DUNIHI Worms Its Way Into Removable Drives
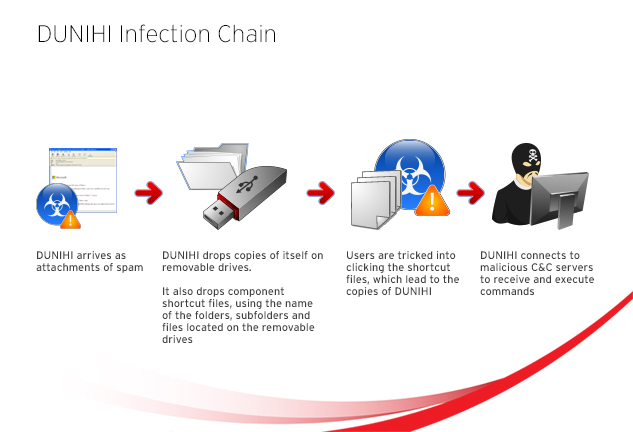
Although cybercriminals continuously refine their techniques, old tricks remain to be efficient in infecting user systems. One such example is DUNIHI variants which uses removable drives as its infection vector. Using Trend Micro Smart Protection Feedback, increased infections were found during the tail end of September onwards. Majority of the detections were found in the Latin America and Asia Pacific regions.
What is DUNIHI?
Like your typical worm, DUNIHI propagates copies of itself specifically on removable drives. It drops its component shortcut file (LNK file), which actually points to its copies found in the removable drives.
What is interesting about this worm is that it uses the name of the folders, subfolders and files located on the removable drives. It then sets the attributes of the original folders and files to System and Hidden to trick users into clicking the .LNK files (detected as LNK_DUNIHI).
How does the malware arrive into your user system?
Based on our research, the DUNIHI worm may initially arrive as an attachment to spam. The spam may take on different forms, and so far we have determined several spam samples carrying the malware which include a fake Microsoft email notice convincing users to update their OS using the file attached.
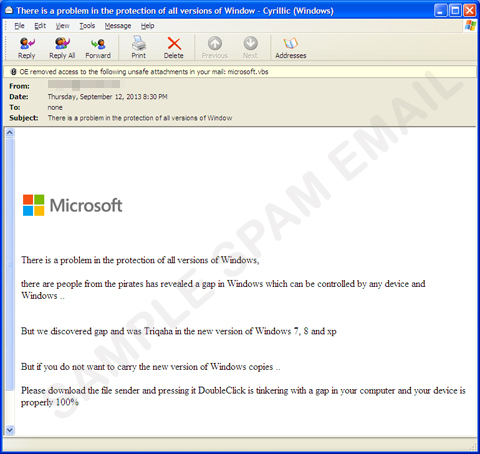
Figure 1. Sample spammed message
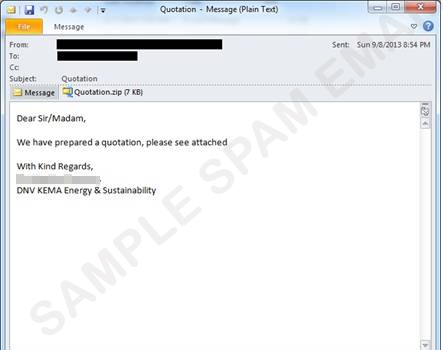
Figure 2. Sample spammed message
Another sample we found informs users of a price quotation with a .ZIP file. To execute, users need to unzip and open the said file. Based on our investigation, some samples were spotted bundled with an installer, one of which is VLC player. The said samples were uploaded in a file sharing website, http://{BLOCKED}e.tt. In addition, this malware may arrive via removable drives and can be dropped by another malware and downloaded from a malicious URL.
How do DUNIHI variants propagate?
DUNIHI variants search for all removable drives connected to the infected machine. It then drops a copy of itself to the drive’s directory with Hidden file attribute. It searches and hides all folders and files in the drive’s root directory and creates link files that point to the previously dropped copy of itself – one for each hidden folder and file. In addition, it makes use of icons on the shortcut to imitate the hidden files.
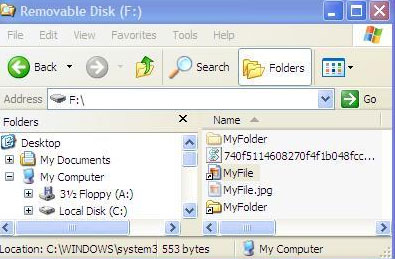
Figure 3. Sample image of removable drive after infection
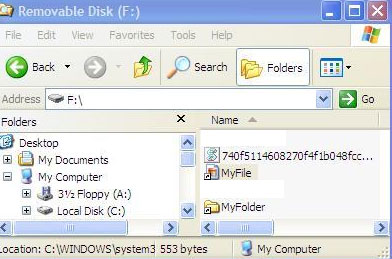
Figure 4. Screenshot of infected removable drives that doesn’t show the hidden files
Although the use of removable drives for propagation and hidden folder as malware shortcut is an old trick already, it is still efficient in infecting user systems.
What is noteworthy about DUNIHI?DUNIHI tricks users into thinking that the malicious .LNK components are the actual folders and files. It uses a clever social engineering trick to hoodwink users into thinking that they are opening legitimate files on the said folder. Once done, the .LNK components lead to the copies of DUNIHI, which are found in the removable drives and are set to Hidden to avoid suspicions from users.
Aside from its social engineering trick, DUNIHI (detected as VBS_DUNIHI) connects to malicious command-and-control (C&C) servers to receive and execute commands onto the infected system. Below are some of the malicious routines that it can execute:|
Backdoor Commands |
Description |
| execute | Execute arbitrary code received from C&C server |
| update | Download and execute an updated copy of itself |
| uninstall | Uninstall itself from the system and removable drives |
| send | Downloads and executes a file from a URL specified by the C&C server. It uses the same file name with the one in the URL and save in a directory also specified by the C&C server. If there is no specified directory, it uses the install directory in its configuration. |
| site-send | Downloads and executes a file from a URL specified by the C&C server. It uses the file name specified by the C&C server and saves it to the install directory in its configuration. |
| recv | Uploads a specified file to the C&C server |
| enum-driver | Sends list of all drives and their drive types |
| enum-faf | Sends all subfolders and files found in the specified directory. |
| enum-process | Sends running processes |
| cmd-shell | Executes "cmd.exe /c {command from C&C}" then sends result. |
| delete | Deletes a specified file |
| exit-process | Terminates a process with the corresponding Process ID specified. Uses shell command, "taskkill /F /T /PID {Process ID}". |
| sleep | Sleep for a specified amount of time |
How does this affect users?
Because DUNIHI’S .LNK component uses the filenames of the folders and files found in the removable drives before infection, users are likely to mistake them for legitimate files. Also, VBS_DUNIHI connects to certain C&C servers to receive and execute commands. This makes the infected system susceptible to more malware infections and information theft.
One of the primary means for DUNIHI variants to propagate is via removable drives. As such, employees who use USBs in the workplace can potentially introduce the dangers posed by this threat.
How do I protect myself from this threat?
For users, it is best to always double-check the validity of email messages before opening and downloading the attached files. If possible, verify with the email sender if the email receive is legitimate or not. In the case of the fake MS email, users can visit Microsoft’s official web page to check future software updates. Also, MS does not email updates to users.
To know more how attackers and other online bad guys use social engineering tricks to lure users into their traps, you can check out Digital Life E-guide How Social Engineering Works. Users are also recommended to disable the AUTORUN feature since this malware uses removable drives to propagate.
Does Trend Micro protect users from this threat?
Trend Micro protects users from this threat by detecting the related email messages from the user’s email inboxes via email reputation services. The malware is also detected and deleted if found in the system via file reputation services, while web reputation services blocks access to the domains where DUNIHI variants connect to.
FROM THE FIELD: EXPERT INSIGHTS
“Aside from the propagation routine, this malware is also capable of executing commands from remote users. This can be achieved once it successfully connects to its C&C server. For me, these actions are more alarming rather than its propagation routine. It exposes the infected machine to more critical situation.” –Jeffrey Bernardino, threat response engineer