Dating Spam Arrives with Backdoor Application
March 16, 2011
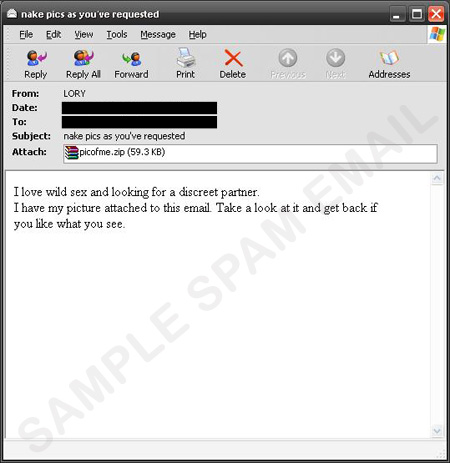
One of the easiest ways for cybercriminals to lure users into their traps is to appeal to human curiosity. In the case of a recent dating spam sample, recipients are enticed to open the attached .ZIP file with the promise of nude photos. Once users open the file, PICOFME.ZIP, they will instead see a .SCR file detected as BKDR_IRCBOT.HIK.
Upon installation, the backdoor application drops copies of itself on the affected system and opens TCP port 6667. It then proceeds to connect to a URL to receive commands from a remote malicious user.
Following commands sent by a remote malicious user, this backdoor application can download and execute its updated copy or other malware, gather system information, and stop or start services. It also joins the IRC channel #AllNiteCafe.
Trend Micro advises users to simply delete such emails, especially if they come from unknown senders, to prevent system infection.
Upon installation, the backdoor application drops copies of itself on the affected system and opens TCP port 6667. It then proceeds to connect to a URL to receive commands from a remote malicious user.
Following commands sent by a remote malicious user, this backdoor application can download and execute its updated copy or other malware, gather system information, and stop or start services. It also joins the IRC channel #AllNiteCafe.
Trend Micro advises users to simply delete such emails, especially if they come from unknown senders, to prevent system infection.
SPAM BLOCKING DATE / TIME: March 16, 2011 GMT-8
TMASE INFO
- ENGINE:6.5
- PATTERN:8014
