OSX_DEFMA.B
Mac OS


Threat Type: Trojan
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This malware makes use of <i>Facebook</i> links and blackhat search engine optimization (BHSEO) to lure users into malicious sites hosting this FAKEAV variant. This malware is one of the FAKEAV variants that target Mac OS users.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
This Trojan arrives via clicking on malicious links on Facebook.
It displays specific graphical user interface (GUI) in the web browser of affected system.
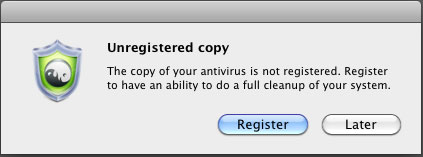
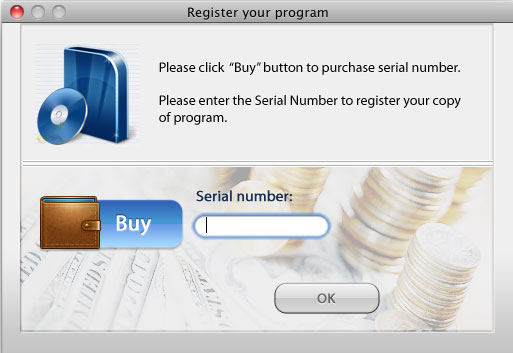
Once installed, it displays fake scanning results and shows random alerts urging users to register the product.
It also opens the default browser of the affected system to connect to pornographic sites.
This Trojan may be unknowingly downloaded by a user while visiting malicious websites.
It displays fake alerts that warn users of infection. It also displays fake scanning results of the affected system. It then asks for users to purchase it once scanning is completed. If users decide to purchase the rogue product, users are directed to a certain website asking for sensitive information, such as credit card numbers. When users agree to buy the software, it connects to a certain URL.
TECHNICAL DETAILS
Arrival Details
This Trojan may be unknowingly downloaded by a user while visiting malicious websites.
It may be downloaded from the following remote sites:
- http://{BLOCKED}ngs.in/
- http://{BLOCKED}es.in/
- http://{BLOCKED}234.76/
Installation
This Trojan drops the following files:
- //Application/MacDefender.app/
- //Application/MacDefender.app/Contents
- //Application/MacDefender.app/Contents/Info.plist
- //Application/MacDefender.app/Contents/MacOS
- //Application/MacDefender.app/Contents/MacOS/MacDefender
- //Application/MacDefender.app/Contents/PkgInfo
- //Application/MacDefender.app/Contents/Resources/{resource files}
- or
- //Application/MacGuard.app/
- //Application/MacGuard.app/Contents
- //Application/MacGuard.app/Contents/Info.plist
- //Application/MacGuard.app/Contents/MacOS
- //Application/MacGuard.app/Contents/MacOS/MacGuard
- //Application/MacGuard.app/Contents/PkgInfo
- //Application/MacGuard.app/Contents/Resources/{resource files}
Rogue Antivirus Routine
This Trojan displays fake alerts that warn users of infection. It also displays fake scanning results of the affected system. It then asks for users to purchase it once scanning is completed. If users decide to purchase the rogue product, users are directed to a certain website asking for sensitive information, such as credit card numbers.
When users agree to buy the software, it connects to the following URL to continue the purchase:
- http://{BLOCKED}.217.79/mac.php
NOTES:
It may also arrive on a system by clicking spammed malicious links on Facebook. It displays the following graphical user interface (GUI) in the Web browser of the affected system:
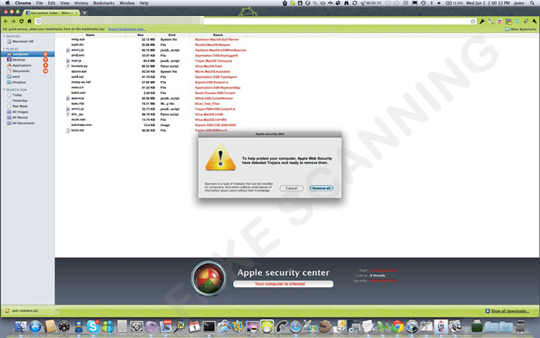
Clicking anywhere or refreshing the page results to re-download of the malware.
After installation, the following fake scan is shown by the malware:
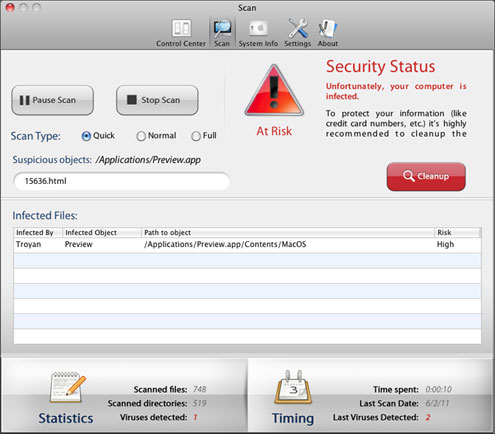
It also randomly display fake alerts and asks the user to register the product to clean the system:
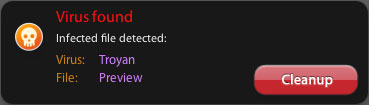
It displays the following if user agrees to buy the software:
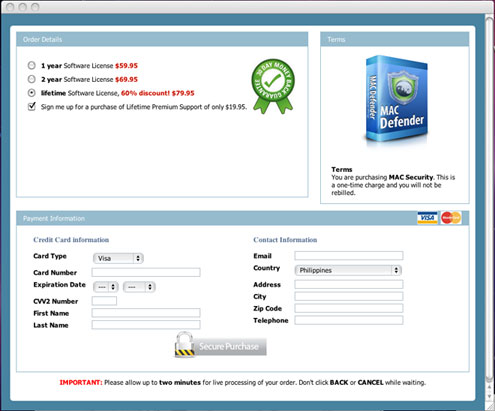
It also opens the default browser of the affected system to connect to the following pornographic websites:
- {BLOCKED}agra-now.net
- {BLOCKED}h.com
- {BLOCKED}mgalleries.com
- {BLOCKED}y.com
- {BLOCKED}rn.com
- {BLOCKED}orn.com
SOLUTION
NOTES:
Terminating Malware Program:
- To terminate the malware, open Activity Monitor in the Utilities or search using Spotlight.
- In the list of processes, click MacDefender or MacGuard.
- Click the Quit Process of Activity Monitor and then click Force Quit on the pop-up message that will appear.
- Go to your Applications folder and drag MacDefender or MacGuard to the Trash. You may also right-click on the application then select Move to Trash.
- Go to System Preferences > Accounts > Login Items.
- Select the checkbox for MacDefender or MacGuard.
- Click the (-) button to delete selected items.
Scan your computer with your Trend Micro product to delete files detected as OSX_DEFMA.B. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


