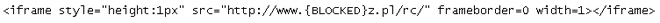PE_VIRUX.S-4
Windows 2000, XP, Server 2003


Threat Type: File infector
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This file infector infects target host files via Cavity-Appending infection technique.
It hooks APIs so that when these APIs are called, the virus code is executed which then infect files.
It does not infect files with certain characteristics.
It also searches for target script files for iframe infection. Infected script files are detected as HTML_IFRAME.SMV.
It connects to certain IRC servers and attempts to join a certain channel to receive and execute commands on the affected system.
As of this writing, no reply has been received from the servers.
This file infector may be dropped by other malware. It may be unknowingly downloaded by a user while visiting malicious websites.
It connects to Internet Relay Chat (IRC) servers.
TECHNICAL DETAILS
Arrival Details
This file infector may be dropped by other malware.
It may be unknowingly downloaded by a user while visiting malicious websites.
Installation
This file infector injects threads into the following normal process(es):
- WINLOGON.EXE
Other System Modifications
This file infector also creates the following registry entry(ies) as part of its installation routine:
HKEY_USERS\.DEFAULT\SOFTWARE\
Microsoft\Windows\CurrentVersion\
Explorer
UpdateHost = {random binary value}
It creates the following registry entry(ies) to bypass Windows Firewall:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\SharedAccess\Parameters\
FirewallPolicy\DomainProfile\AuthorizedApplications\
List
\??\%System%\winlogon.exe = \??\%System\winlogon.exe:*:enabled:@shell32.dll,-1
File Infection
This file infector infects the following file types:
- EXE
- SCR
It avoids infecting files that contain the following strings in their names:
- OTSP
- WC32
- WCUN
- WINC
Backdoor Routine
This file infector connects to any of the following Internet Relay Chat (IRC) servers:
- ilo.{BLOCKED}z.pl
- ant.{BLOCKED}z.pl
HOSTS File Modification
This file infector adds the following strings to the Windows HOSTS file:
- 127.0.0.1 www.{BLOCKED}z.pl
Other Details
Based on analysis of the codes, it has the following capabilities:
- It infects target host files via Cavity-Appending infection technique.
- It hooks the following APIs so that when these APIs are called, the virus code is executed which will then infect files:
- NtCreateFile
- NtOpenFile
- NtCreateProcess
- NtCreateProcessEx
- NtQueryInformationProcess
- It does not infect files with the following characteristics:
- .DLL files
- PE Files with _win section name
- Files with infection marker
- It also infects script files by first checking if the target script file's extension name is any of the following:
- ASP
- HTM
- PHP
- Once it finds target script files, it creates a flag for the file for iframe infection. It opens flagged files then checks for a certain string in the file. If it finds that string, it skips the file. If not, then it proceeds with the infection of the file.
- It then looks for the string