Earth Baku Returns: Uncovering the Upgraded Toolset Behind the APT Group’s New Cyberespionage Campaign
 Download Earth Baku: An APT Group Targeting Indo-Pacific Countries With New Stealth Loaders and Backdoor
Download Earth Baku: An APT Group Targeting Indo-Pacific Countries With New Stealth Loaders and Backdoor
Last year, we began studying new malware tools that surfaced as part of a cyberespionage campaign, which Earth Baku — a notorious advanced persistent threat (APT) group, better known as APT41 — had carried out against organizations in the Indo-Pacific region. While we have yet to determine the exact motives behind Earth Baku’s operations, we share our key findings from our analysis with a view to encouraging further research into this active campaign.
Victim profile
For this campaign, Earth Baku has leveled its attacks against entities in the airline, computer hardware, automotive, infrastructure, publishing, media, and IT industries. According to our detections, these organizations are located in the Indo-Pacific region. So far, we have registered hits in India, Indonesia, Malaysia, the Philippines, Taiwan, and Vietnam.
Figure 1. Countries affected by Earth Baku’s campaign, all in the Indo-Pacific region
Source: Trend Micro™ Smart Protection Network™ infrastructure
New tools
Our analysis indicates that Earth Baku employs previously unidentified pieces of malware in this campaign: two shellcode loaders, which we have named StealthVector and StealthMutant, and a backdoor, which we have dubbed ScrambleCross.
The loaders: StealthVector and StealthMutant
StealthVector, a shellcode loader written in C/C++, has various configurable features that malicious actors can easily implement without changing its source code. It can be configured to uninstall itself, run its payload in a specific location, avoid detection by disabling Event Tracing for Windows (ETW), and perform username checking for context awareness. StealthVector’s configuration is difficult to decrypt because the loader is encrypted with the ChaCha20 routine and a fixed custom initial counter.
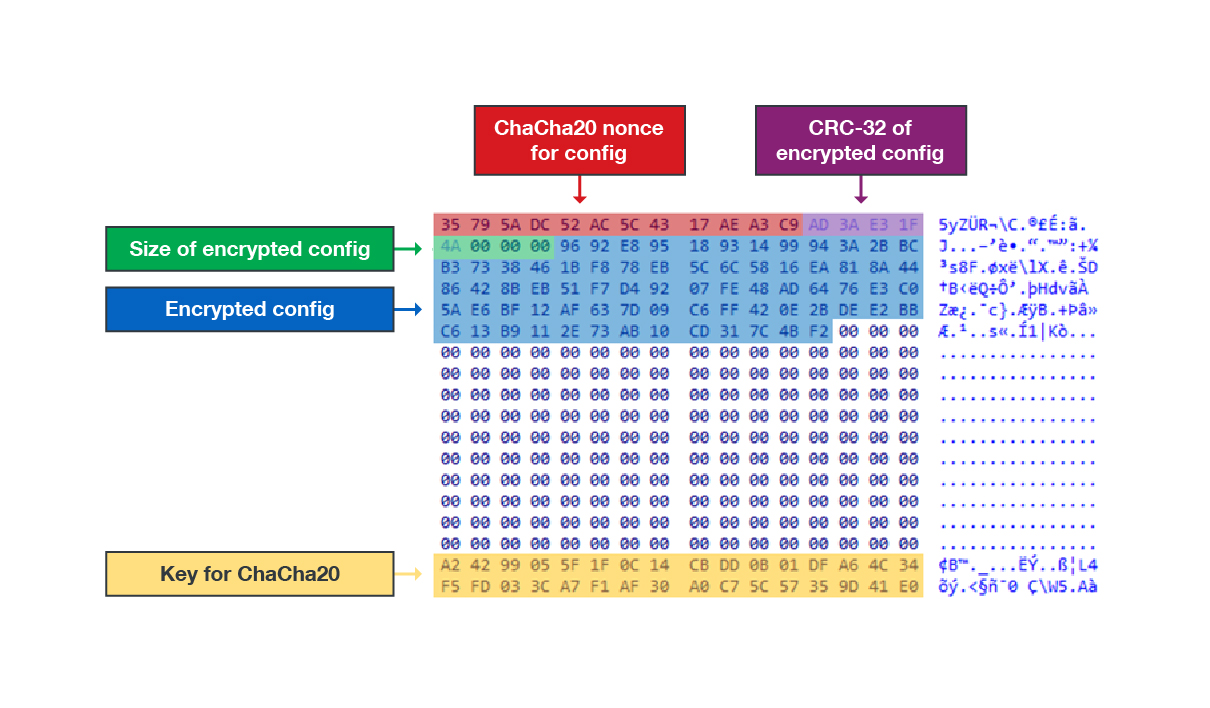
Figure 2. The locations of StealthVector’s encrypted configuration and ChaCha20 key information
StealthMutant, a C# implementation of StealthVector, executes its payload by performing process hollowing, a technique widely used by both malicious actors and red teams. Like StealthVector, StealthMutant can disable ETW and go undetected by Windows’ built-in logging system. Most of the StealthMutant samples we have observed use AES-256-ECB to decrypt their payloads, but we have also found older versions of this loader that use XOR instead.
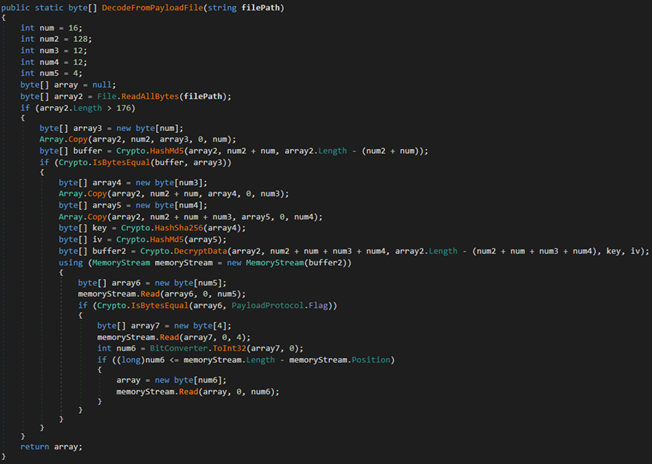
Figure 3. A StealthMutant sample that uses AES-256-ECB for decryption
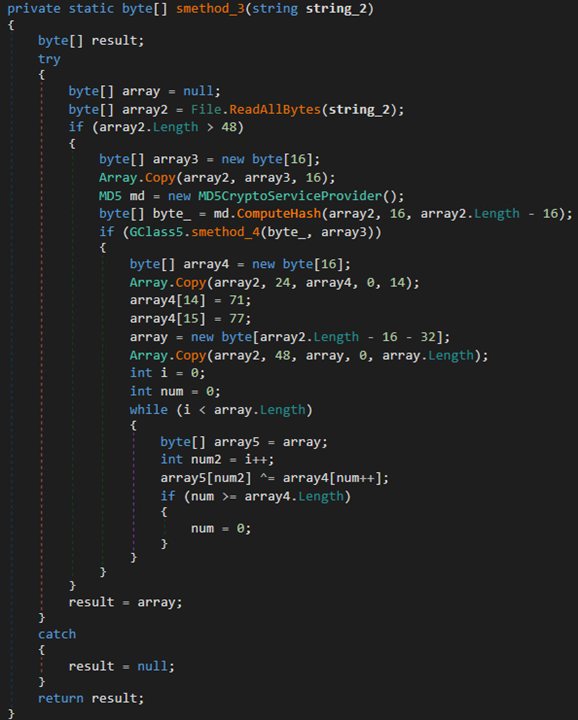
Figure 4. A sample of an older StealthMutant version that uses XOR for decryption
The payloads: ScrambleCross and Cobalt Strike beacon
A shellcode-based backdoor, ScrambleCross is one of the two kinds of payloads found in StealthMutant and StealthVector samples, the other being the Cobalt Strike beacon. ScrambleCross fields backdoor commands to and from its command-and-control (C&C) server, enabling it to receive and then manipulate plug-ins. Because we have yet to retrieve any plug-ins from its C&C server, we have not ascertained the full extent of ScrambleCross’ plug-in manipulation capabilities.
Attack vectors
This campaign uses different means to enter and infect a target system:
- Injection of an SQL script into the system’s Microsoft SQL Server to upload a malicious file
- Exploitation of the Microsoft Exchange Server ProxyLogon vulnerability CVE-2021-26855 to upload a malicious web shell
- Possible distribution through emails containing malicious attachments
- Use of the installer application InstallUtil.exe in a scheduled task
Attribution
This campaign is tied to one of Earth Baku’s earlier cyberespionage campaigns, which the group is perpetrating under the alias APT41. This older campaign has been ongoing since November 2018 and uses a different shellcode loader, which we have named LavagokLdr, but these two campaigns are alike in many ways.
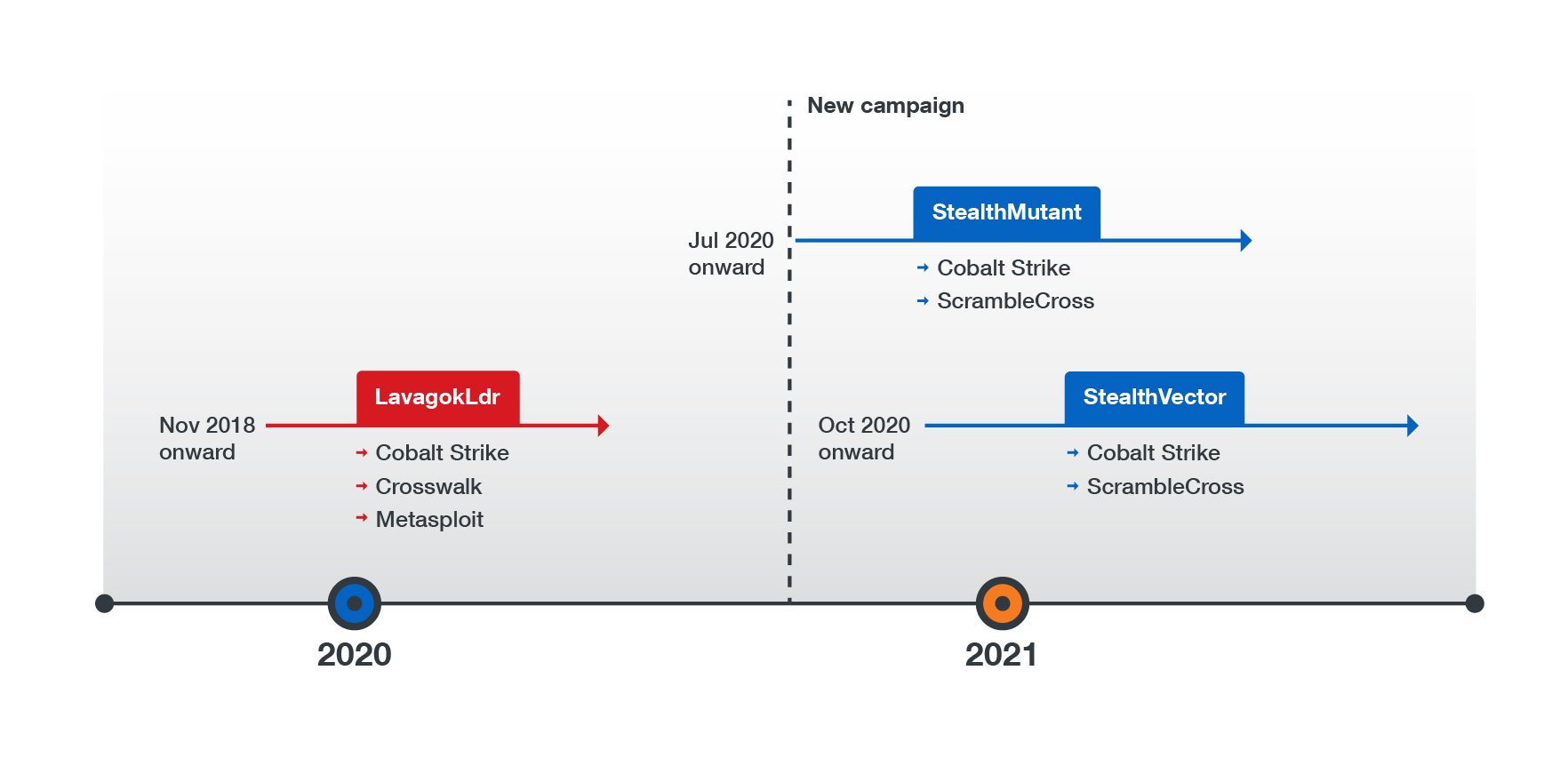
Figure 5. A timeline of Earth Baku’s previous campaign and its new campaign
We have attributed this new campaign to Earth Baku on the basis of its code similarities to the other campaign:
- Both campaigns use the installer script called install.bat.
- Their shellcode loaders have the same kind of dynamic link library (DLL), Storesyncsvc.dll, and similar procedures for loading APIs.
- Their payloads perform similar processes for signature checking and decoding their main functions.
Skilled actors, upgraded tools
Our analysis of StealthMutant, StealthVector, and ScrambleCross demonstrates that Earth Baku has improved its malware tools since its last campaign. This suggests that the group’s members specialize in different areas, including low-level programming, software development, and techniques used by red teams. While we have yet to ascertain Earth Baku’s motives behind this campaign, the group has designed these sophisticated new tools to be easily modified and to avoid detection more efficiently when infiltrating a targeted network.
Our research paper “Earth Baku: An APT Group Targeting Indo-Pacific Countries With New Stealth Loaders and Backdoor” sheds more light on Earth Baku’s operations in general and the capabilities of its new pieces of malware in particular. It also provides security recommendations that can help organizations protect their networks from campaigns like Earth Baku’s.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks