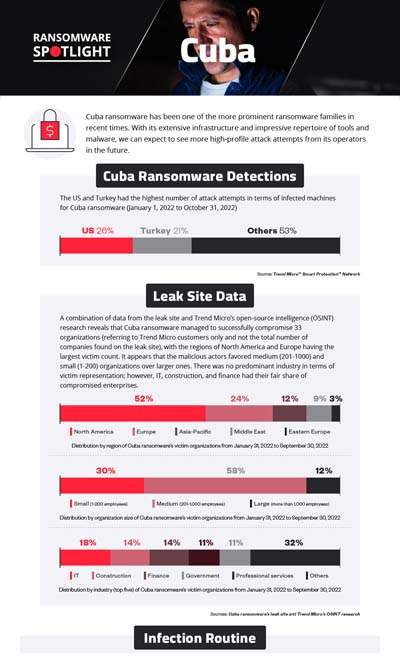
Data shows that Cuba ransomware did not solely focus on Eastern European countries, as the attempts spanned multiple regions. The US and Turkey had the highest number of attack attempts with 26% and 21% of the total, respectively.
Meanwhile, industry data shows that organizations in the healthcare, finance, and consumer sectors had the largest number of Cuba ransomware attack attempts, with the rest split among various other industries that include telecommunications, banking, and manufacturing. Overall, there were 73 companies that were targeted by Cuba ransomware, although the vast majority did not specify the industry that they were involved in.
Targeted regions and industries
according to Cuba ransomware’s leak site
This section examines data based on the attacks recorded on the leak site of Cuba ransomware’s operators. These attacks represent successfully compromised organizations that have refused to pay the ransom demand as of the time of writing.
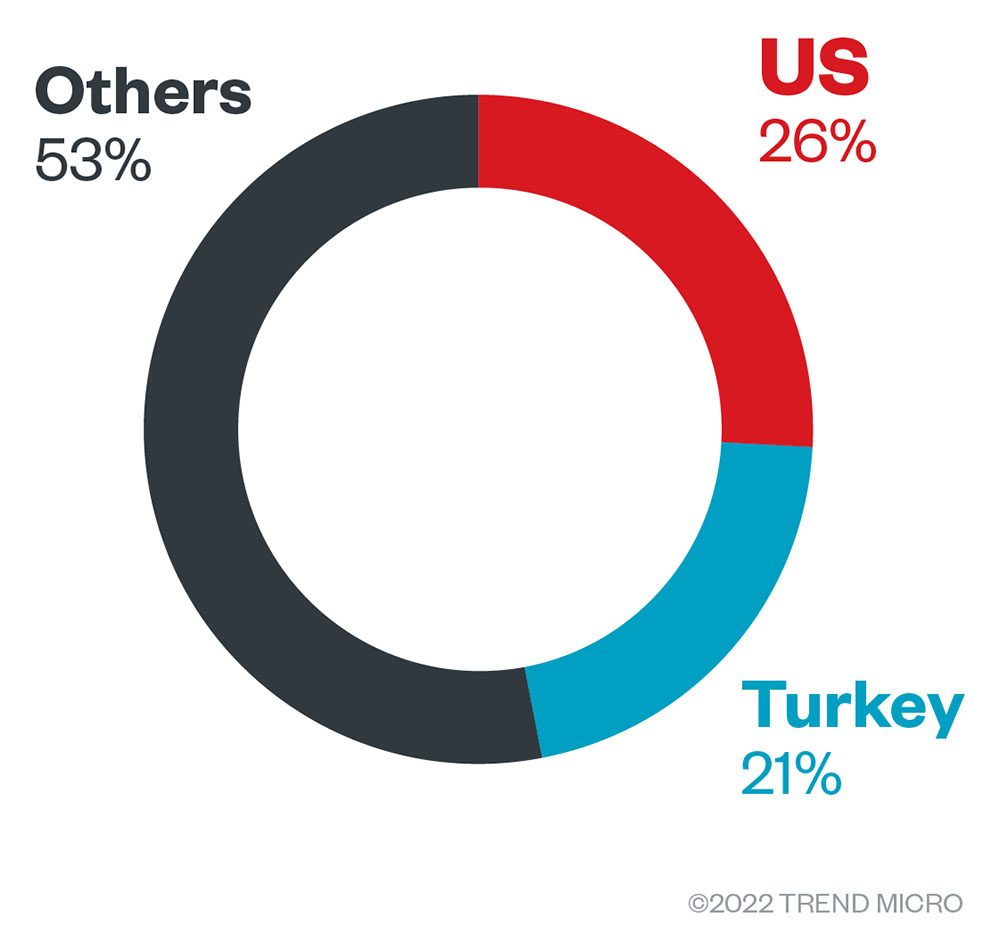
Based on a combination of Trend Micro’s open-source intelligence (OSINT) research and investigation of the leak site, the group managed to compromise a total of 33 organizations. Of these, 17 were operating out of North America, with Europe containing eight organizations, followed by Asia-Pacific with four. Considering that not all organizations that were targeted were in the leak site, this indicates that ransomware groups are not as effective with their attacks as some people might think: the right technological solutions can help prevent a successful attack or infection.
Figure 2. Distribution by region of Cuba ransomware’s victim organizations from January 31, 2022, to September 30, 2022
Source: Cuba ransomware’s leak site and Trend Micro’s OSINT research
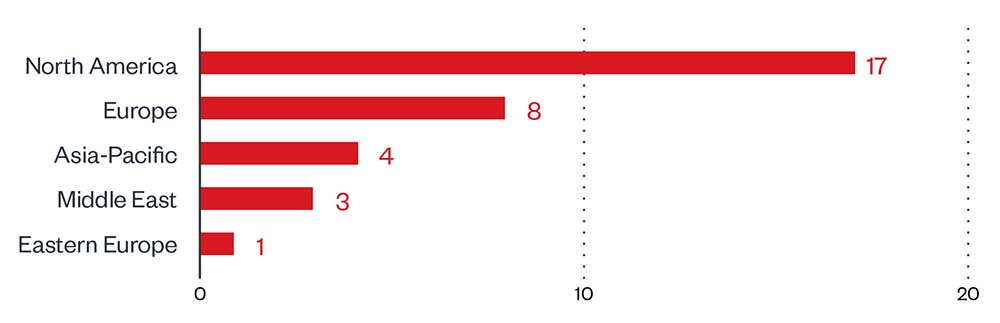
Moving on to specific countries, the US had the highest number of victim companies, with the rest coming from various other countries.
Figure 3. Distribution by country (top ten) of Cuba ransomware’s victim organizations from January 31, 2022, to September 30, 2022
Source: Cuba ransomware’s leak site and Trend Micro’s OSINT research
Cuba ransomware did not seem to favor a specific industry, as the victim organizations did not predominantly come from a single sector. IT services/technology had the highest victim count at five, followed by construction and finance with four each.
Figure 4. Distribution by industry (top ten) of Cuba ransomware’s victim organizations from January 31, 2022, to September 30, 2022
Source: Cuba ransomware’s leak site and Trend Micro’s OSINT research
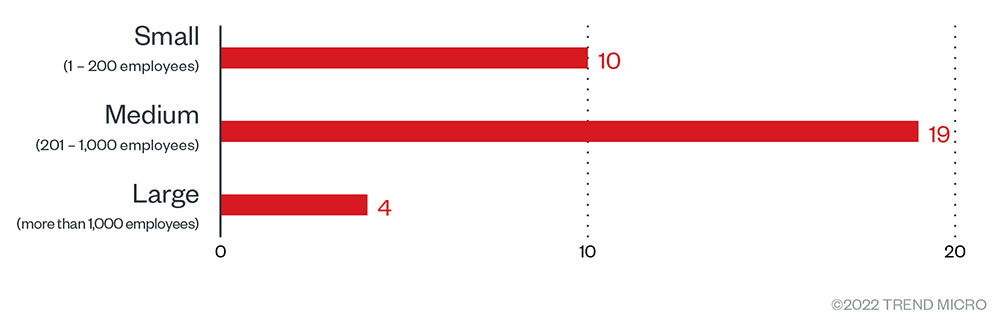
Most of the victims (58%) were medium-sized companies (201-1000 employees), followed by small businesses (30%) of 1-200 employees. Large organizations only accounted for four attacks, or roughly 12% of the total.
Figure 5. The distribution by organization size of Cuba ransomware’s victim organizations from January 31, 2022, to September 30, 2022
Source: Cuba ransomware’s leak site and Trend Micro’s OSINT research
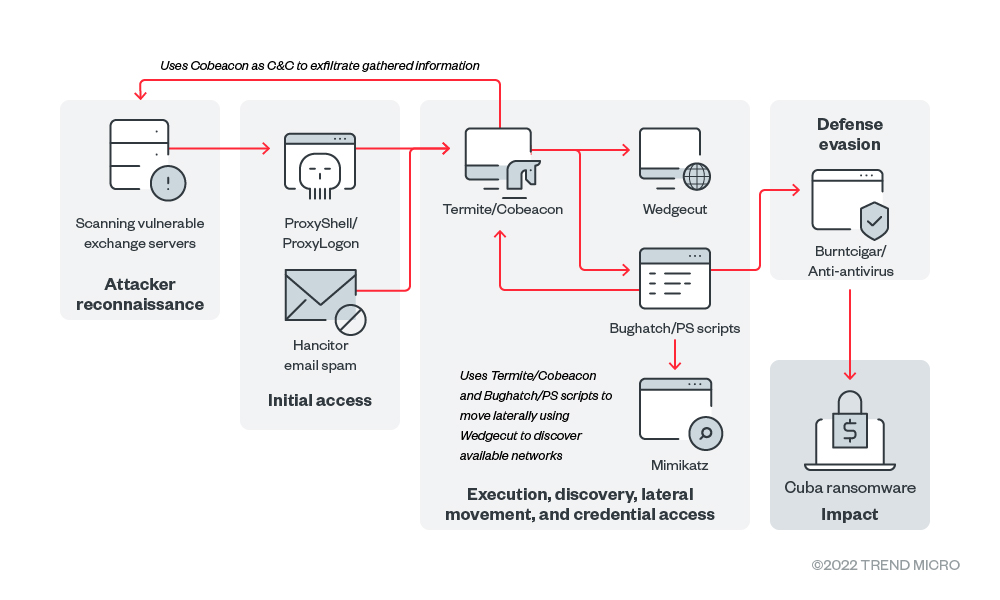
Infection chain and techniques
Initial Access
Cuba ransomware makes use of the ProxyShell (CVE-2021-34473, CVE-2021-34523 , and CVE-2021-31207) ProxyLogon (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065) vulnerabilities to download and execute its component (Termite) which downloads other parts of its routine.
- Reports have mentioned of Cuba ransomware being downloaded by the Hancitor malware via a malicious spam campaign, but this has not been observed internally.
Defense Evasion
- Cuba ransomware will not proceed with its routine if a Russian keyboard layout is detected. Instead, it will terminate and delete itself.
- It uses other components to terminate AV-related processes.
- It uses the KillAV tool to terminate AV-related processes and also makes use of an Avast driver vulnerability ("C:\windows\temp\aswArPot.sys") to terminate services
Discovery
- Cuba ransomware finds, lists, and encrypts files on available connected and shared networks when "-netscan" is provided as an argument upon execution.
- It finds, lists, and encrypts files on connected removable drives when "-net" is provided as an argument upon execution.
- It finds, lists, and encrypts local files when either "-local" or no argument is provided upon execution.
- It makes use of a tool to scan available networks that will be used during its lateral movement phase.
Lateral Movement
- For lateral movement, Cuba ransomware employs a number of tools that include RDP, SMB, and PsExec. It also frequently uses Cobeacon to facilitate movement within the victim networks that were discovered by its network discovery tools
- Following lateral movement, the threat actors deploy various backdoors, including the publicly available NetSupport RAT, Beacon and Bughatch, which are often deployed using the Termite in-memory dropper.
Command and Control
- Cuba ransomware uses its own Cobalt Strike network to communicate back to its command-and-control (C&C) server. It also uses PROXYHTA to communicate with the C&C server to download additional components.
Impact
- The ransomware uses a combination of Salsa and RSA for its encryption algorithm. Furthermore, it employs LibTomCrypt for its cryptography implementations.
- It uses Salsa20 to encrypt files, then makes use of RSA to encrypt the Salsa key to prevent decryption of the encrypted files.
- It checks the file marker FIDEL.CA to determine if the file is already encrypted. If it isn’t, it will prepend the file marker and the encrypted Salsa Key.
- After encryption it will then rename the file and add its extension ".cuba" before dropping a ransom note.
MITRE tactics and techniques
| Initial Access | Execution | Defense Evasion | Credential Access | Discovery | Command and Control | Lateral Movement | Exfiltration | Impact |
|---|---|---|---|---|---|---|---|---|
T1190 - Exploit Public-Facing Application T1566 - Phishing | T0807 - Command-Line Interface T1059 - Command and scripting interpreter | T1480 - Execution Guardrails T1630 - Indicator Removal on Host T1629 - Impair Defenses | T1003 - OS Credential Dumping | T1135 - Network Share Discovery | T1437 - Application Layer Protocol | T0867 - Lateral Tool Transfer | T1041 - Exfiltration Over C2 Channel | T0881 - Service Stop T1471 - Data Encrypted for Impact |
Summary of malware, tools, and exploits used
Security teams should take note of and observe the presence of the following malware tools and exploits that are typically used in Cuba ransomware attacks:
Malware
- Bughatch
- Burntcigar
- Cobeacon
- Colddraw
- Hancitor (Chanitor)
- Termite
- Wedgecut
Tools
- Mimikatz
- PowerShell
- ProxyLogon
- ProxyShell
- PsExec
- Remote Desktop Protocol
| Initial Access | Execution | Defense Evasion | Credential Access | Discovery | Lateral Movement | Exfiltration | Command and Control | Impact |
|---|---|---|---|---|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
| ||||||
|
Recommendations
Given its high level of activity in late 2021 and throughout 2022, we can expect to see more of Cuba ransomware in the future. Its attacks against high-profile targets show that it isn’t hesitant to go after big fish, while its extensive infrastructure and heavy use of other malware and tools in its routine shows that its operators are professional and have high levels of technical knowledge. Although it is still not as well-known as some other existing ransomware families, we encourage organizations to start taking note of Cuba ransomware and how it operates to minimize the chances of a successful attack occurring.
To protect systems against Cuba ransomware and other similar threats, organizations can implement security frameworks that allocate resources systematically to establish a strong defense strategy against ransomware.
Here are some best practices that organizations can consider to help protect themselves from Cuba ransomware infections:
Audit and inventory
- Take an inventory of assets and data.
- Identify authorized and unauthorized devices and software.
- Audit event and incident logs.
Configure and monitor
- Manage hardware and software configurations.
- Grant admin privileges and access only when necessary to an employee’s role.
- Monitor network ports, protocols, and services.
- Activate security configurations on network infrastructure devices such as firewalls and routers.
- Establish a software allowlist that only executes legitimate applications.
Patch and update
- Conduct regular vulnerability assessments.
- Perform patching or virtual patching for operating systems and applications.
- Update software and applications to their latest versions.
Protect and recover
- Implement data protection, back up, and recovery measures.
- Enable multifactor authentication (MFA).
Secure and defend
- Employ sandbox analysis to block malicious emails.
- Deploy the latest versions of security solutions to all layers of the system, including email, endpoint, web, and network.
- Discover early signs of an attack such as the presence of suspicious tools in the system.
- Use advanced detection technologies such as those powered by AI and machine learning.
Train and test
- Regularly train and assess employees on security skills.
- Conduct red-team exercises and penetration tests.
A multilayered approach can help organizations guard possible entry points into their system (endpoint, email, web, and network). Security solutions can detect malicious components and suspicious behavior, which can help protect enterprises.
- Trend Micro Vision One™ provides multilayered protection and behavior detection, which helps block questionable behavior and tools early on before the ransomware can do irreversible damage to the system.
- Trend Micro Cloud One™ Workload Security protects systems against both known and unknown threats that exploit vulnerabilities. This protection is made possible through techniques such as virtual patching and machine learning.
- Trend Micro™ Deep Discovery™ Email Inspector employs custom sandboxing and advanced analysis techniques to effectively block malicious emails, including phishing emails that can serve as entry points for ransomware.
- Trend Micro Apex One™ offers next-level automated threat detection and response against advanced concerns such as fileless threats and ransomware, ensuring the protection of endpoints.
Indicators of Compromise (IOCs)
The IOCs for this article can be found here. Actual indicators might vary per attack.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.


 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks