Ransom.Win64.DONOTRUN.A
Python/Filecoder.EK trojan, Python/Filecoder.EK trojan (NAI)
Windows


Threat Type: Ransomware
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
This ransomware locks the user out of their devices by locking the screen.
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It drops files as ransom note.
TECHNICAL DETAILS
Arrival Details
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Ransomware drops the following files:
- %Temp%\_MEI{random 5 characters}\certifi\cacert.pem
- %Temp%\_MEI{random 5 characters}\certifi\py.typed
- %Temp%\_MEI{random 5 characters}\charset_normalizer\md.cp311-win_amd64.pyd
- %Temp%\_MEI{random 5 characters}\charset_normalizer\md__mypyc.cp311-win_amd64.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_ARC4.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_chacha20.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_pkcs1_decode.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_aes.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_aesni.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_arc2.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_blowfish.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_cast.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_cbc.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_cfb.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_ctr.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_des.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_des3.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_ecb.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_eksblowfish.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_ocb.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_ofb.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_Salsa20.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_BLAKE2b.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_BLAKE2s.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_ghash_clmul.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_ghash_portable.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_keccak.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_MD2.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_MD4.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_MD5.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_poly1305.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_RIPEMD160.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_SHA1.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_SHA224.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_SHA256.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_SHA384.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_SHA512.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Math\_modexp.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Protocol\_scrypt.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\PublicKey\_ec_ws.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\PublicKey\_ed448.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\PublicKey\_ed25519.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\PublicKey\_x25519.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Util\_cpuid_c.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Util\_strxor.pyd
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\d3dcompiler_47.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\libEGL.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\libGLESv2.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\MSVCP140.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\MSVCP140_1.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\opengl32sw.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Core.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5DBus.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Gui.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Network.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Qml.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5QmlModels.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Quick.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Quick.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Quick.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Widgets.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Widgets.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\generic\qtuiotouchplugin.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\iconengines\qsvgicon.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qgif.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qgif.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qico.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qjpeg.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qsvg.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qsvg.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qsvg.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qwbmp.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qwbmp.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\platforms\qminimal.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\platforms\qoffscreen.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\platforms\qwebgl.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\platforms\qwindows.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\platformthemes\qxdgdesktopportal.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\styles\qwindowsvistastyle.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_ar.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_bg.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_ca.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_cs.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_cs.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_de.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_en.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_es.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_fi.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_fr.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_gd.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_gd.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_hu.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_it.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_it.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_ko.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_lv.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_pl.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_ru.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_sk.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_tr.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_uk.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_zh_TW.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\QtCore.pyd
- %Temp%\_MEI{random 5 characters}\PyQt5\QtGui.pyd
- %Temp%\_MEI{random 5 characters}\PyQt5\QtWidgets.pyd
- %Temp%\_MEI{random 5 characters}\PyQt5\win_amd64.pyd
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info\entry_points.txt
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info\INSTALLER
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info\LICENSE
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info\METADATA
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info\RECORD
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info\REQUESTED
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info\top_level.txt
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info\WHEEL
- %Temp%\_MEI{random 5 characters}\_asyncio.pyd
- %Temp%\_MEI{random 5 characters}\_bz2.pyd
- %Temp%\_MEI{random 5 characters}\_cffi_backend.cp311-win_amd64.pyd
- %Temp%\_MEI{random 5 characters}\_ctypes.pyd
- %Temp%\_MEI{random 5 characters}\_decimal.pyd
- %Temp%\_MEI{random 5 characters}\_hashlib.pyd
- %Temp%\_MEI{random 5 characters}\_lzma.pyd
- %Temp%\_MEI{random 5 characters}\_multiprocessing.pyd
- %Temp%\_MEI{random 5 characters}\_overlapped.pyd
- %Temp%\_MEI{random 5 characters}\_queue.pyd
- %Temp%\_MEI{random 5 characters}\_socket.pyd
- %Temp%\_MEI{random 5 characters}\_ssl.pyd
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-console-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-datetime-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-debug-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-errorhandling-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-file-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-file-l1-2-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-file-l2-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-handle-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-heap-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-interlocked-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-libraryloader-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-localization-l1-2-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-memory-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-namedpipe-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-processenvironment-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-processthreads-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-processthreads-l1-1-1.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-profile-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-rtlsupport-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-string-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-synch-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-synch-l1-2-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-sysinfo-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-timezone-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-util-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-conio-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-convert-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-environment-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-filesystem-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-heap-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-locale-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-math-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-process-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-runtime-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-runtime-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-string-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-string-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-utility-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\base_library.zip
- %Temp%\_MEI{random 5 characters}\libcrypto-1_1.dll
- %Temp%\_MEI{random 5 characters}\libffi-8.dll
- %Temp%\_MEI{random 5 characters}\libssl-1_1.dll
- %Temp%\_MEI{random 5 characters}\pyexpat.pyd
- %Temp%\_MEI{random 5 characters}\python3.dll
- %Temp%\_MEI{random 5 characters}\python311.dll
- %Temp%\_MEI{random 5 characters}\select.pyd
- %Temp%\_MEI{random 5 characters}\ucrtbase.dll
- %Temp%\_MEI{random 5 characters}\unicodedata.pyd
- %Temp%\_MEI{random 5 characters}\VCRUNTIME140.dll
- %Temp%\_MEI{random 5 characters}\VCRUNTIME140_1.dll
(Note: %Temp% is the Windows temporary folder, where it usually is C:\Windows\Temp on all Windows operating system versions.)
It adds the following processes:
- {Malware Path}\{Malware File Name}.exe
- %System%\cmd.exe /c sc stop WinDefend
- %System%\sc.exe /c sc stop WinDefend
- %System%\cmd.exe /c "ver"
- %System%\conhost.exe 0xffffffff –ForceV1
- %System%\conhost.exe 0xffffffff –ForceV1
(Note: %System% is the Windows system folder, where it usually is C:\Windows\System32 on all Windows operating system versions.)
It creates the following folders:
- %Temp%\_MEI{random 5 characters}
- %Temp%\_MEI{random 5 characters}\certifi
- %Temp%\_MEI{random 5 characters}\charset_normalizer
- %Temp%\_MEI{random 5 characters}\Crypto
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher
- %Temp%\_MEI{random 5 characters}\Crypto\Hash
- %Temp%\_MEI{random 5 characters}\Crypto\Math
- %Temp%\_MEI{random 5 characters}\Crypto\Protocol
- %Temp%\_MEI{random 5 characters}\Crypto\PublicKey
- %Temp%\_MEI{random 5 characters}\Crypto\Util
- %Temp%\_MEI{random 5 characters}\PyQt5
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\generic
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\iconengines
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\platforms
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\platformthemes
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\styles
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info
(Note: %Temp% is the Windows temporary folder, where it usually is C:\Windows\Temp on all Windows operating system versions.)
Other Details
This Ransomware connects to the following possibly malicious URL:
- discord.com:{BLOCKED}3
- api.ipify.org:{BLOCKED}3
It does the following:
- It locks the screen and displays the following image:
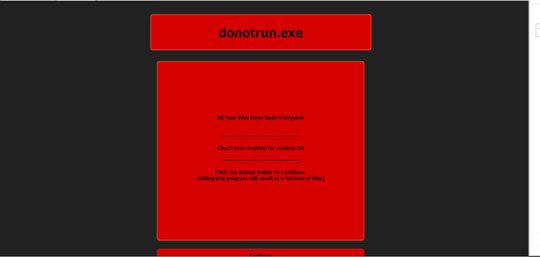
Ransomware Routine
This Ransomware drops the following file(s) as ransom note:
- %Desktop%\readme.txt
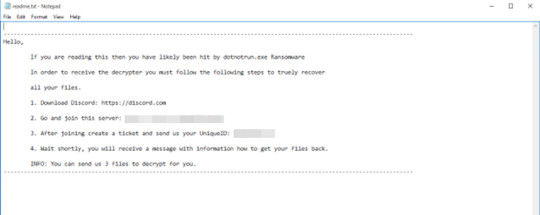
SOLUTION
Step 1
Before doing any scans, Windows 7, Windows 8, Windows 8.1, and Windows 10 users must disable System Restore to allow full scanning of their computers.
Step 2
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 3
Restart in Safe Mode
Step 4
Search and delete these files
- %Temp%\_MEI{random 5 characters}\certifi\cacert.pem
- %Temp%\_MEI{random 5 characters}\certifi\py.typed
- %Temp%\_MEI{random 5 characters}\charset_normalizer\md.cp311-win_amd64.pyd
- %Temp%\_MEI{random 5 characters}\charset_normalizer\md__mypyc.cp311-win_amd64.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_ARC4.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_chacha20.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_pkcs1_decode.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_aes.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_aesni.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_arc2.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_blowfish.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_cast.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_cbc.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_cfb.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_ctr.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_des.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_des3.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_ecb.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_eksblowfish.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_ocb.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_raw_ofb.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher\_Salsa20.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_BLAKE2b.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_BLAKE2s.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_ghash_clmul.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_ghash_portable.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_keccak.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_MD2.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_MD4.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_MD5.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_poly1305.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_RIPEMD160.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_SHA1.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_SHA224.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_SHA256.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_SHA384.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Hash\_SHA512.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Math\_modexp.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Protocol\_scrypt.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\PublicKey\_ec_ws.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\PublicKey\_ed448.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\PublicKey\_ed25519.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\PublicKey\_x25519.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Util\_cpuid_c.pyd
- %Temp%\_MEI{random 5 characters}\Crypto\Util\_strxor.pyd
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\d3dcompiler_47.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\libEGL.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\libGLESv2.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\MSVCP140.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\MSVCP140_1.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\opengl32sw.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Core.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5DBus.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Gui.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Network.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Qml.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5QmlModels.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Quick.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Quick.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Quick.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Widgets.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin\Qt5Widgets.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\generic\qtuiotouchplugin.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\iconengines\qsvgicon.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qgif.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qgif.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qico.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qjpeg.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qsvg.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qsvg.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qsvg.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qwbmp.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats\qwbmp.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\platforms\qminimal.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\platforms\qoffscreen.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\platforms\qwebgl.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\platforms\qwindows.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\platformthemes\qxdgdesktopportal.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\styles\qwindowsvistastyle.dll
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_ar.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_bg.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_ca.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_cs.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_cs.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_de.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_en.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_es.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_fi.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_fr.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_gd.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_gd.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_hu.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_it.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_it.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_ko.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_lv.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_pl.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_ru.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_sk.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_tr.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_uk.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations\qtbase_zh_TW.qm
- %Temp%\_MEI{random 5 characters}\PyQt5\QtCore.pyd
- %Temp%\_MEI{random 5 characters}\PyQt5\QtGui.pyd
- %Temp%\_MEI{random 5 characters}\PyQt5\QtWidgets.pyd
- %Temp%\_MEI{random 5 characters}\PyQt5\win_amd64.pyd
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info\entry_points.txt
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info\INSTALLER
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info\LICENSE
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info\METADATA
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info\RECORD
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info\REQUESTED
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info\top_level.txt
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info\WHEEL
- %Temp%\_MEI{random 5 characters}\_asyncio.pyd
- %Temp%\_MEI{random 5 characters}\_bz2.pyd
- %Temp%\_MEI{random 5 characters}\_cffi_backend.cp311-win_amd64.pyd
- %Temp%\_MEI{random 5 characters}\_ctypes.pyd
- %Temp%\_MEI{random 5 characters}\_decimal.pyd
- %Temp%\_MEI{random 5 characters}\_hashlib.pyd
- %Temp%\_MEI{random 5 characters}\_lzma.pyd
- %Temp%\_MEI{random 5 characters}\_multiprocessing.pyd
- %Temp%\_MEI{random 5 characters}\_overlapped.pyd
- %Temp%\_MEI{random 5 characters}\_queue.pyd
- %Temp%\_MEI{random 5 characters}\_socket.pyd
- %Temp%\_MEI{random 5 characters}\_ssl.pyd
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-console-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-datetime-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-debug-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-errorhandling-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-file-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-file-l1-2-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-file-l2-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-handle-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-heap-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-interlocked-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-libraryloader-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-localization-l1-2-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-memory-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-namedpipe-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-processenvironment-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-processthreads-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-processthreads-l1-1-1.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-profile-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-rtlsupport-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-string-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-synch-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-synch-l1-2-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-sysinfo-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-timezone-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-core-util-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-conio-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-convert-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-environment-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-filesystem-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-heap-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-locale-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-math-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-process-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-runtime-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-runtime-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-string-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-string-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\api-ms-win-crt-utility-l1-1-0.dll
- %Temp%\_MEI{random 5 characters}\base_library.zip
- %Temp%\_MEI{random 5 characters}\libcrypto-1_1.dll
- %Temp%\_MEI{random 5 characters}\libffi-8.dll
- %Temp%\_MEI{random 5 characters}\libssl-1_1.dll
- %Temp%\_MEI{random 5 characters}\pyexpat.pyd
- %Temp%\_MEI{random 5 characters}\python3.dll
- %Temp%\_MEI{random 5 characters}\python311.dll
- %Temp%\_MEI{random 5 characters}\select.pyd
- %Temp%\_MEI{random 5 characters}\ucrtbase.dll
- %Temp%\_MEI{random 5 characters}\unicodedata.pyd
- %Temp%\_MEI{random 5 characters}\VCRUNTIME140.dll
- %Temp%\_MEI{random 5 characters}\VCRUNTIME140_1.dll
- %Desktop%\readme.txt
Step 5
Search and delete these folders
- %Temp%\_MEI{random 5 characters}
- %Temp%\_MEI{random 5 characters}\certifi
- %Temp%\_MEI{random 5 characters}\charset_normalizer
- %Temp%\_MEI{random 5 characters}\Crypto
- %Temp%\_MEI{random 5 characters}\Crypto\Cipher
- %Temp%\_MEI{random 5 characters}\Crypto\Hash
- %Temp%\_MEI{random 5 characters}\Crypto\Math
- %Temp%\_MEI{random 5 characters}\Crypto\Protocol
- %Temp%\_MEI{random 5 characters}\Crypto\PublicKey
- %Temp%\_MEI{random 5 characters}\Crypto\Util
- %Temp%\_MEI{random 5 characters}\PyQt5
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\bin
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\translations
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\generic
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\iconengines
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\imageformats
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\platforms
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\platformthemes
- %Temp%\_MEI{random 5 characters}\PyQt5\Qt5\plugins\styles
- %Temp%\_MEI{random 5 characters}\setuptools-65.5.0.dist-info
Step 6
Restart in normal mode and scan your computer with your Trend Micro product for files detected as Ransom.Win64.DONOTRUN.A. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


