Cybercriminals Unleash Bitcoin-Mining Malware
Introduction
Bitcoins have been around since 2008 but have only began gaining attention in September 2011. This increasing public attention did not go unnoticed by cybercriminals who have began unleashing Bitcoin-mining malware. The term "Bitcoin-mining malware" is used to refer to malware that cybercriminals use to install Bitcoin miners in users' systems. These allow cybercriminals to utilize systems' computing resources for their own gain.
What is a Bitcoin and how is it created?
Bitcoin is a form of electronic currency that uses peer-to-peer (P2P) networks to track and verify transactions. The Bitcoin system does not make use of financial institutions so no central authority is necessary to control this currency. Bitcoins can be used to pay for various online services like Web hosting, mobile app development, and cloud file storage. They can also be used to pay for products like games, music, gift cards, and books. Bitcoin use is not limited to online transactions, as some real-world establishments accept Bitcoins as payment for various goods. These can also be traded for traditional currency via sites that offer most international currencies in exchange.
Bitcoins are generated or “mined” after processing a so-called “block” of data. A Bitcoin block is a cryptographic problem one’s system solves with the aid of great computing power.
How do Bitcoin miners get into users' system?
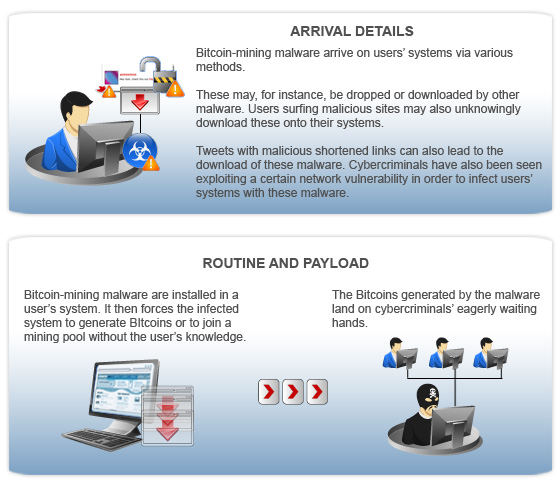
Most Bitcoin-mining malware arrive via malicious downloads or through social media. Exploitation of system and/or application vulnerabilities may also lead to infection.
| BKDR_BTMINE.MNR may arrive on users’ systems as part of a malware package. It may either be dropped or downloaded by other malware/grayware/spyware from malicious sites. These may also be unknowingly downloaded by users while visiting malicious sites. | BKDR_BTMINE.DDOS may also arrive as part of a malware package. These may be downloaded by other malware/grayware/ spyware from malicious sites or may be unknowingly downloaded by users while visiting malicious sites. | Cybercriminals use social media to infect users’ systems with Bitcoin-mining malware. They have, for instance, used Tweets with malicious links to trick users into downloading WORM_KOLAB.SMQX, which subsequently downloads HKTL_BITCOINMINE onto infected systems. | Some cybercriminals also used WORM_OTORUN.ASH to exploit a certain network vulnerability to force systems to participate in a Bitcoin pool. It may also be dropped or downloaded by other malware/spyware/ grayware from malicious sites. |
What happens to Bitcoin-mining-infected systems?
Bitcoin-mining malware primarily aim to force systems to generate Bitcoins for cybercriminals’ use.
| BKDR_BTMINE.MNR accesses malicious URLs to procure certain IP addresses. It then accesses the said IP addresses to send receive information, to download other malware, and to get an updated list of IP addresses. It also downloads and uses one of three different Bitcoin-mining software, depending on the infected system’s specifications. | BKDR_BTMINE.DDOS comes with a list of IP addresses that it tries to access in order to send and receive information, to download other malware, to get an updated list of IP addresses, and to obtain a list of sites to target via distributed denial-of-service (DDoS) attacks. | Upon execution, WORM_KOLAB.SMQX creates a directory that contains HKTL_BITCOINMINE—a Bitcoin-mining-mining grayware, in an infected system. WORM_KOLAB.SMQX uses this grayware to generate Bitcoins without the users’ knowledge. During analysis, the grayware tried but failed to access a malicious link using a specific user name and password. | WORM_OTORUN.ASH attempts to force infected systems to participate in a Bitcoin-mining pool service known as Deepbit. A Bitcoin mining pool refers to a network of Bitcoin miners that process the same block for faster payout. The Bitcoins generated through such a pool are then divided among the participants. |
How do Bitcoin-mining malware infections affect users?
The Bitcoin mining process eats up a system's computing power. As such, infected systems sustain increased wear and tear from processing Bitcoin blocks. Infected systems work abnormally slow. Even though Bitcoin-mining malware do not appear to target specific individuals, cybercriminals may choose to infect systems with highly capable graphic processing units (GPUs) or video cards, as these process Bitcoins faster. As such, gamers and other users of graphics-intensive applications may be especially favored targets.
What drives the proliferation of Bitcoin-mining malware?
Cybercriminals always try to find new ways to monetize their malicious activities. Bitcoin generation allows them to do just that. Infecting others’ systems with Bitcoin-mining malware allows cybercriminals to make money without exerting as much effort. The fact that Bitcoin is slowly being recognized as a legitimate currency and that it has real-world value seems to be spurring greater cybercriminal interest.
What makes Bitcoin-mining malware attacks noteworthy?
Among the Bitcoin-mining-related malware we have seen so far, WORM_OTORUN.ASH is particularly noteworthy. The inclusion of Bitcoin-mining code may mean that cybercriminals are considering making Bitcoin mining a regular payload.
Do Trend Micro products protect users from Bitcoin-mining malware?
Yes, Trend Micro products protect users from the malware mentioned in this article. Backed by the Trend Micro™ Smart Protection Network™ infrastructure, Web reputation technology blocks users access to all of the related malicious URLs. File reputation technology, meanwhile, detects and deletes all known malware associated with involuntary Bitcoin mining.
What can users do to prevent Bitcoin-mining malware from infecting their systems?
Safe computing habits can help prevent system infection and involuntary Bitcoin mining:
- Do not download and install applications from unknown sites.
- Be wary of clicking shortened links on Twitter or any other site, regardless of source. URL shortening makes it difficult for a user to gauge a link’s legitimacy.
- Sudden unexplained system slowdown may indicate Bitcoin mining. Check it for clues of Bitcoin-mining malware infection like an unexplained increase in processing power usage.
- Invest in a security solution that can detect and prevent Bitcoin-mining malware from infecting your system.
Expert Insights
“Cybercriminals will continue to find ways to monetize their malicious activities. Bitcoin-mining malware attacks are just another means for them to do so. Bitcoin mining may have earned cybercriminal attention due to the fact that it represents a direct source of income.” —Roland Dela Paz, Trend Micro threat response engineer
“In the early part of September, a Bitcoin was worth more than US$8. Should the value of Bitcoins rise, the number of Bitcoin-mining malware will also increase.” —Karl Dominguez, Trend Micro threat response engineer