For enterprises, staying competitive in an ever-changing market involves keeping up with the latest technological trends. However, without the parallel development of security infrastructure and robust response, these technologies could be used as a conduit for cyberthreats that result in losses.
The reality of data breaches
According to a study done by IBM and Ponemon, a data breach costs an average of US$3.92 million. For organizations, this cost can vary depending on how quickly they discover and respond to a breach.
The 2020 Data Breach Investigations Report published by Verizon found that while most of the data breaches in 2019 lasted only days or less, a quarter of the cases lasted months or more. Containment averages also lasted around the same amount of time, with most breaches being contained within days or less.
Overall, the numbers in the report show an improvement in data breach discovery and response compared to previous years. However, the report noted that the apparent improvement could be reflective of the inclusion of more breaches detected by managed security service providers (MSSPs) in their sampling.
Organizations should aim to prevent these breaches from happening; however, preparing for such incidents and having protocols for reducing a breach lifecycle is an essential and realistic approach for dealing with current threats.
Preparing for Threats
Knowing what enterprises are up against is the first step in preparing for and responding to potential cyberattacks. In the past, threats were much simpler, largely defined by the technologies they exploited. Now that enterprises lean on more advanced network and data infrastructures, the attack surface and impact of threats have grown.
Trend Micro’s review of the 2019 threat landscape shows the complexity and persistence of current threats, with cybercriminals employing strategies that take advantage of industry trends and popular platforms.
Ransomware attacks have started to focus more on high-profile targets and less on developing new families, as evidenced by the decrease in new ransomware families in 2019. Based on our detections of ransomware-related threats, the number of new ransomware families in 2019 (95) was fewer than half of the corresponding count in 2018 (222).
Phishing-related activity also decreased. However, these detections doubled (from 65,702 to 131,757) in the case of Microsoft 365, specifically Outlook. This trend reflects how the widespread use of Microsoft 365 by enterprises could have enticed scammers to target the software suite.
2019 was also marked by a number of notable attacks on e-commerce sites as Magecart Group 12 and FIN6 infected thousands of online shops to steal customer credit information.
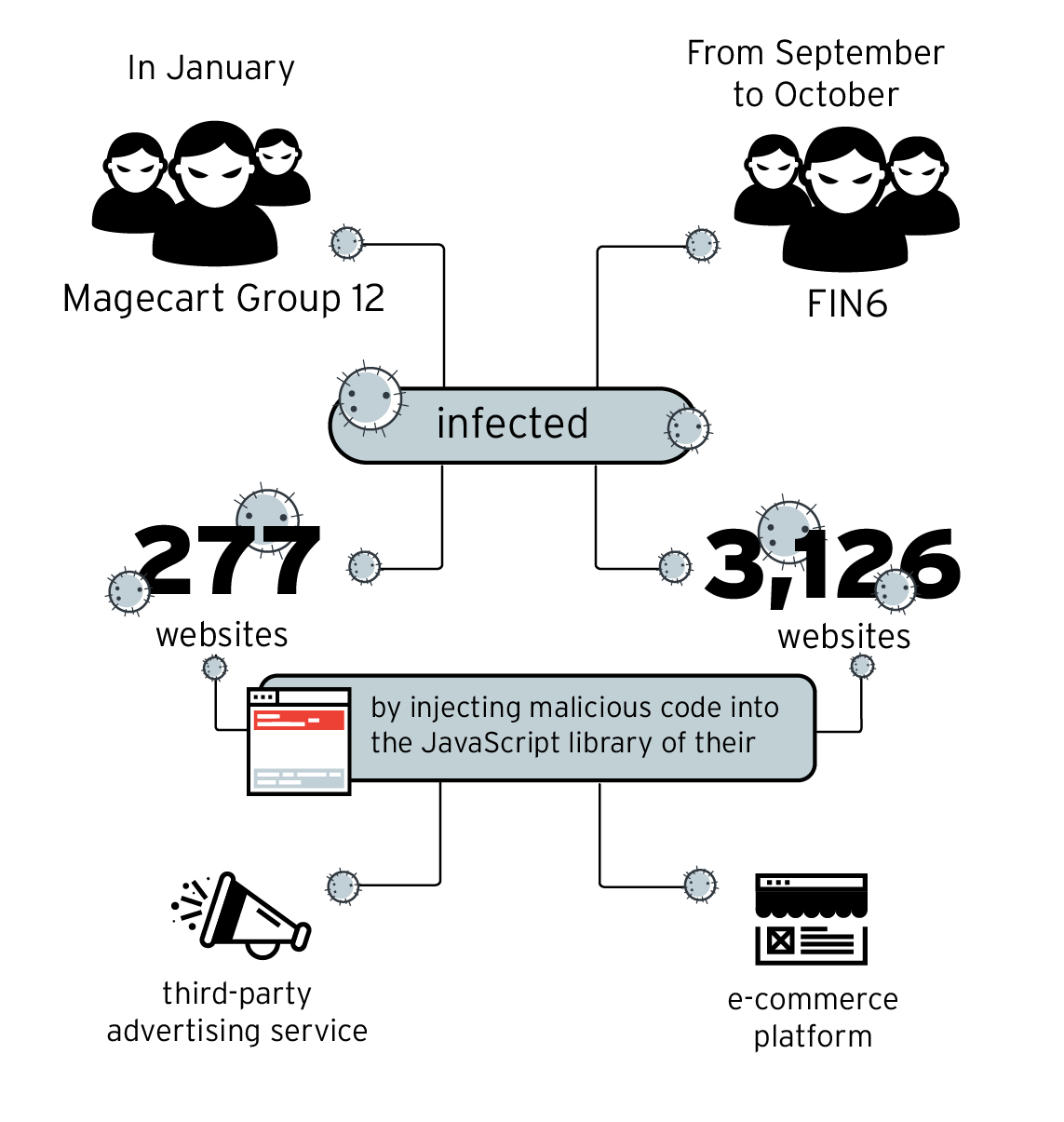
Figure 1: E-commerce site compromise campaigns perpetrated by Magecart Group 12 and FIN6 in 2019
The threats above highlight the security gaps in technologies used today. These also demonstrate how trends and weaknesses of industries, devices, or platforms shape the attack landscape.
Organizations have a lot of bases to cover as they adopt new applications and software to improve operations and drive innovation. Aside from gaining familiarity with current threats, personnel should also get a firm grasp of all the technologies used by their organization.
While multilayered protection can help in detecting and preventing cyberattacks from breaching defenses, all personnel in charge of maintaining corporate infrastructure should also be equipped with knowledge on how to respond to a discovered breach and active attack.
[Read: Dynamic challenges to threat detection and endpoint security, and how to overcome them]
Incident Response
Threats like these attacking enterprise defenses necessitate an effective incident response strategy. Incident response is the process or that plan organizations use as a guide for managing and mitigating breaches or cyberattacks.
The end goal of incident response is to get the business running again after an attack. This involves identifying and qualifying the threat that breached their defenses. An incident also implies that the organization’s preventive mechanisms have failed and need to be reinforced.
A distinctive characteristic of incident response is that it can be successful without having to identify the threat actor behind the attack. Incident response happens “live,” or during an ongoing attack, with the intention of putting a stop to it. In contrast, something like computer forensics happens after the fact and has the luxury to go more in-depth because the threat has abated.
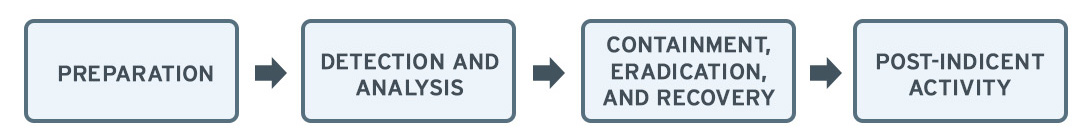
Two incident response frameworks have been widely accepted as the standard: the NIST (National Institute of Standards and Technology) and SANS (SysAdmin, Audit, Network, and Security). These frameworks closely resemble each other and cover a broad base, from preparing for an attack to making sure an incident is not repeated.
THE PLAYBOOK
The playbook introduced here is derived from the two frameworks and should help those who are new to incident response with its overall goal and process. These steps are followed on the premise that an organization has detected an attack or a breach. However, as seen in both frameworks, preparing for breaches and threats is an equally important aspect of incident response.
Preparation
Preparation involves the development of policies and protocols to follow in the face of an attack. These protocols must also involve mapping out the people and entities to inform in case of a breach.
This step includes the formation of a dedicated response team that would lead the mitigation efforts during the attack, as well as training and assigning responsibilities to those who are not part of this team if such an incident were to involve them.
Detection, Identification, and Analysis
This set of steps necessitate the right threat detection and intelligence tools to monitor endpoints, network traffic, and other data sources. Following these steps should give responders a thorough estimate of the situation, which would be the basis for further actions to take, and who to involve in its response.
Alert and report to stakeholders.
As mentioned earlier, preparation procedures involve identifying who to inform or involve when an incident takes place. These include the company response team, executives, and government or law enforcement groups assigned for such an incident. Depending on the extent of the breach, customers should also be informed, as per the guidelines set by data protection regulations.
- Provide daily war room style updates to all stakeholders on the hourly progress of the containment effort.
- View and treat the incident in a broader lens. It is not only an IT matter, but also a legal and compliance concern.
- Adhere to the breach notification requirements of data protection laws.
TIPS:
Augment your staff with a Managed Detection and Response service, as handling detections from multiple sources can be a time-consuming task that can overburden IT teams and require cybersecurity skills that are difficult to find.
Perform root-cause analysis.
Begin the process of finding out the cause of the attack and the conditions that allowed it to happen.
- If you do not have an endpoint detection and response (EDR) module enabled on your endpoint security agent, download free tools such as Trend Micro Anti-Threat Toolkit (ATTK) to identify the cause and conditions.
- Since EDR cannot give the full picture, consider using cross-layer detection and response (XDR) platforms. A network breach detection system will help you discover unmanaged endpoints that are used as infection points, which EDR would not be able to discover. Email telemetry, EDR, and network detection — which are tools used in XDR platforms — would connect all the dots.
- Identify the type of threats and tactics that the cybercrime used. This process includes documentation and footprinting. Take note of reconnaissance scans, network scans, vulnerability exploits, hacking tools, malware, and social engineering techniques.
TIPS:
Use an out of band network breach detection system to scan all network traffic (ingress/egress and east-west) to identify other indicators of compromise on your network.
Assess the impact.
The organization must be able to estimate the affected areas before planning for further remediation tactics.
- Run tools that can identify other systems that have been affected.
- Correlate logs from various system such as the firewall, intrusion prevention system (IPS), out of band network breach detection systems, domain name system (DNS), active directory (AD), and other security events
TIPS:
Ensure that your endpoint security agent is equipped with an endpoint detection and response module (EDR) or cross layer detection and response (XDR).
Security information and event management (SIEM) is a tool that can be used to correlate logs, but this requires proper staffing and triaging.
Containment, Eradication, and Recovery
The goal of these next few steps is to minimize the impact of the incident or breach. This involves isolating the threat, removing it from the affected system, and repairing the damage it has caused.
Isolate.
The affected systems should be isolated from the network via network access control. Isolation does not mean powering off the system, as forensic artifacts — which need to be extracted for further investigation — may still be in volatile memory. If the attack is severely impacting operations, isolate the network from the internet.
Eradicate.
This step involves the removal of the threat from the system and transferring further analysis to security professionals or a security vendor.
- Remove the threat.
- Submit the threat to a security vendor for bandage and signature update.
- Use the bandage signature update provided by the security vendor that helps clean up previously undetected threats and do a full scan of all network endpoints.
Remediate.
With the threat removed, begin the remediation process to fix whatever problems or disruptions the attack had left.
- Start with critical applications that impact business operations.
- Use tools or services that analyze industrial internet of things (IIoT) settings involving industrial control systems (ICS) and other system vulnerabilities.
- Make use of pentesting services.
- Apply patches and perform hardening, system cleanup, or reimaging.
Lessons Learned or Post Incident
Once the incident and all its effects have been dealt with, examine the circumstances that allowed the incident to happen. Observations and lessons from this step can be used to strengthen the overall incident response process of the organization. This step links back to the preparation phase at the beginning of this playbook.
Review security best practices.
Take the opportunity to review the security best practices to prevent similar breaches.
- Follow recommendations provided by the security vendor or professionals. If they pointed out that a security tool was not configured optimally, then configure settings according to best practices.
- Review defenses in-depth and ensure these layers are adequately secured:
- Review security policies such as those for access control, remote access, firewall management, network connection, password policy, user account policies, information protection and data classification, email security, and acceptable use policies
- Review risk management processes to mitigate risk and identify acceptable risks
- Share final report to stakeholders
TIPS:
Proactively reach out to your vendor now to assist you with this before an incident occurs.
Trend Micro XDR and Managed XDR
Organizations can also benefit from advanced Trend Micro solutions that can proactively protect IT environments from a wide range of cybersecurity threats. The Trend MicroTM XDR solution effectively protects connected emails, endpoints, servers, cloud workloads, and networks. Trend Micro XDR uses powerful AI and expert security analytics to correlate data, as well as deliver fewer yet higher-fidelity alerts for early threat detection. In a single console, it provides a broader perspective of enterprise systems and shows a more focused and optimized set of alerts. This provides IT security teams with better context for identifying threats faster and understanding and remediating impact more effectively.
Meanwhile, Trend Micro Managed XDR provides expert threat monitoring, correlation, and analysis from skilled and seasoned Managed Detection and Response analysts. Managed XDR is a flexible 24/7 service that provides organizations with one single source of detection, analysis, and response. These three are necessary steps that fit into the playbook and frameworks discussed above. Analyst expertise is also enhanced by Trend Micro solutions that are optimized by AI and enriched by global threat intelligence. The Managed XDR service allows organizations to expand with the cloud without sacrificing security or overburdening IT teams.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.


 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks