Malspam With JavaScript Attachment Leads To Locky Ransomware
Publish Date: 23 mars 2016
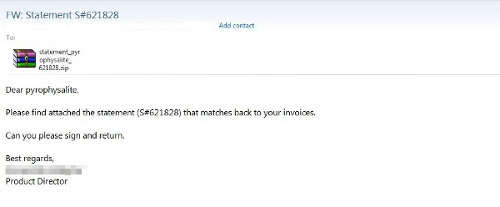
We are currently seeing huge volumes of malicious JavaScript attachments being spammed at users through email. This particular spam campaign uses the typical social engineering lures like invoice notifications, payment slips, payment confirmations, tax related notifications, billing statements, purchase orders and the like.
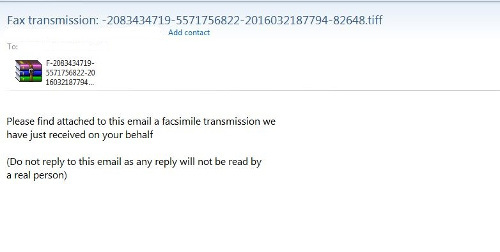
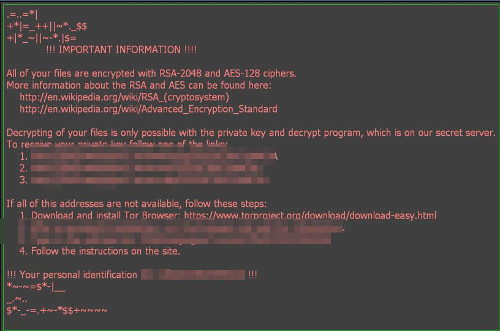
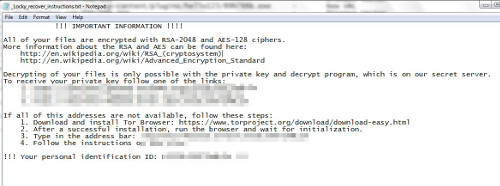
Users are once more advised not to open links from suspicious or unfamiliar senders, especially when they come with attachments.
Spam Blocking Date/Time: : 23 mars 2016 GMT-8
TMASE
- TMASE Engine: :
- Patrón TMASE: atures du moteur TMASE: :2210