Securing the Pandemic-Disrupted Workplace: Trend Micro 2020 Midyear Cybersecurity Report
 Download Securing the Pandemic-Disrupted Workplace: Trend Micro 2020 Midyear Cybersecurity Report
Download Securing the Pandemic-Disrupted Workplace: Trend Micro 2020 Midyear Cybersecurity Report
In our annual predictions for 2020, we were able to forecast a new norm in the cybersecurity landscape. Still, no one could have anticipated that these changes would affect not just cybersecurity, but also healthcare, business, and other industries as well. Notably, there is a singular cause behind all these changes in cybersecurity: the coronavirus pandemic.
At a time when many business operations are immobilized or even on the verge of shutdown, cybercriminals continue to thrive. Operators, both known and emerging, take advantage of the current crisis by coming up with novel threats and strengthening existing ones. Even with fewer detections, ransomware remains a threat as operators arm malware with new capabilities to aim for bigger targets. Additionally, security researchers race to patch recently uncovered vulnerabilities.
Our midyear roundup examines pressing security issues during the first half of this year and offers recommendations to help enterprises secure their systems in the new normal terrain.
Threats connected to Covid-19 and WFH emerge
Referencing Covid-19 is one of the latest social engineering lures used by cybercriminals. We have witnessed a surge of nearly 9 million Covid-19-related threats from January to June 2020. These threats are delivered via email, URLs, or malicious files that mention the pandemic either blatantly or more subtly, as a factor affecting business services.
Number and distribution of Covid-19 threats, 1H 2020
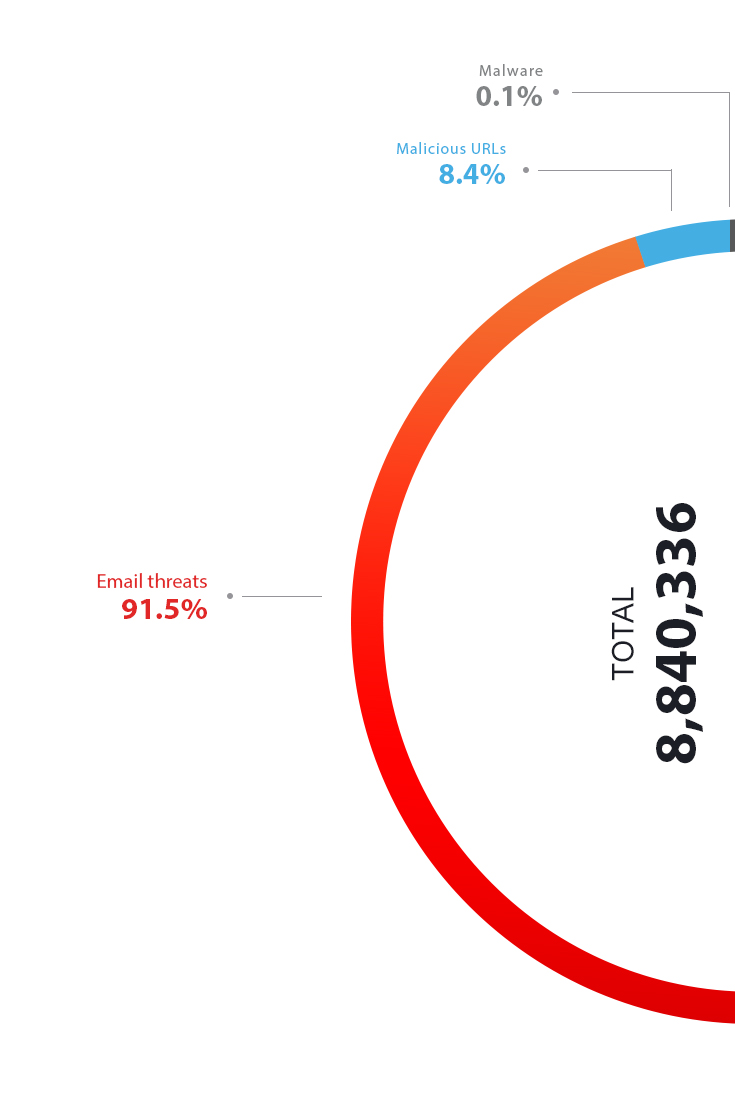
Email threats
Email was the most used entry point, making up 91.5% of detections for Covid-19-related threats. The numbers started rising in March and peaked in April. Some of the emails we observed include those that pose as health advisories or donation requests. These usually have attachments that carry malware.
4,786
4,028
897,711
2,915,129
2,440,215
1,829,324
Monthly count for Covid-19-related email threats 1H 2020
Number and distribution of Covid-19 threats, 1H 2020

WFH
With businesses shifting to remote work due to the pandemic, cybercriminals went after tools used in these environments, such as video conferencing apps. Some attacks involve crashing private video conferencing calls or baiting users with malicious domains.
We also found malware families such as a Coinminer and WebMonitor RAT bundled with video conferencing app installers, as well as a case where malware (Backdoor and Devil Shadow Botnet) disguised themselves as fake installers. Users are advised to download applications or programs only from official download centers and app stores to avoid getting compromised.
Old and new threats abound
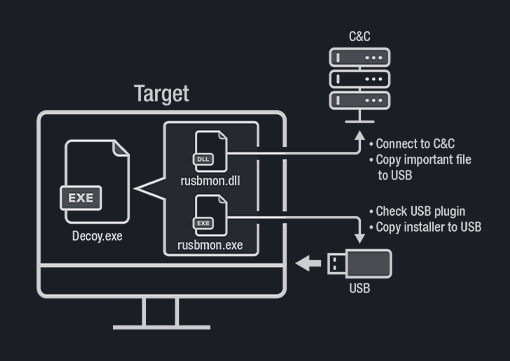
Sample scenario of an attack employing USBferry
Known and emerging actors craft targeted attacks
With or without a pandemic, it’s business as usual for threat groups, as proven by several noteworthy campaigns spotted in the first half of 2020. Both known and new threat actors made their presence felt by either showcasing novel techniques or expanding to new platforms.
Known threat groups
New threat groups
Known threat groups
zeroed in on Apple-based platforms. A recent campaign involved a one-time password app.
aimed at air-gapped systems of militaries through USBferry malware.
New threat groups
focused on gambling and betting companies in South East Asia using malicious DOCX files.
targeted Uyghur-connected individuals in Tibet, Turkey, and Taiwan by compromising their devices with ActionSpy spyware.
Ransomware operators aim at bigger targets, steal data
Ransomware detections might have decreased, but this does not mean that the malware type is any less of a threat. It is possible that ransomware attacks have gotten even stealthier as operators aim for larger targets and heftier sums.
Half-year comparison of the number of ransomware components detected in 1H 2020
We have observed an increase in ransomware demands that target companies in critical industries such as logistics, technology, and government. The average ransom demand for a Ryuk infection rose by around 62.5%.
Average ransom demand (4th quarter, 2019)
US$800,000
Average ransom demand (1st quarter, 2020)
US$1.3 million
Increase in ransom demand for Ryuk ransomware
On the other hand, some ransomware families now focus on private enterprises. Operators behind Nemty, for instance, have shifted their sights to private companies instead of public ones in their Ransomware-as-a-Service (Raas) operations.
Following last year’s trend, ransomware has also been bolstered with new abilities; currently, many ransomware families do not just encrypt files, but also steal data.
Targeted several organizations in Taiwan by infiltrating databases and email servers
Likely successor to Nemty, threatens to expose stolen data
Uncovered vulnerabilities were a pressing concern for organizations
Windows, VPN vulnerabilities
Since February of this year, Microsoft has released an estimated 100 fixes for vulnerabilities every month, with June having the highest number at 129. In previous years, the patches released rarely came close to a hundred.
Comparison of the number of updates released for Patch Tuesday for 1H 2018, 1H 2019, and 1H 2020
Other notable vulnerabilities involve virtual private networks (VPNs). The US Cybersecurity and Infrastructure Security Agency (CISA) warned about the continued exploitation of CVE-2019-19781 and CVE-2019-11510. This development might be attributed to the fact that VPNs are now more widely used for work-from-home setups.
IIoT vulnerabilities
For the first half of 2020, we have witnessed a 16% increase in the number of industrial control system (ICS) vulnerabilities disclosed to Zero Day Initiative (ZDI) compared with the same period last year.
Comparison of the number of ICS vulnerabilities disclosed to ZDI for 1H 2019, 2H 2019, and 1H 2020
A few of the notable IIoT vulnerabilities for the first half of the year include URGENT/11, which are vulnerabilities that put medical devices at risk, and Ripple20, which are vulnerabilities that can infiltrate a variety of IoT devices in diverse industries.
Published vulnerabilities
The Trend Micro™ Zero Day Initiative program published a total of 786 advisories for the first half of 2020, a staggering 74% increase from the figures from the second half of 2019. The vulnerabilities were sourced both from vendors and independent researchers.
Half-year comparison of the number of vulnerabilities disclosed via our ZDI program
Threat Landscape
Overall number of threats blocked for the first half of 2020
25,825,951,753
11,808,095,339
14,017,856,414
Email threats blocked
1,028,006,974
383,621,342
644,385,632
Malicious files blocked
969,254,232
345,935,879
623,318,353
Malicious URLs blocked
36,271,603,944
17,787,370,203
18,484,233,741
Email reputation queries
708,757,638,233
309,795,835,814
398,961,802,419
File reputation queries
1,006,547,423,405
474,130,414,689
532,417,008,716
URL reputation queries
The number of email threats, malicious files, and malicious URLs blocked saw an increase from the first to the second quarter of the year. Email, file, and URL reputation queries also saw similar spikes.
The number of phishing URLs increased in 1H 2020 compared to 2H 2019; the number of unique and non-unique phishing URLs also increased in the first half of 2020
Business email compromise (BEC) attempts increased as shown in this half-year comparison of BEC attempts.
The first half of the year has seen challenges brought about both by consistent efforts and opportunistic ventures made by threat actors. To be constantly and thoroughly prepared for the ever-evolving nature of threats, enterprises should adopt a multilayered security strategy to ensure that all possible entry points such as gateways, networks, servers, and endpoints are secured against attackers.
For deeper insight into threats and other cybersecurity issues for the first half of 2020, read our full report, “Securing the Pandemic-Disrupted Workplace: Trend Micro 2020 Midyear Cybersecurity Report”.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.

 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks