Uncovering IoT Threats in the Cybercrime Underground
Amid the growth of the internet of things (IoT), manufacturers and integrators are testing the limits of how the technology can be applied, as seen in how new forms of connected devices are hitting the market. Some applications play critical roles in industries while others provide more convenience for consumers. The wide spectrum of IoT applications only highlights further the importance of security in everything that is IoT. After all, this technology sparks the imagination of not only integrators but also of cybercriminals.
What form does cybercriminal interest in the IoT take? We uncover some answers by looking at the cybercriminal underground in our research paper "The Internet of Things in the Cybercrime Underground," where we detail what we found in Russian, Portuguese, English, Arabic, and Spanish underground communities.
News and research
Cybercriminals like to keep abreast of the latest findings in the realm of the IoT, likely to survey for openings for possible attacks. This is evidenced by forums across different cybercriminal underground communities discussing IoT-related news and research, as seen in the image.
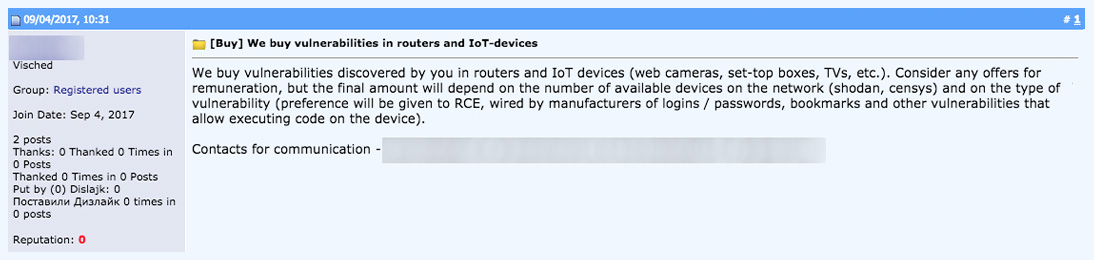
Tutorials
A more direct approach to gaining information about attacks are tutorials. We saw several posts on tutorials and tutorial requests about how to exploit vulnerabilities, hack into devices, and use upcoming ones.
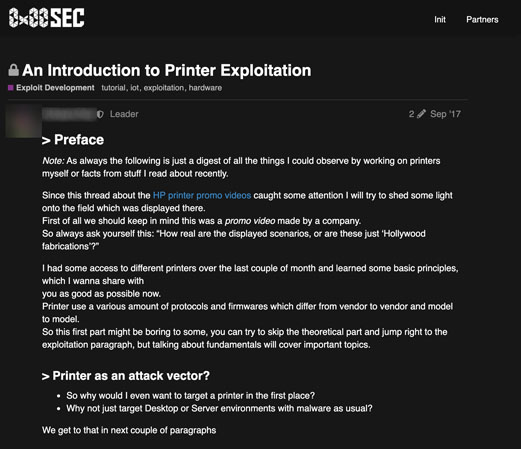
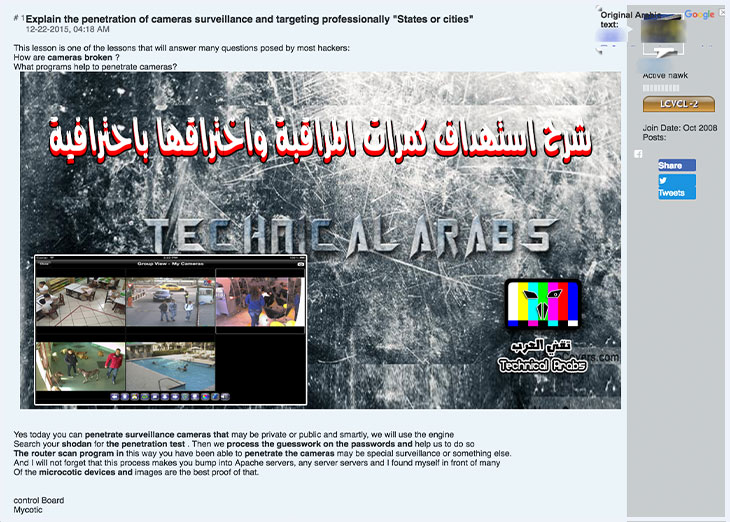
Devices
Things, i.e., connected devices, were predictably a large part of the underground discussions. Aside from tutorials, access rights to hacked devices were being sold in some underground communities. Routers and IP cameras were the most prominently discussed devices.
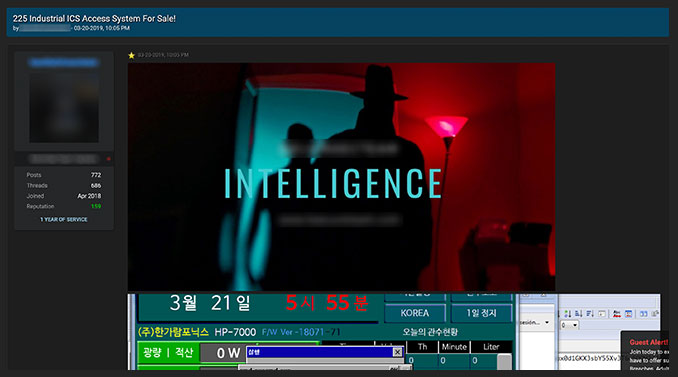
Industrial equipment and systems
Equipment and systems used in industrial settings were also of interest to the different underground communities. The discussions ranged from advertisements selling access to industrial control systems and software for supervisory control and data acquisition (SCADA) systems to a market for modified gas pumps.
Botnets
The IoT lends itself well to botnet attacks, what with its use of multiple online devices. This is reflected in the forums, as botnets were also a key topic across several cybercriminal underground communities. Notably, sharing of Mirai modifications was rampant, at least for the English-speaking underground community.
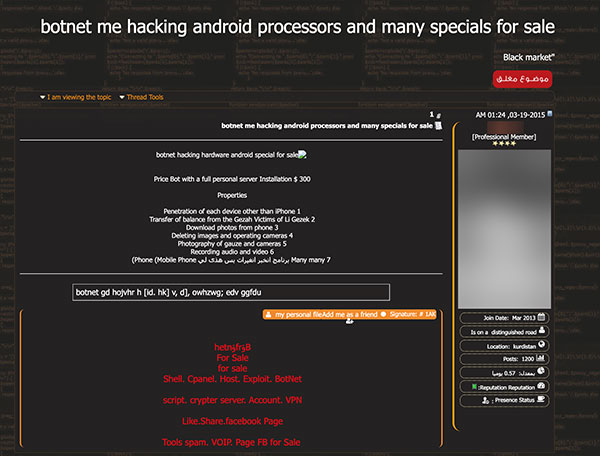
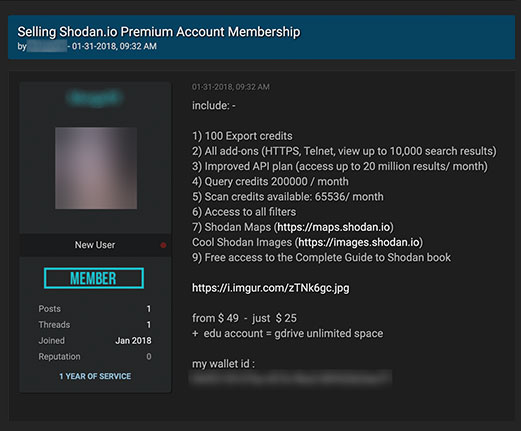
Shodan
Shodan, the search engine for online devices and equipment, came up as a topic in several underground communities. Discussions about Shodan included tutorials for automating searches, Shodan accounts for sale, and even a program that shows canned Shodan searches for several devices.
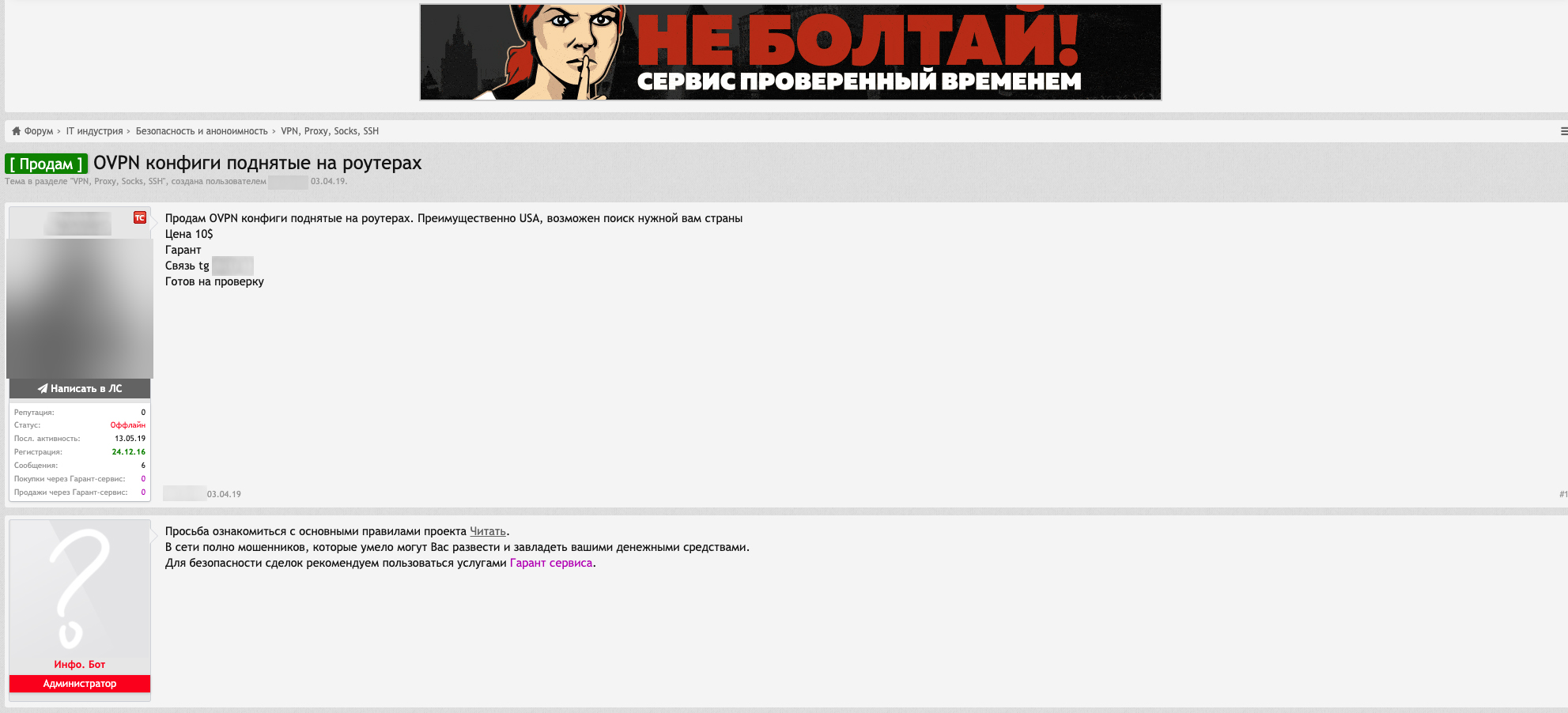
Unique topics
Several underground communities offer unique services and programs for sale. These include IoT-based virtual private networks (VPNs) and distributed denial of service (DDoS) and DNS services.
Although the level and structure of monetization for IoT attacks and threats vary across communities, our findings prove that cybercriminals have a definite and diverse interest in IoT-related opportunities. They scope what the IoT has to offer them as well as future possibilities once new devices hit the market. Above ground, this interest from malicious groups should be countered with an equally — if not more — keen attention on IoT security.
Read our paper, “The Internet of Things in the Cybercrime Underground,” where our findings are further discussed in the context of each underground community.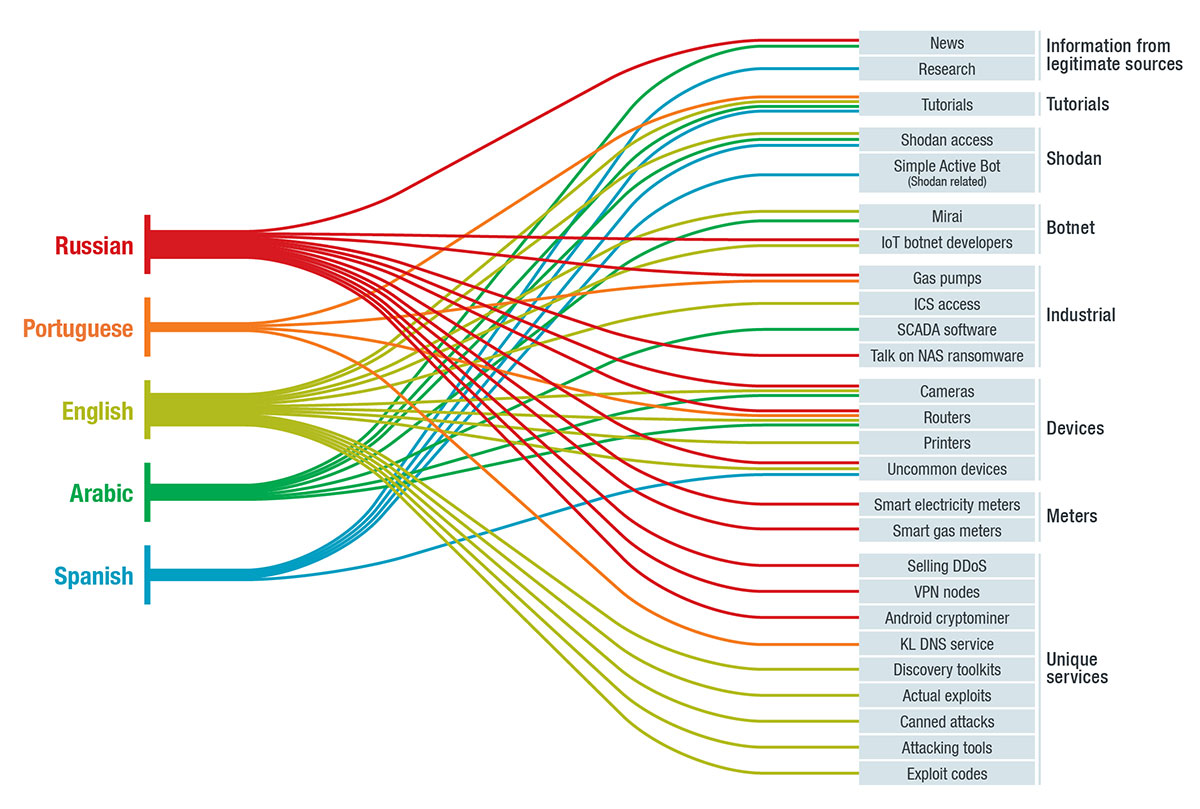
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Unveiling AI Agent Vulnerabilities Part II: Code Execution
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report

 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks