HKTL_DUMPSEC
[Microsoft] HackTool:Win32/Dumpsec.A; [Sophos] Mal/Agent-SK;
Windows 2000, Windows XP, Windows Server 2003


Threat Type: Hacking Tool
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This hacking tool may be manually installed by a user.
It is a command line program that may be used to perform certain routines.
TECHNICAL DETAILS
Arrival Details
This hacking tool may be manually installed by a user.
Backdoor Routine
This hacking tool is a command line program that may be used to perform certain routines.
NOTES:
Other Details
Based on analysis of the codes, it has the following capabilities:
- Dump LSA information
- Dump Microsoft Wireless connections
- Dump active logon sessions
- Dump Windows Sam database
- Dump cached domain credentials
This malware is used as a hacktool with the following options:
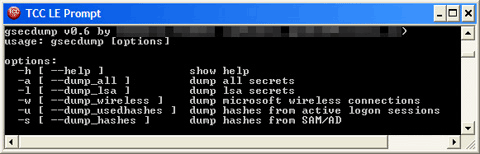
Using this hacktool, the user can dump the system passwords and keys stored in the system. This allows the user to use the acquired password or keys to have access into the system.
SOLUTION
Step 1
For Windows XP and Windows Server 2003 users, before doing any scans, please make sure you disable System Restore to allow full scanning of your computer.
Step 2
Scan your computer with your Trend Micro product to delete files detected as HKTL_DUMPSEC. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


