What Is Spear Phishing ?
Stop more threats with Trend Micro Email Security—advanced protection for your inbox!
Spear Phishing Meaning
Spear Phishing stands out as one of the most dangerous and targeted forms of cyber-attacks. Unlike regular phishing attacks, which cast a wide net in hopes of catching unsuspecting victims, spear phishing is a highly personalized and targeted form of a phishing attack that targets a user rather than a network. Attackers use detailed information about their victims to craft convincing messages that trick them into divulging sensitive information or clicking on malicious links.
How Spear Phishing Attacks Works
Spear phishing attacks are carefully planned and executed. The normal process of Spear Phishing can include the following:
Information Gathering
Attackers begin by gathering information about their targets. They will use resources such as social media, company websites or other publicly available sources to gather information about the target and will look for details such as email addresses, job titles, interests, and relationships.
Personalization of Messages
After gathering information about the target Attackers will craft a personalized message/email. These messages are designed to appear as if they come from a trusted source, such as a colleague, business partner, or even a superior. Personalization makes the messages more convincing and increases the likelihood that the victim will fall for the scam.
Social Engineering Techniques
Attackers use Social Engineering techniques to manipulate their targets psychologically to divulge sensitive information, click on malicious URLs or other actions that are harmful to themselves or their organization. They may create a sense of urgency, fear, or curiosity to prompt immediate action. Common tactics include fake urgent requests from a boss, invoices from suppliers, or notifications from trusted services.
Execution
Once the message is created, it is sent to the target. The message may contain a malicious link that leads to a phishing site designed to steal credentials, or it may include an attachment that, when opened, installs malware on the victim's device. In some cases, the attacker may simply ask for sensitive information directly.
Common Targets and Consequences
Typical Targets
Spear Phishers will usually target a particular person or organization with access to valuable information or assets, such as:
Corporate Executives: High-level executives are prime targets due to their access to sensitive company information and their status within an organization, this is also known as a whaling attack.
Specific Employees: Someone that has access to valuable information within an organization such as employees that work in finance, human resources, and IT departments.
Specific Industries: Industries like government, finance and healthcare are common targets as the rewards would be enormous if a Spear Phishing attack is successful.
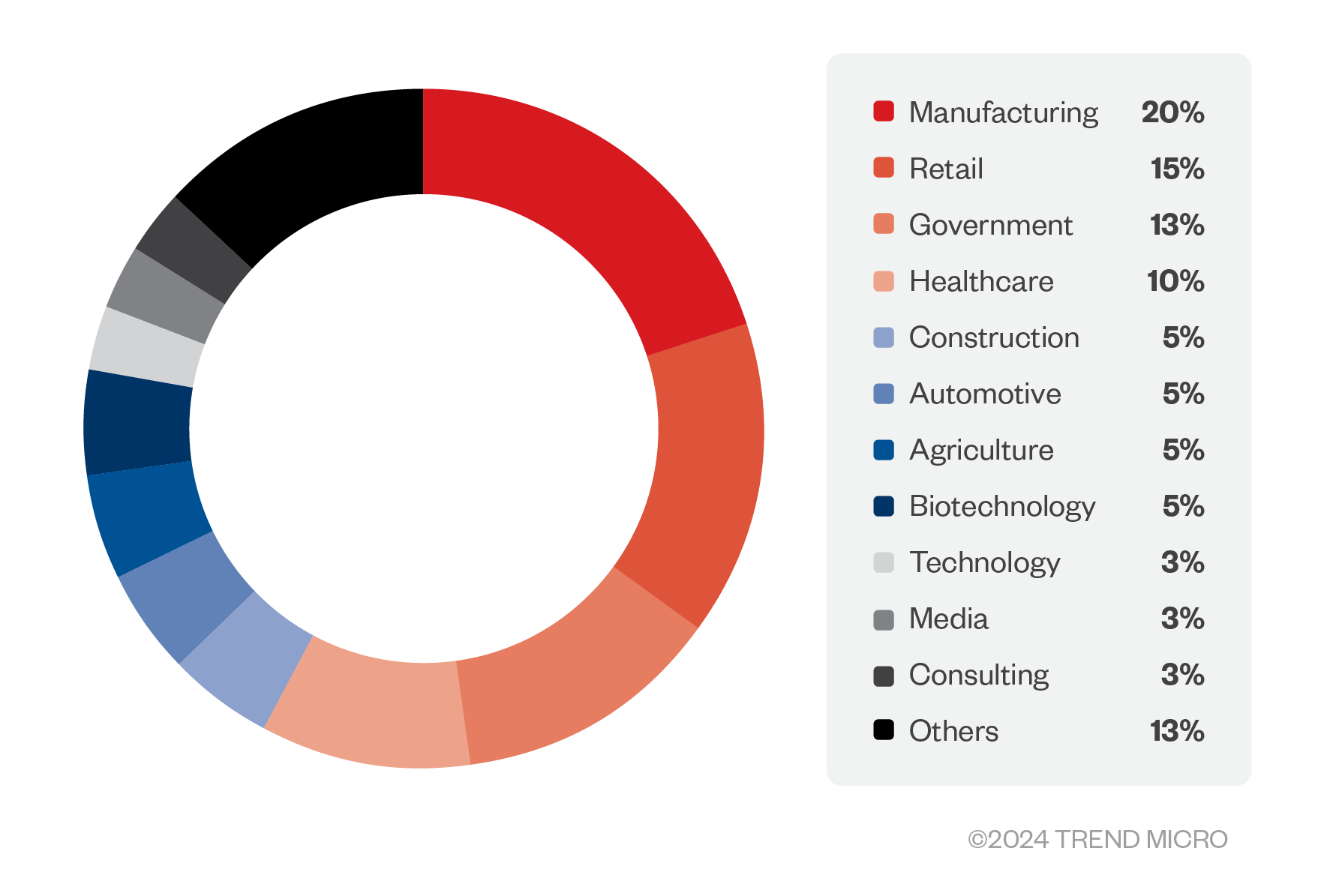
Figure 1. Distribution of the attacks by industry
Potential Consequences
- Data Breaches: Sensitive information, such as personal data, financial information, and intellectual property can be stolen.
- Financial Loss: Attackers may gain access to bank accounts, initiate fraudulent transactions, or trick victims into transferring money.
- Reputational Damage: Organizations that fall victim to spear phishing attacks may suffer reputational harm, losing the trust of customers, partners, and stakeholders.
- Operational Disruption: Malware installed through spear phishing can disrupt business operations, leading to downtime and loss of productivity.
How to Recognize a Spear Phishing Attack
It can be hard to spot Spear Phishing attacks because of their personalized nature, but there are several red flags to look out for:
Unexpected Requests
If you receive an urgent or unexpected communication that requests some kind of sensitive information you should verify it separately before responding.
Unusual Language or Tone
Even well-crafted spear phishing emails can contain subtle language or tone inconsistencies. Look for unusual phrases, grammatical errors, or tone shifts that don't match the sender's typical communication style.
Discrepancies in Sender Details
Check the sender's email address and domain carefully. Spear phishing emails often come from addresses that look like legitimate ones but contain slight variations.
Suspicious Links and Attachments
You should check a link by hovering over it to see the full URL before clicking. Unsolicited attachments should not be opened without proper verification.
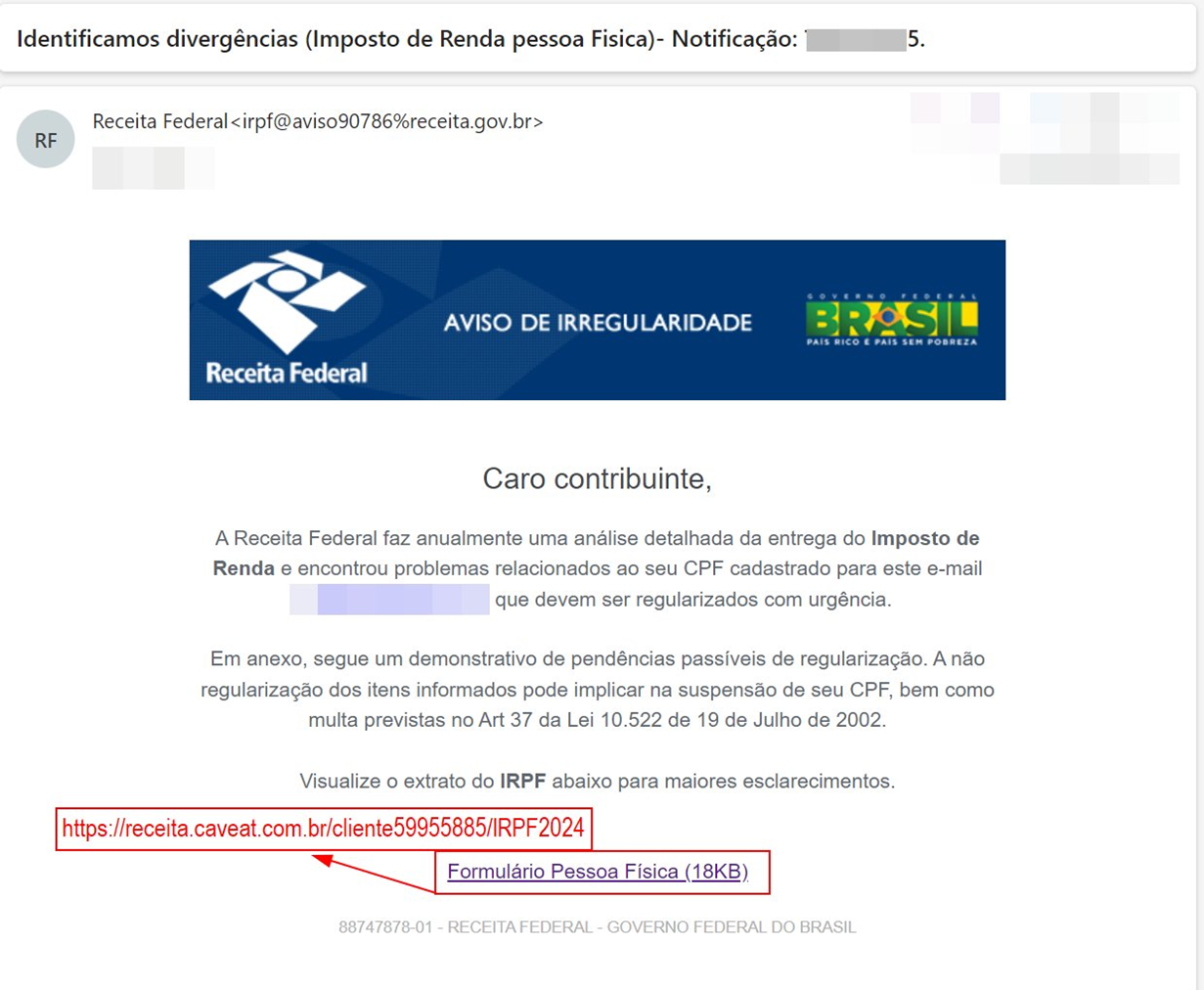
Figure 2. Example of the spear phishing email whose final payload is the Astaroth malware
Preventive Measures and Best Practices
To protect against spear phishing, individuals and organizations should adopt thorough preventive measures, such as:
Employee Training
Spear Phishing targets humans not systems so it is important that you train your staff to recognize and respond to Spear Phishing attacks. Use simulated phishing exercises to test their awareness and improve their detection skills.
Robust Email Security Protocols
Use advanced email security protocols, such as spam filters, email authentication (DKIM, SPF, DMARC), and anti-phishing solutions. These tools can help to filter out malicious emails before they reach users.
Multi-Factor Authentication
Enable multi-factor authentication (MFA) for accessing sensitive systems and data. MFA adds an extra layer of security, making it more difficult for attackers to gain unauthorized access.
Regular Security Awareness Programs
Conduct ongoing security awareness programs to keep employees informed about the latest spear phishing tactics and best practices for staying safe online.
Tools and Technologies to Combat Spear Phishing
Advanced Email Filtering Systems
Use modern email filtering systems that use machine learning and artificial intelligence to detect and block spear phishing emails. These systems analyze email content, sender reputation, and other factors to identify potential threats.
Anti-Phishing Software
Use anti-phishing software that can detect and block phishing attempts in real-time. These solutions will often include browser extensions and endpoint protection to safeguard against malicious links and attachments.
Threat Intelligence Platforms
Use threat intelligence platforms to stay up to date on new spear phishing threats and attack patterns. These platforms provide insights and alerts based on global threat data, helping organizations to proactively defend against new threats.
The Role of Incident Response
Having a well-defined incident response plan is crucial when dealing with spear phishing attacks:
Identifying and Containing the Threat
Quickly identify and contain the threat to prevent further damage. This may involve isolating affected systems, blocking malicious IP addresses, and changing compromised passwords.
Notifying Affected Parties
You should notify all affected parties about a breach. It is important to be transparent in this scenario so others can take necessary precautions.
Implementing Remedial Actions
Take corrective actions to address the vulnerabilities exploited by the attack. This may include updating security protocols, patching software, and enhancing email filtering systems.
Future Trends in Spear Phishing
AI and Machine Learning
Spear Phishers are using AI and machine learning to create more convincing spear phishing messages. This results in the creation of highly personalized and sophisticated attacks that are more difficult to detect.
IoT and Cloud Security
As the Internet of Things (IoT) and cloud services have become more popular, attackers are targeting these environments. Spear phishing techniques are evolving to take advantage of vulnerabilities in connected devices and cloud infrastructure.
Advanced Persistent Threats (APTs)
APTs use sophisticated techniques to infiltrate and remain undetected within networks. Spear phishing is often the initial vector for these attacks, highlighting the need for continuous adaptation of defense strategies.
Continuous Penetration Testing
Continuous penetration testing and red teaming exercises help organizations stay ahead of spear phishing threats. These proactive measures identify and address vulnerabilities in real-time, enhancing overall security.
Trend Micro Email Security Solution
Trend Micro™ Email Security screens out malicious senders and analyzes content to filter out spam. It examines sender authenticity and reputation and defends against malicious URLs.
Cross-generational threat defense techniques bolster protection against threats, establishing visibility and control across evolving threat landscapes.
Related information about Spear Phishing

Example of Spear Phishing Attack using Malware
Trend Micro researchers have uncovered a surge of malicious activities involving a threat actor group that we track as Water Makara.

SideWinder Uses South Asian Issues for Spear Phishing
While tracking the activities of the SideWinder group, we identified a server used to deliver a malicious LNK file and host multiple credential phishing page
