Automated teller machine (ATM) malware was not as common when Trend Micro started to analyze samples in 2015. The fact that some criminal gangs in South America and Russia had studied how these machines work and made special software to attack them was remarkable at the time. ATMs are unlike the usual Windows environments, so an attacker would need knowledge on a special set of application programming interfaces (APIs) and how they interact with specific bank applications.
Since our first collaboration with Europol’s European Cybercrime Centre (EC3) where we explained the different cyberthreats targeting ATMs, we observed the ATM malware landscape evolving toward network-based attacks. We published a second paper detailing this evolution and the ATM malware families that emerged over the years.
[READ RESEARCH: Cashing in on ATM Malware: A Comprehensive Look at Various Attack Types]
We have seen a lot of shifts in the ATM malware field, but the most important one is not technical: ATM malware has become a common feature in the cybercriminal underground and is now being offered as part of attackers’ arsenal for stealing cash. ATM malware has become a commodity, and any criminal with US$1,000 to invest can start attacking ATMs in no time.
Notably, these criminal offerings are coming from the Russian-speaking criminal underground. This is not to say that South American gangs have stopped attacking ATMs in their region, but that the Russian criminal undergroundhas a more dynamic, thriving marketplace, where all kinds of illicit transactions are more likely to happen.
[RELATED: Revisiting the Russian Cybercriminal Underground]
ATM Malware 101: Criminal Advice and Help Online
Cybercriminal offerings usually include more than the malware. Often, these underground sellers provide instructions, practical bits of advice, and troubleshooting guides.
As an example, one of the most publicized ATM malware offerings, the so-called “Cutlet Maker,” had a concrete description of the hardware needed to pull off a successful heist, as well as detailed step-by-step instructions for using the program.

Part of the Cutlet Maker package: a description of the ATM brand and model to target, as well as the equipment needed to attack it
Along with this “user manual” of sorts, the seller shares his own troubleshooting advice on how to make the software work in different environments. Here is an English translation of the introduction for this guide:
“The original and the second manual outline all the information that is needed for it to work. Tav really has it all. In this manual, there will be only information on how to get around the difficulties that may arise. Here I will present my own experience.”
We can't be sure if “Tav” is the original author of the malware or the manual, or the internal name of this malware. The document’s metadata identifies the manual's author as “Bogdan.”
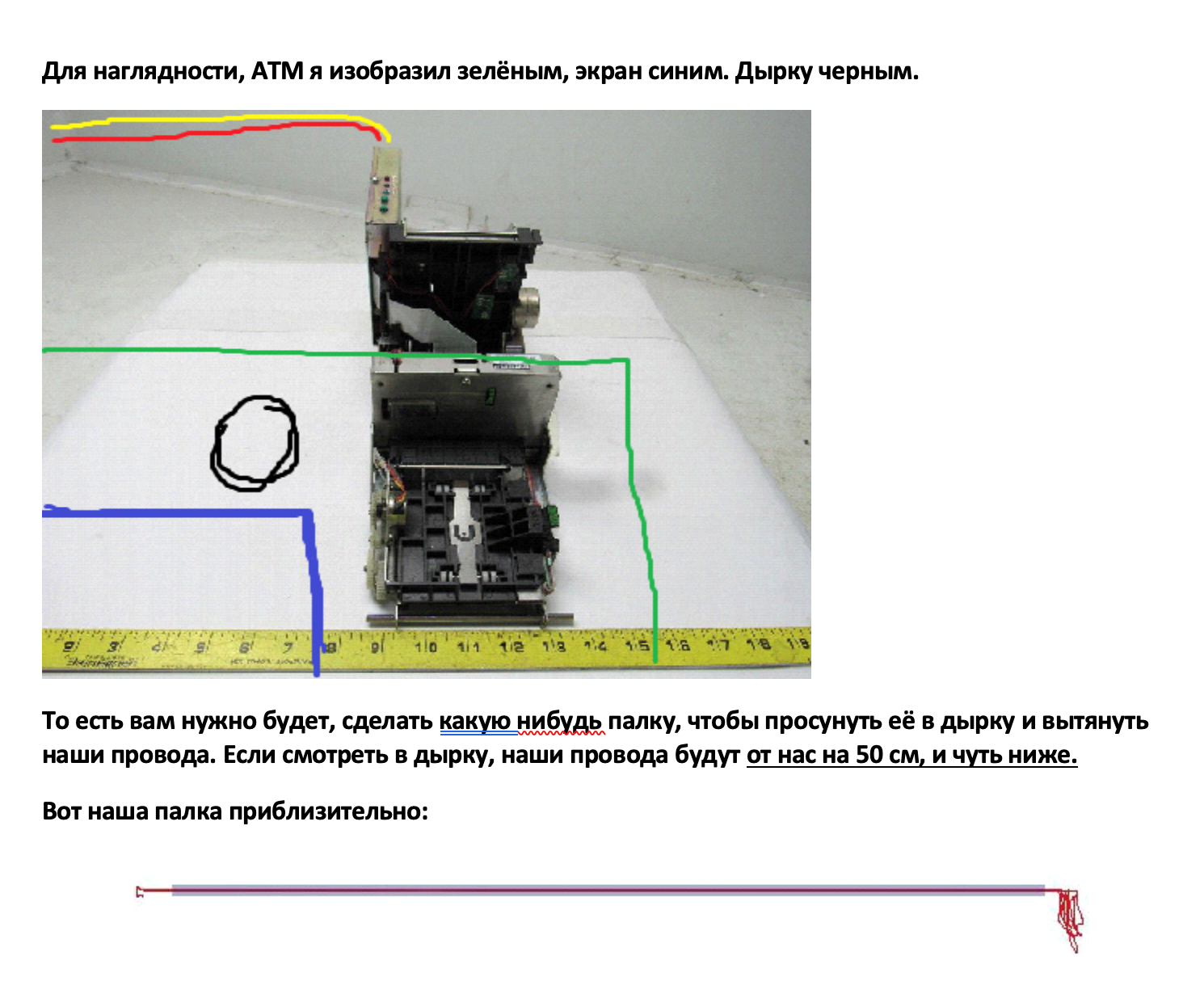
Screenshot of the troubleshooting guide for Cutlet Maker. The author describes the ATM's USB port location, along with advice on how to devise a stick for attaching the USB cable and accessing the internal USB port
[RELATED READ: Dissecting PRILEX and CUTLET MAKER ATM Malware Families]
The included guide describes the target ATM's external and internal details. This is a translation of the advice from the criminal seller:
“The ports we need are located behind the plastic canopy, which is above the ATM screen, followed quite often by the bank's advertising paper. This cover keeps on three clips, they are located in the upper part of the plastic – on the left, in the middle, and on the right. Pry the knife gently so that this cover does not break, put it on top of the ATM so as to not interfere further. We take out a flashlight, shine and see the following:”

The author describes what the attacker will see once the panel that uncovers the internal USB port is removed
Some of the advice also includes mobile phone usage and how doing it incorrectly can allow law enforcement to track the attacker.
However, not all of the advice found on these criminal guides are purely physical. There is, for instance, an explanation on how to disable an installed antivirus program, if the machine is protected by one:
“Adobe services are disabled here. We do the same with our antivirus. Next, go to the Startup tab, remove the checkmarks from our antivirus. Then, apply and proceed. Next, go to the antivirus folder C:/Program.../Our antivirus/ and change the name of the .exe: For example, from kvp.avp.exe to any other.
You have turned off the antivirus, now you can run our malware from a flash drive.”
The aforementioned appears to be a simplistic approach and would not work on a more hardened, modern security solution. However, such a solution will not always be found on a dedicated machine like an ATM.
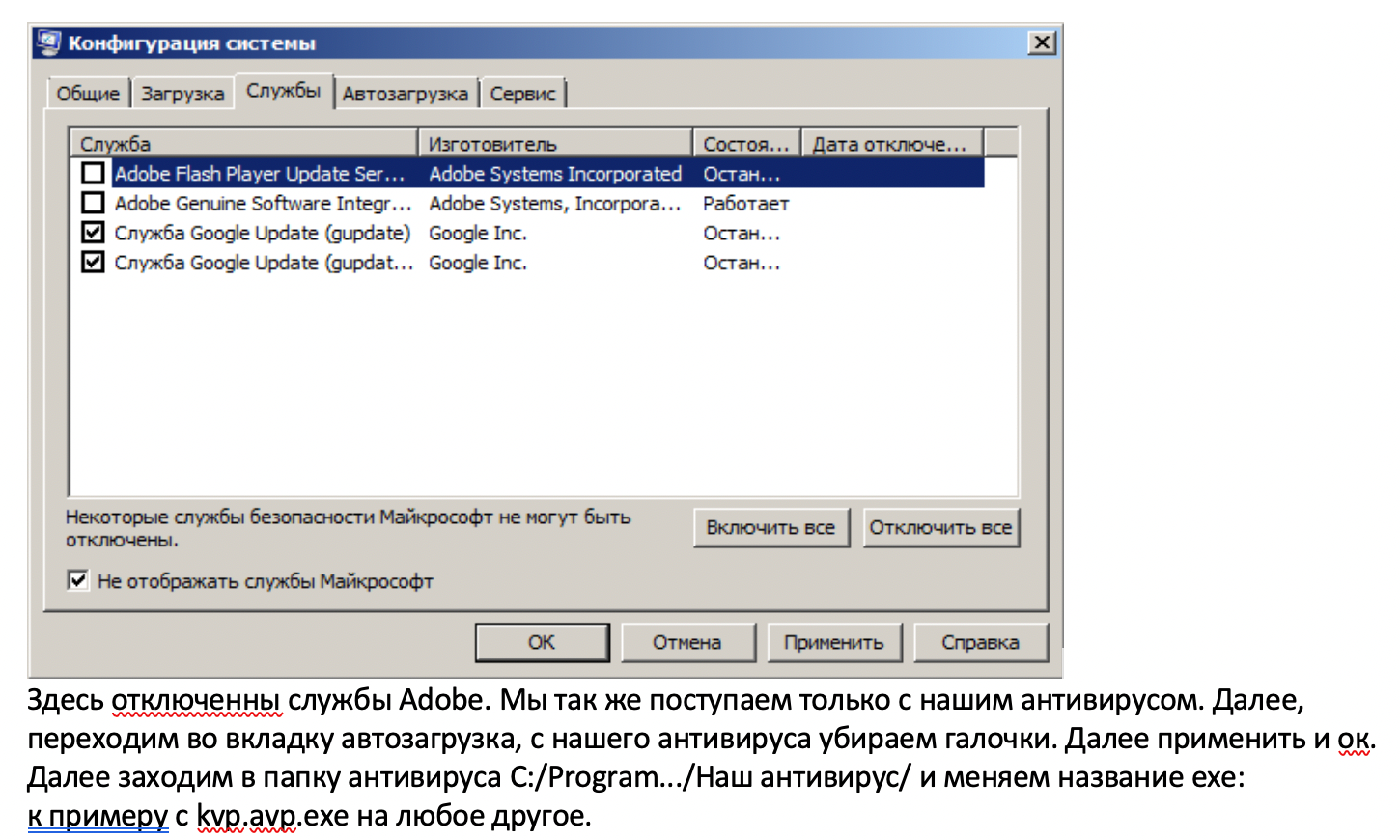 A snippet explaining how to disable the antivirus program, if the ATM has one installed
A snippet explaining how to disable the antivirus program, if the ATM has one installed
Case Study: An ATM Malware Reseller
ATM malware is becoming a common offering in criminal underground forums, and it's not the exotic or niche item it was before. A seller was even seen offering multiple malware families in one of these forums. These posts are probably not from the original malware authors; they're likely from resellers taking a cut from the sales.
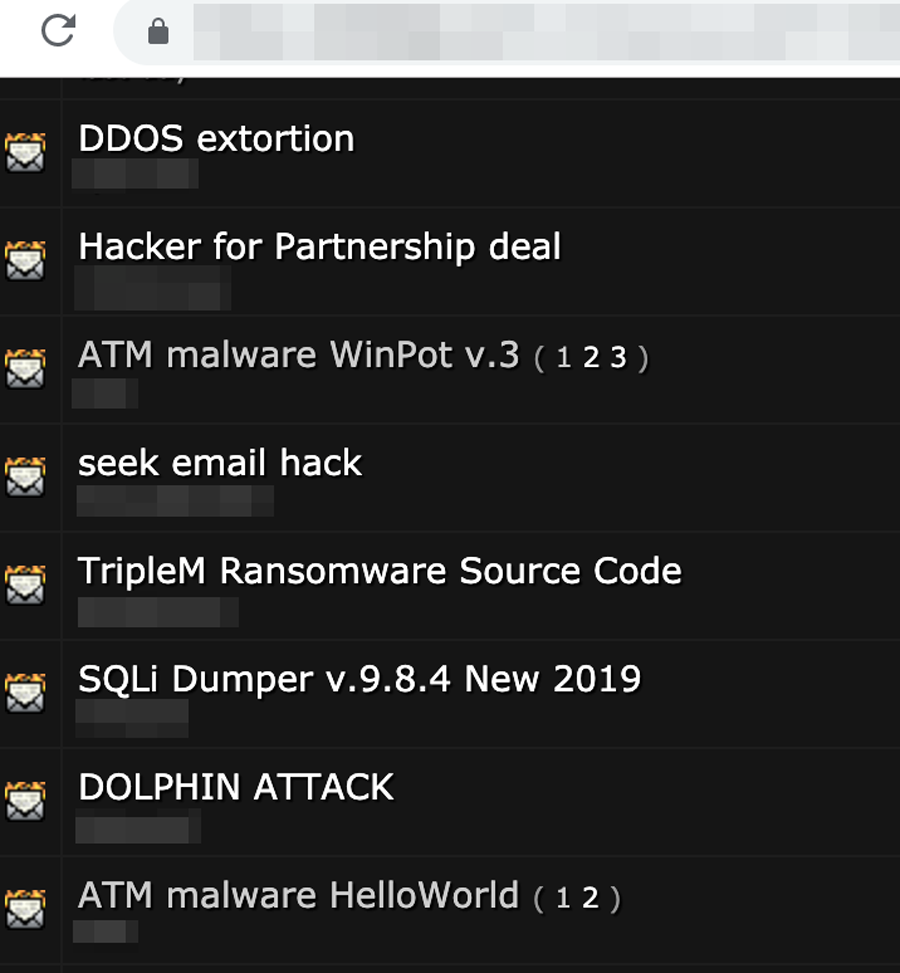 List of recent threads in a popular criminal forum
List of recent threads in a popular criminal forum
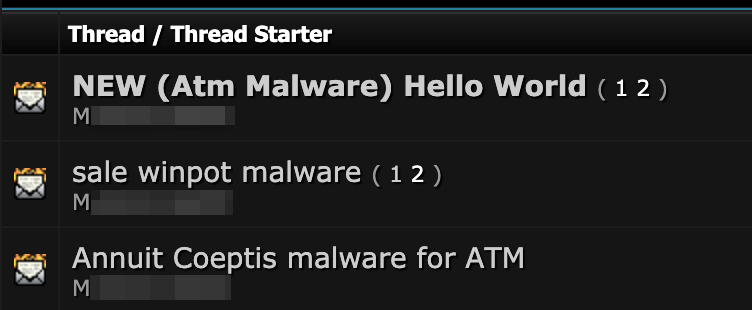 List of three underground forum threads showing different ATM malware files being offered by the same seller
List of three underground forum threads showing different ATM malware files being offered by the same seller
While looking through these criminal forums, we couldn’t help but notice a particular reseller who was specializing in ATM malware, so we decided to take a closer look into the user's profile. The criminal postings by M_ (full username redacted) were peddling many different ATM malware toolkits in criminal forums.
The forum poster does not appear to be the original coder of these projects; he's a reseller, based on the comments from buyers and other forum users. The seller has replied multiple times to forum threads with “I’m selling the same software at a substantially lower price.” Also, this person has videos demonstrating how the malware works, posted on DarkVideo, a video streaming site. Other forum users have accused this actor of selling software that does not work. As a side note, his written Russian reads as if it was translated, which implies that he might not be a native speaker.
M_ has advertised a variety of ATM malware for the following prices:
Based on this individual’s online presence and forum activity, we could compose a more detailed profile, which is available only to LEA members.
ATM Malware as a Commodity for Digital Bank Heists
The number of ATM malware offerings in cybercriminal underground forums has significantly increased in the last two years. This type of malware, which used to belong exclusively to criminal gangs (that used them for their benefit), is now becoming a mainstream tool that's bought and used by enterprising criminals. In other words, ATM malware is becoming a commodity that allows any would-be criminal with a few hundred dollars to start attacking ATMs.
Some of these criminal advertisements will no doubt be pure scams, but some of them appear to deliver. In fact, we have seen positive reviews that indicate some of the sellers offer working malware. There are several families available, but we can see that some are becoming more popular than others — reminiscent of the time when Zeus and SpyEye were competing to be the top banking trojan in the cybercriminal underground.
What can we expect in the near future? If things don’t take a radical turn, more criminals will start trying to subvert unprotected ATMs. However, the techniques they use are very basic, and the technical level of the average attacker is low. This means that security countermeasures that get in their way might deter them from committing this crime.
Unfortunately, unprotected ATMs are still common, but banks could eliminate these low-hanging fruits by putting up more security measures. If this happens, we might see ATM attacks go back to being more targeted and highly technical, but the likelihood of this happening depends on each bank’s defense budget.
If your company owns a significant amount of unprotected ATMs in the field, the risk of them becoming targeted with ATM malware grows every month.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks