Many of the individuals and groups in underground forums go to great lengths to ensure that transactions go through without a hitch, implementing a system of checks and balances that include vetting, the use of escrow and deposits, as well as arbitrage for handling any problems. Underground forums also have strictly enforced rules that prescribe the use of polite and ethical behavior — certainly with a hint of irony when considering the unethical purpose of many of these websites. This level of trust and ethics is especially important considering these threat actors have the ability and qualifications to attack each other.
Overview of underground netiquette
Forum Hierarchy
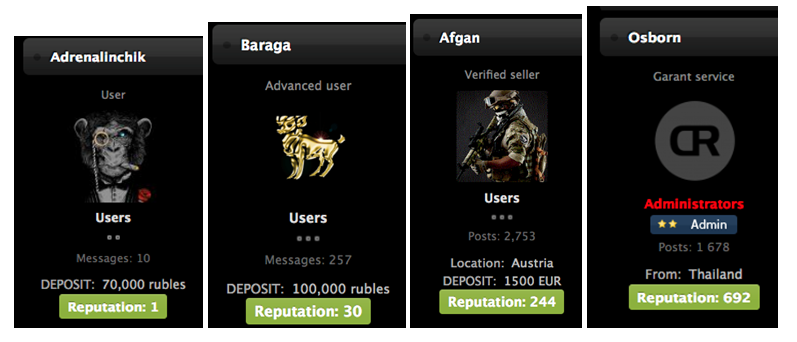
Most underground forums have hierarchy levels, which are based on several fundamental and often measurable features, like account age, activity levels, reputation and the amount of money they can provide to cover incidents.
Consequences for rule violations
The top of the totem pole — administrators and moderators — are often responsible for creating and implementing the rules. They usually deal with written or unspoken rule violations harshly, with penalties such as account bans, suspensions, and tagging accounts as, kidala (Russian for ripper or scammer).
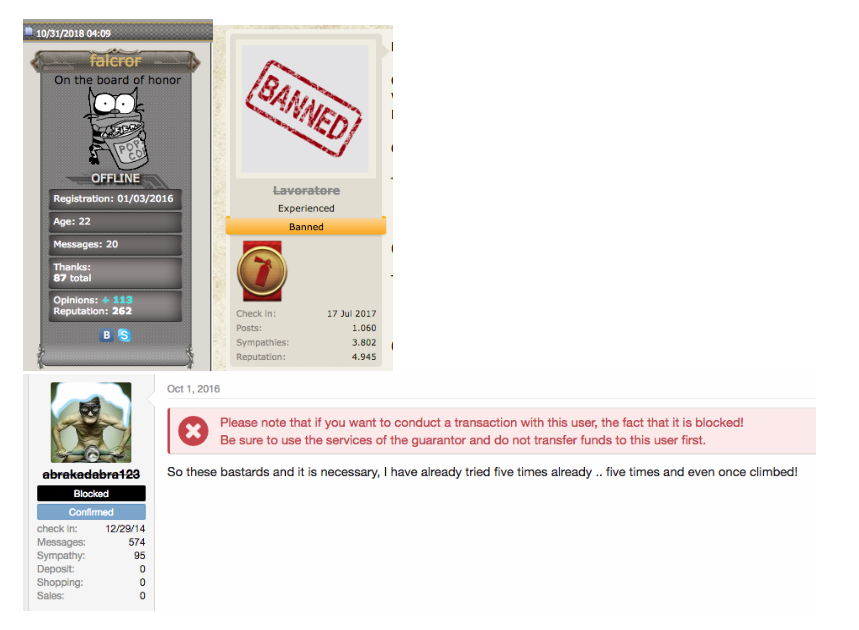
Accounts of violators aren't banned haphazardly. Moderators are required to provide reasons for a ban, typically involving rule violations or complaints from another forum actor along with evidence that a service or product has not been provided. It's generally difficult for a forum member to recover the lost reputation once labeled a troublemaker or unreliable, thus adhering to the rules is needed to remain a trusted member of the community.
Some actors attempt to get around this by using several accounts, one for reputable transactions and others used for temporary goals.
No honor among thieves: short-term gains versus long-term goals
Monetization is one of, if not the major driving force in the underground market. In many ways, it is comparable to a financial market, where some investors play the long game, investing in blue-chip stocks and generally riding the wave of volatility — always with a goal in mind. However, there are the also those who are in it for the short term, similar to investors who play short positions, sometimes by using trickery and disreputable tactics. When it comes to underground forums, these are represented by scammers who are trying out their own version of the “get-rich-quick” scheme; reputation be damned.
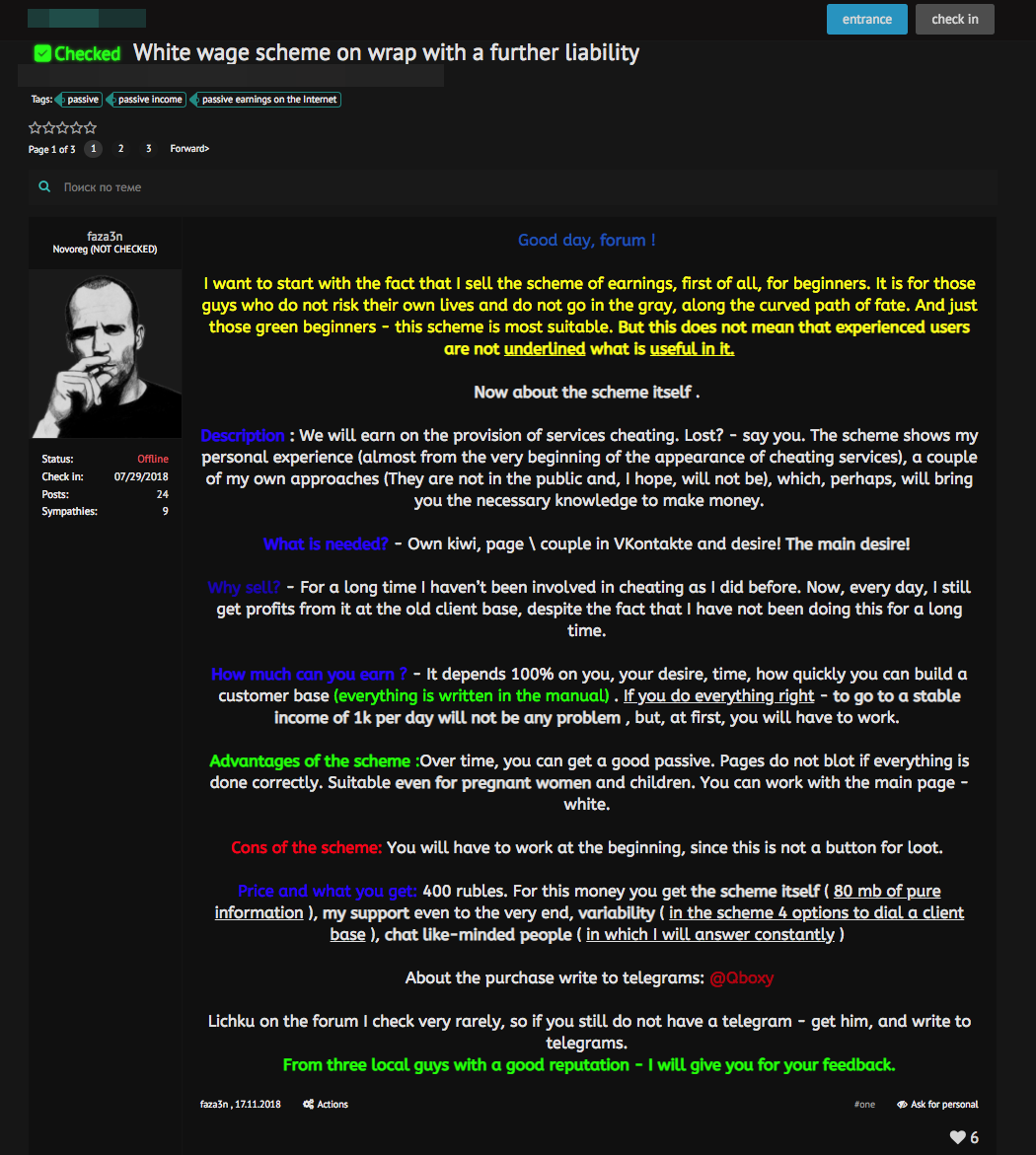
These scammers often advertise free tools or services that are rarely ever such. For example, on of the scams we found was an advertisement for free software that performs ATM jackpotting. Naive would-be-cybercriminals see the advertisement and click on the link, which redirects them to an external site embedded with info-stealing malware.
Underground forums are rife with these kinds of schemes, covering a wide array of topics including money mulling, laundering, and refund fraud, along with guides to extort or blackmail people. Some schemes are online, while others (such as those that sell fake telecom contracts in malls) are offline. Some intermediate versions of schemes — called semi-offline — exist as well.
Digging deeper: a real-world example
One particular scam that is very popular in underground forums is “step-by-step” earning guides which are often, unsurprisingly, fraudulent in nature (although not all are illegal). These products and services are usually sold to a limited number of buyers since increasing the activity’s scale could result in detection.
Traditionally, these guides have been distributed through forums. However, scammers have started using the Telegram messaging app, which has gained popularity with cybercriminals, to create hype channels before selling or monetizing the guides in an alternative way.
While monitoring these guides, we found a very interesting document (Detected as TROJAN.WIN32.FAKEMS.SK) that contained a detailed description: “How to earn money on arbitrage betting for sport events”
To an unsuspecting reader, the document would seem like a fairly comprehensive multi-page guide with an introduction, preparation, how-to and FAQ sections. However, beneath the “legitimate” exterior, it is actually a malicious file.
The document file, which is written in Russian, uses social engineering to trick the user into clicking on an attached file named “HideMe guard.exe” to install a “free VPN” application. A message box then pops up, asking the user’s permission to execute the file.
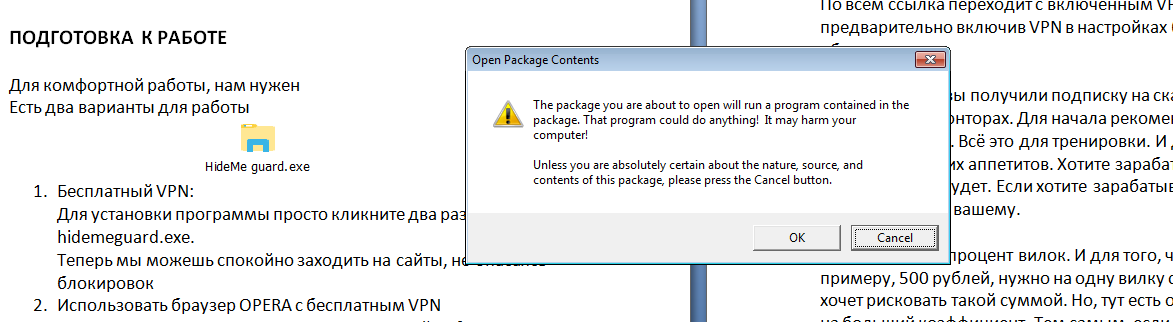
Instead of the expected free VPN, the user will instead become part of a botnet (named ACRUX as seen in its code and detected as COINMINER.WIN32.ACRUXMR.A).
The primary payload for this botnet is a cryptocurrency-mining malware, whose components it will download from a C&C server. In addition, it will also steal the credentials and other information in the infected system, hitting the affected user with a double whammy.
Conclusion
Despite the existence of a seemingly professional code of ethics in underground forums, we can still see the presence of scams in the community. The perpetrators are typically those who go for quick profits over reputation. In essence, it’s a microcosm of what really comprises the underground — for all the talk of trust and ethics, it’s still a place where cybercriminals and other unscrupulous elements exchange tools, services and ideas. It also paints a portrait of where the underground is headed, if it isn’t already there: a place where monetization has become the name of the game.
Indicators of Compromise (SHA256):
Malicious Document (Trojan.Win32.FAKEMS.SK)
- 1d26b77a30f54638e73efa86603afdcef01861d4af6f7f7359575774417e1add
ACRUX Botnet (Coinminer.Win32.ACRUXMR.A)
- 5fc1d1c152760aea6912e4378f2c5041e1ed189c67f293ec461a9216e2c88054
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Unveiling AI Agent Vulnerabilities Part III: Data Exfiltration
- Unveiling AI Agent Vulnerabilities Part II: Code Execution
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks