Italian Spam Campaign Delivers URSNIF Malware
Publish Date: 16 août 2018
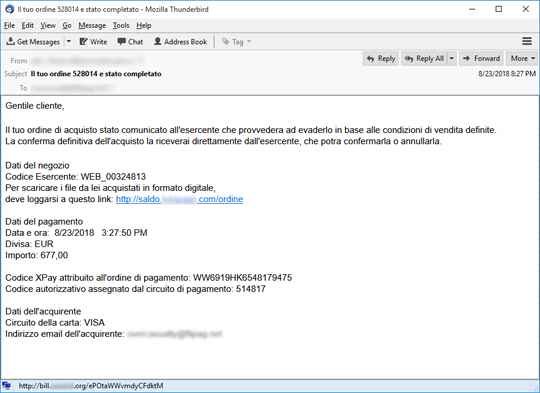
We spotted a recent spam campaign in Italian that delivers URSNIF malware to unsuspecting users. The email deceives its recipients by posing as a notification with a link that leads to the supposed receipt from a recent purchase. Upon checking, different links coming from a range of compromised websites were used in this campaign, which downloads either a VBScript (.VBS) or JavaScript (.JS) file. Some of the sites are:
- hxxp://bill.{somedomain}.com/ordine
- hxxp://bill.{somedomain}.org/{randomstring}
- hxxp://bill.{somedomain}.com/{randomstring}
- hxxp://bill.{somedomain}.us/{randomstring}
- hxxp://fattura.{somedomain}.com/ordine
- hxxp://fattura.{somedomain}.com/{randomstring}
- hxxp://ordine.{somedomain}.org/ordine
- hxxp://ordine.{somedomain}.ca/{randomstring}
- hxxp://ordine.{somedomain}.us/{randomstring}
- hxxp://ordine.{somedomain}.com/ordine
- hxxp://saldo.{somedomain}.com/{randomstring}
- hxxp://saldo.{somedomain}.com/ordine
- hxxp://status.{somedomain}.org/{randomstring}
- hxxp://www.{somedomain}.com/{randomstring}?{randomstring}={randomnumbers}
Early waves of the attack were observed on August 16 and were seen to use FTP links as shown below:
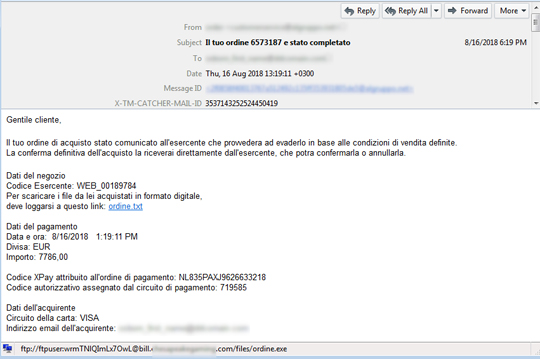
Upon clicking the link, it will download a VBS or a JS file, which is the actual downloader of the URSNIF malware. Should the user click on the malicious link and download the file, the user's machine will be infected once it's executed.
The files were found to be obfuscated:
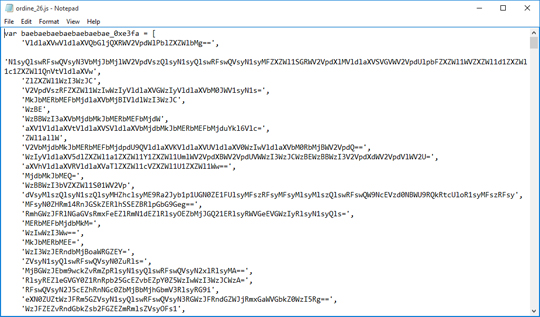
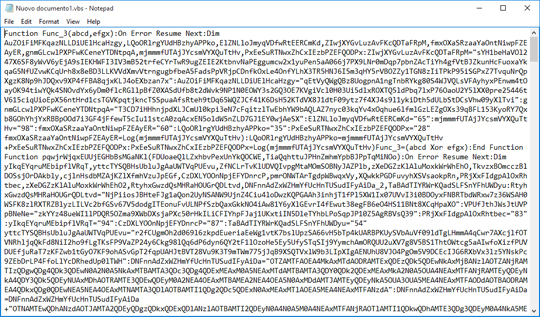
JS file that downloads URSNIF is detected by Trend Micro as JS_DLOADR.AUSUKC. VBS file that downloads URSNIF is detected by Trend Micro as VBS_DLOADR.YYSXQ.
The payload, the downloaded malware file, is detected by Trend Micro as TSPY_URSNIF.TIBAIDT.
Trend Micro users are protected from this particular email threat. We advise users to be wary of their emails and to not open attachments or links in unsolicited emails. Email best practices will help users avoid being infected with malware such as URSNIF.
Spam Blocking Date/Time: : 16 août 2018 GMT-8
TMASE
- TMASE Engine: :
- Patrón TMASE: atures du moteur TMASE: :4036