Cash and Communication: New Trends in the Middle East and North Africa Underground
by Mayra Rosario Fuentes and Ahmed Kamal Aly
Cybercriminal activity in underground markets constantly fluctuates in response to different factors, such as real-world market movements or the availability of new tools or technology. In our continued exploration of the Middle East and North Africa (MENA) underground, we noticed several changes since our previous investigation. Cybercriminals started using a new form of communication to transact, and the stolen goods-to-cash ecosystem suddenly made way for money laundering services. This means that cybercriminals are finding new and more discreet ways to move their money, and also experimenting with new ways to stay under the radar.
This was a definite shift from 2017, when cybercrime activities that originated from and targeted the MENA region escalated. A harmful old malware called Shamoon resurfaced, and industry experts found that Middle East organizations were susceptible to serious ransomware attacks. Also, a survey of oil and gas executives revealed that 50 percent of all cybercrime attacks targeted the oil and gas industry within the MENA region. This showed a shift in risk where services and operational technology were being hit instead of information technology. In this threat landscape, MENA underground marketplaces were quite active. A distinct culture set MENA apart from other countries’ markets, and a joint philosophy that encouraged free sharing allowed many types of crimeware to proliferate. In particular, malware and fake documents were readily available, and there were popular cashout services that helped criminals convert stolen merchandise.
However, in 2018 some of the popular goods and services offered in the underground changed. As mentioned above, active sellers evolved to match market need and client demands — mostly in terms of money services. Many MENA cybercriminals also changed from a free service and adopted a more secure end-to-end encrypted messaging used in other underground markets.
Prevalent Cybercriminal Acts in the Region
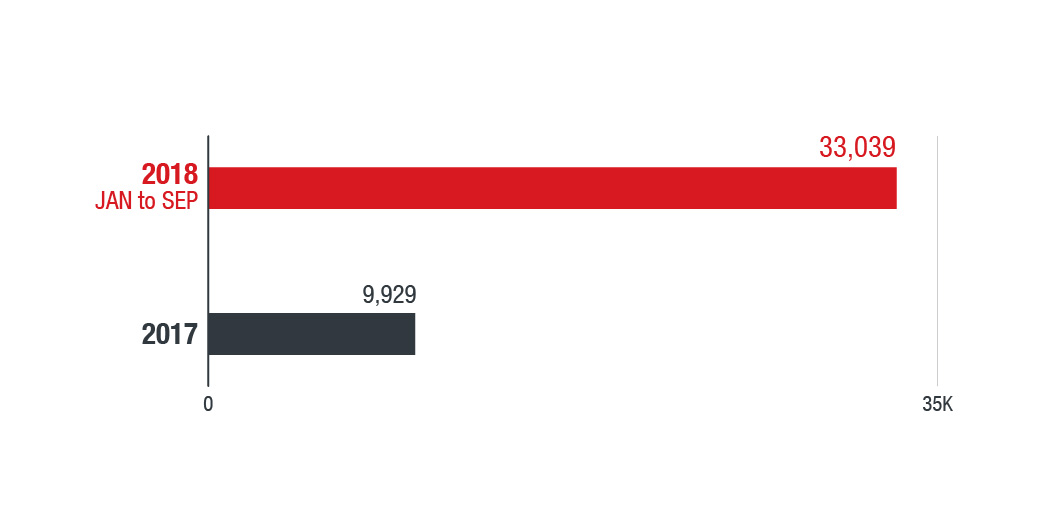
We noted a spike in overall malware detections from the last quarter of 2017 to the start of 2018, mostly from Turkey, United Arab Emirates (UAE), and Saudi Arabia. But when it comes to specific malicious activity, ransomware events are indeed on the rise. Our data shows a significant increase in the number of ransomware files detected within the MENA region from 2017. A comparison of the number of ransomware files we found in 2017 to the first nine months of 2018 shows a 233% increase. Our data also revealed that Turkey had the most ransomware activity in the region, followed by Tunisia and Saudi Arabia.
Figure 1: File-based ransomware detection for 2017 and 2018 (January to September) MENA countries
However, as we discussed in our previous report, common cybercriminal activity in the region also includes website disruptions such as Distributed denial of service (DDoS) and online vandalism like website defacement.
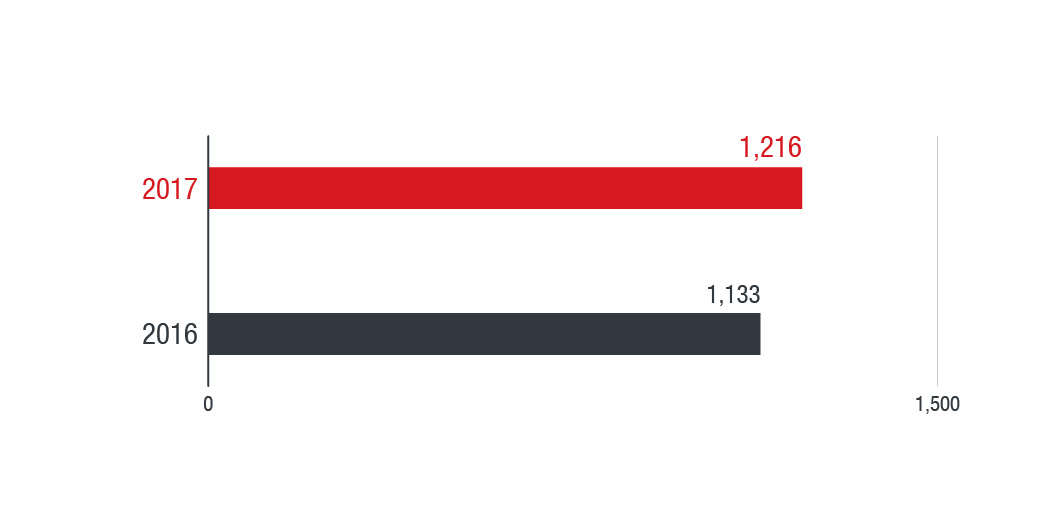
Figure 2: The rate of web defacement records in the MENA region from 2016-2017, for all websites reported to defacement archives
We analyzed data aggregated from reports submitted to defacement archives by the defacers themselves, along with shared initiatives, CERTs, and even data on the victims for 2016 and 2017. The data showed a significant jump in defacement events from 2016 to 2017, hitting Syria and Saudi Arabia the most. The MENA region is also a frequent target of DDoS attacks. A 2017 report from a global network management and application company showed that Kuwait and Saudi Arabia were the countries hit by the most DDoS attacks. The report also indicates that Saudi Arabia suffered the biggest recorded incident with a 140gbps DDoS attack.New developments in services and communications
Financial Services
Our 2017 paper on the MENA underground covered many different aspects of cybercriminal activity, which includes their operations, wares, clientele and markets. The report noted that cashout services were widespread in the underground. The services were used to convert physical items, usually stolen, into cash. However, these services have developed and evolved. Now, cash services are actually money laundering operations that convert money (instead of goods) into different currencies.
In multiple underground forums, these money laundering operations are now found in new dedicated sections called “broker” services or “contracts.” They advertise money exchanges from European banks, Paypal, Western Union, and MENA-specific banks. Brokers ask for commissions that range from 10% to 50% to help convert the money into a new currency. Often, the requests are to cash out money from American banks.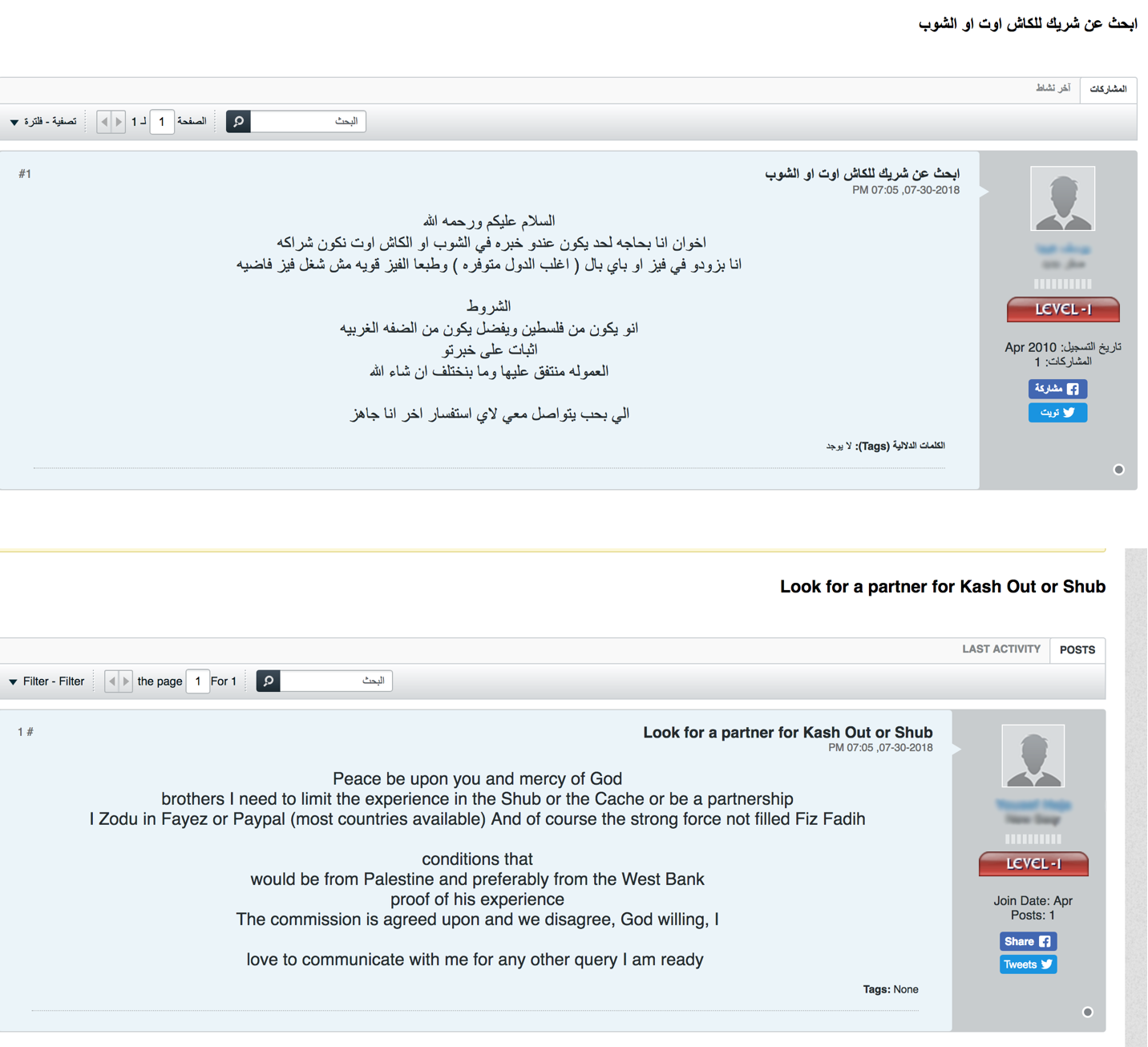
Figure 3: A user from the Soqor forum is looking for a new business partner for cashout services (translated in bottom image)
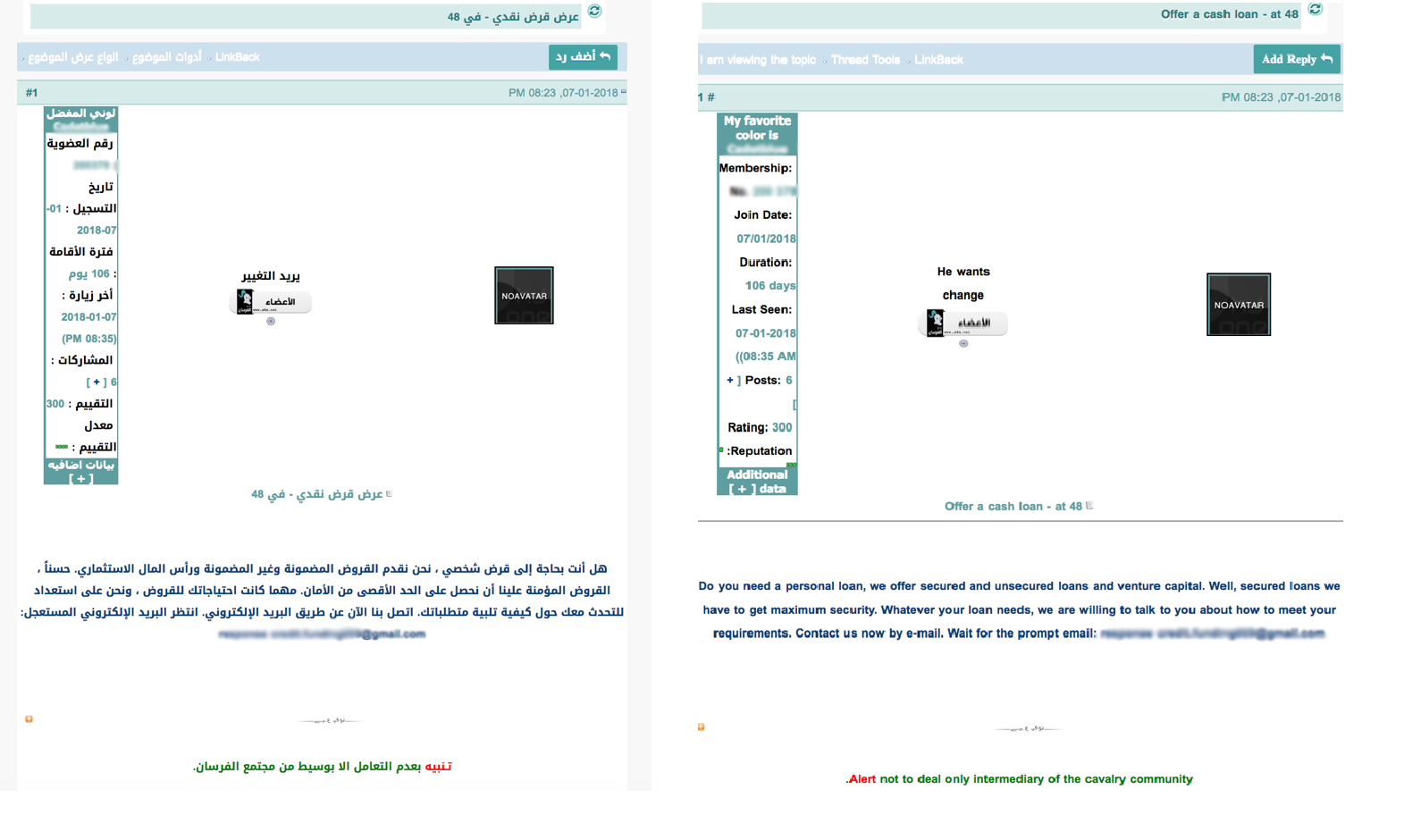
Figure 4: An advertisement on X6x offering "Personal loans" (translated in right image)
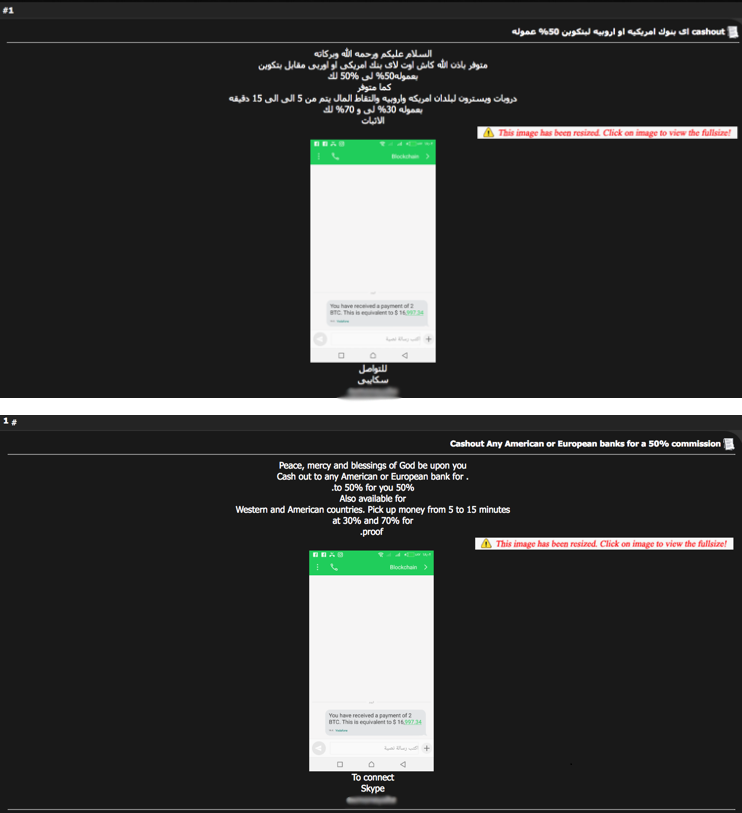
Figure 5: Hack-Int post advertising cashout services to any American or European bank (translated in bottom)
Discount Travel
Discount travel services were first seen on multiple MENA underground forums in late 2017. As mentioned in our previous research “How Cybercriminals Tour the World on the Cheap,” cybercriminals run this business by offering services paid for using stolen credit cards and hacked loyalty program accounts. This isn’t a unique service — Russian, English, and Chinese cybercriminal forums have been advertising discounts on travel documents as well as airline and hotel loyalty accounts for the past several years. Most of the travel discounts offered are for flights and hotels starting at 30% off the original price.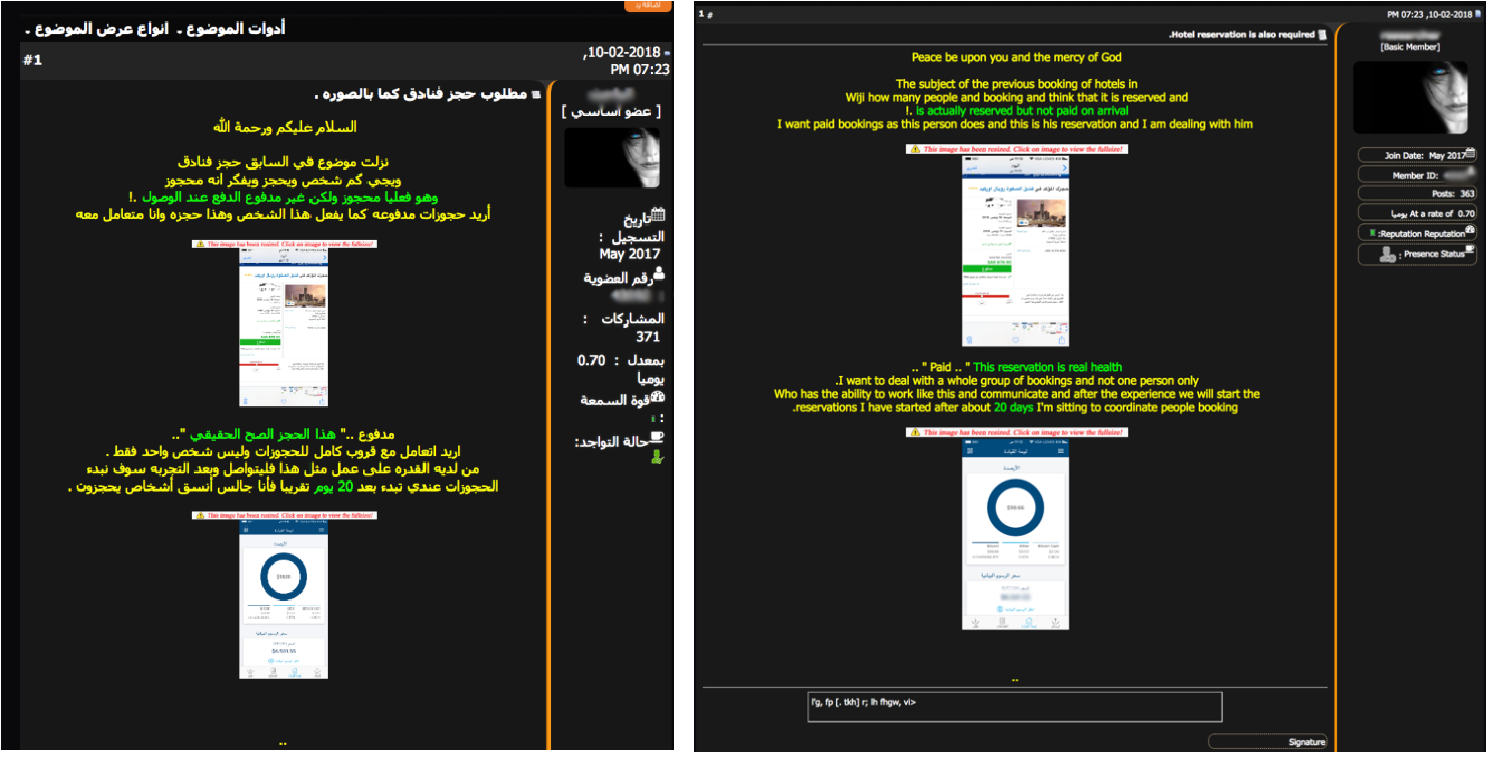
Figure 6: A user from Hack-int forum requesting assistance with booking BULK discount travel tickets (translated in right image)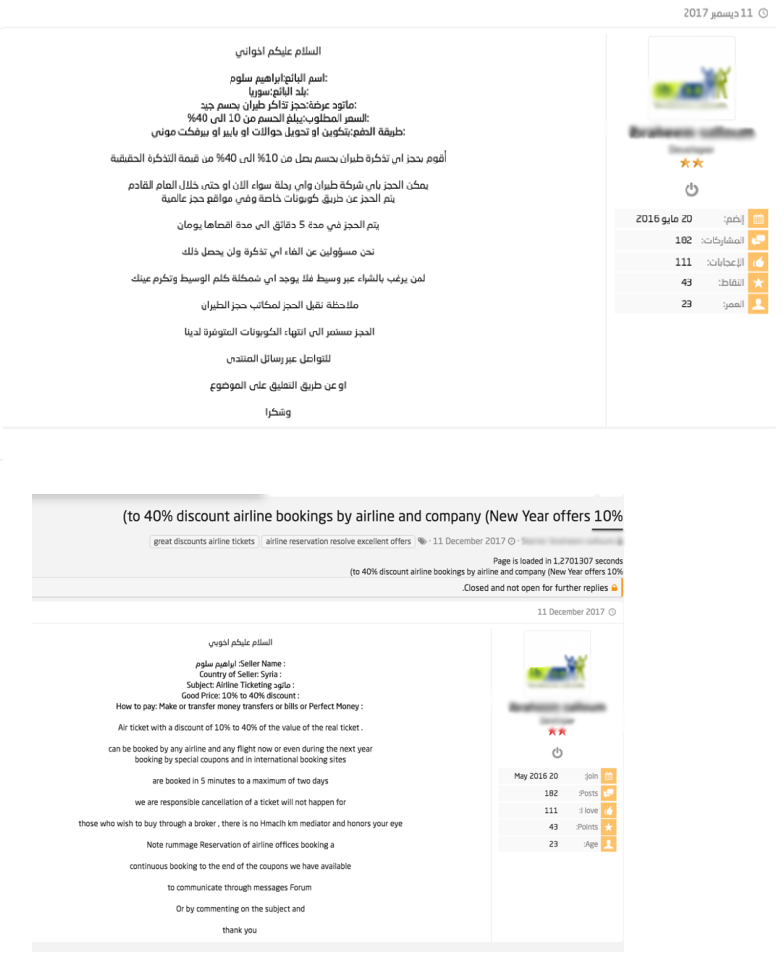
Figure 7: Advertisement for discount Airline tickets from the Dev-point forum (translated in bottom image)
Communications
MENA actors are now using Telegram, taking advantage of its secure messaging features to offer live support. Russian and Brazilian underground forums have been using Telegram for several years, and it makes sense for those in the MENA underground to follow the trend. Forum users are listing Telegram channels, along with the usual email address or Whatsapp number in their contact information.
Now, we see advertisements on MENA underground forums promoting dedicated sections for Telegram and topics to educate users on this application. Commonly posted topics include “how-to guides for searching users” and “how to create accounts without the need for a mobile number.” Since many MENA countries require personal identification like a passport or an ID before buying SIM cards or mobile phones, these guides are valuable for neophytes.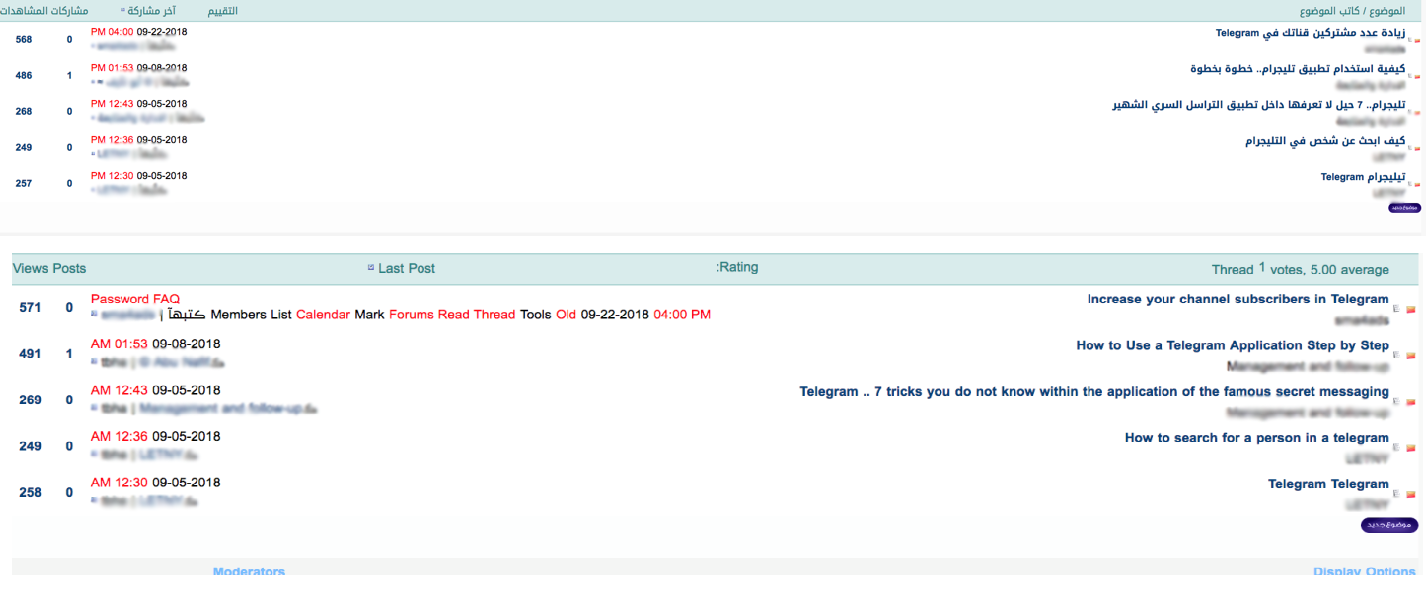
Figure 8: The telegram section found on the X6x forum as of October 2018 (translated in bottom image)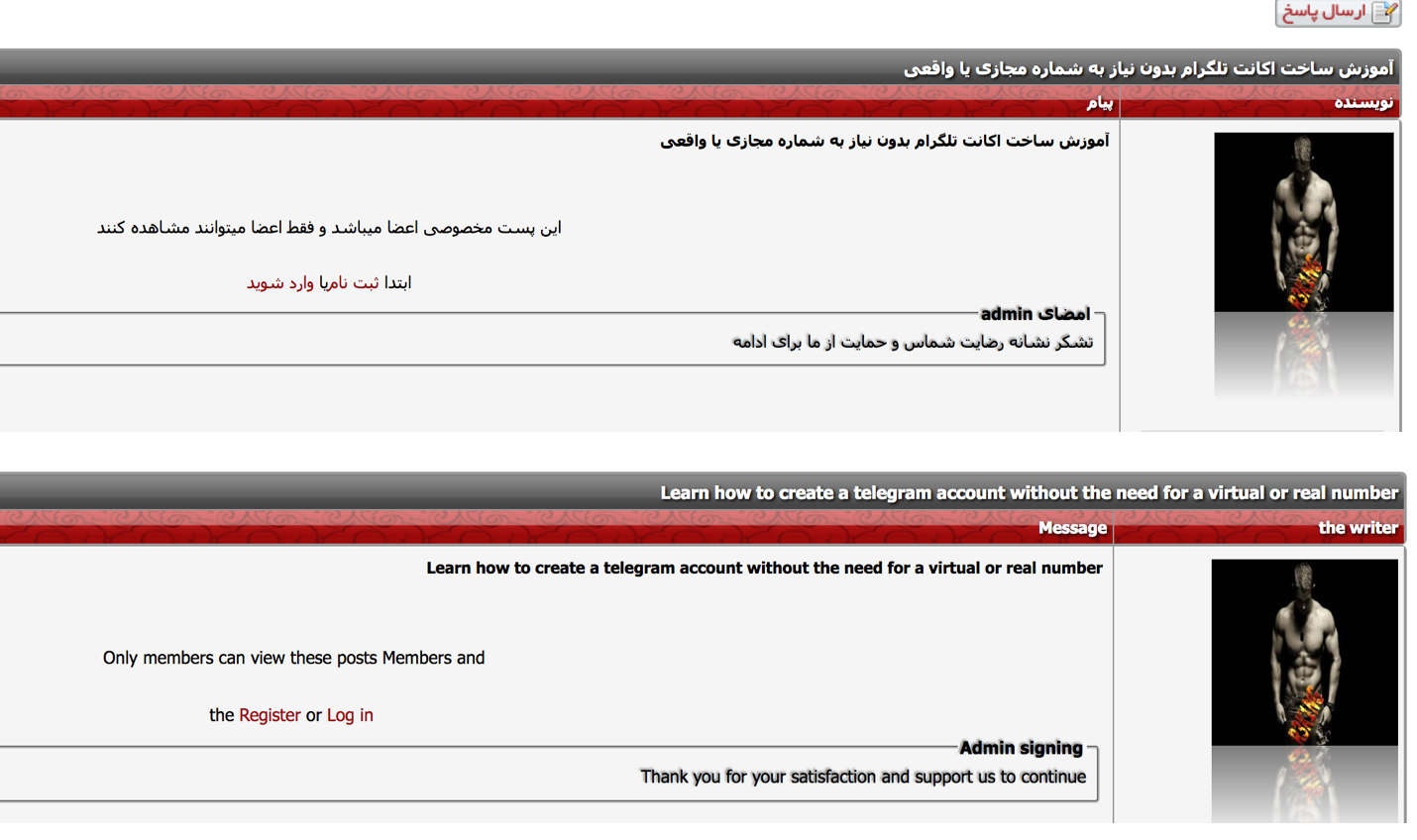
Figure 9: Advertisement on how to create a Telegram account without a mobile number on the .easypc.ir forum (translated in bottom image)
Providing sought after goods and services is what keeps an underground market in business, and the sellers have to keep up with the fluctuating needs of users. Cash moves freely online, and users are eager to move to services like PayPal where they can transact without leaving much of a footprint. Switching to stronger currencies is also in demand since markets continue to be quite volatile. Similarly, as the travel industry continues to grow, demand for airfare discounts and perks has increased.
Secure communication is also a significant factor in underground transactions — buyers and sellers need to be able to communicate freely to conduct business. The move to Telegram, with its end-to-end encryption, gives them anonymity and keeps them hidden from law enforcement. Given that underground markets in other countries already use Telegram, it was a shrewd move for those who are active on MENA markets.
The Next Targets of MENA Underground Cybercriminals
The future of cybercrime is with the internet of things (IoT). This isn’t a particularly new angle — threats against IoT have been growing every year. But because of the continuing proliferation of these devices, cybercriminals will have more and better opportunities to abuse them for their own gain.
IoT devices are scattered across homes and businesses — from security cameras, kitchen appliances, and smart door locks to gaming systems, TVs, smart wearables, HVACS, and ICS systems. And more IoT devices will be used in nation-wide programs within MENA: Saudi Arabia and UAE are committed to create smart cities across the country. UAE’s Roads and Transport Authority has already started using autonomous vehicles in certain districts this February. Also, Qatar launched an initiative to develop smart infrastructure in time for the 2022 World Cup.
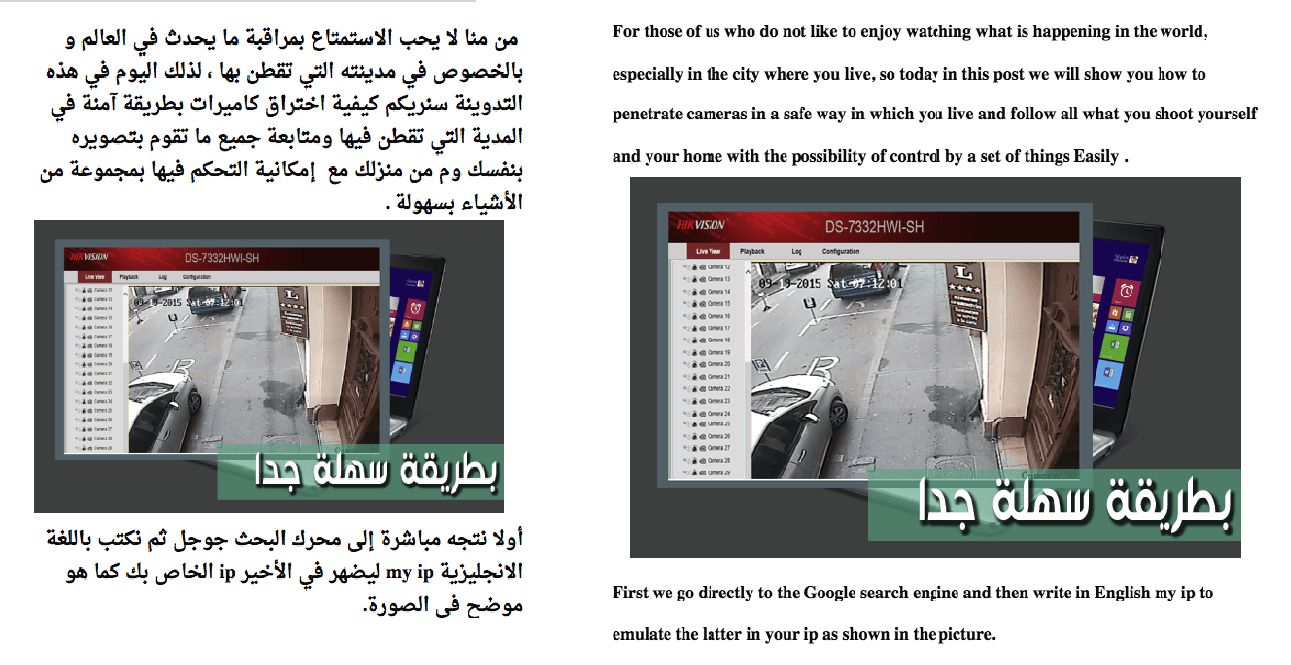
Figure 10. A Forum user discussing an easy way to hack cameras (translated in right image)

Figure 11. Discussion about Ransomware of Things on Dev-point (translated in right image)
As IoT further develops, we expect to see cybercriminals looking for new ways to exploit these networked devices to gain access to or control over them. In multiple Arabic speaking forums, users have already discussed the inner workings of popular IoT devices such as smart watches, lights, and robots.
And so, given the persistent spread of these devices and the wide-reaching impact of an IoT exploit, it should be a priority for homes and business owners to secure their devices as best they can.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks