Spam, Scams and Other Social Media Threats
Data de publicação: terça-feira, 29 de março de 2011
People’s lives are becoming more intertwined due to online interactions over time. While the Internet provides several options for users to create and maintain relationships, social media sites make it even easier to do so. Unfortunately, time spent on social media sites opens windows of opportunity for cybercriminals and online threats.
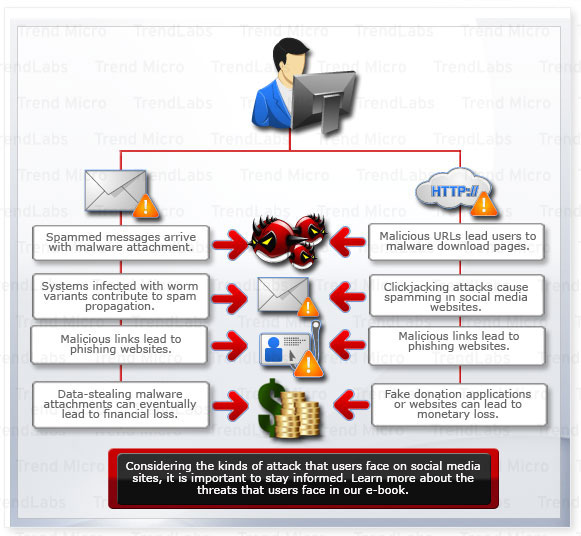
With a captured audience and various means by which cybercriminals can initiate contact with users, it is not surprising that social media sites are constant targets for spam, scams and other attacks. Furthermore, there are now several options for creating and sharing content. Users can post 140-character status updates, links, images and videos. Sending private or direct messages are likewise possible, a feature that attackers did not lose time in exploiting.
How do these attacks start? These attacks primarily proliferate on social media websites such as Facebook and Twitter, both of which currently have millions of active users. Their popularity makes them perfect venues for executing cybercriminal activities.
Users typically encounter social media threats when they log in to the social networking sites. They may encounter the malicious posts while browsing people's profiles or while visiting social media sites. These posts typically include malicious URLs that can lead to malware download pages and/or phishing sites or can trigger spamming routines.
However, social media threats are not contained within the social networking sites’ walls. Public interest in social media is in itself a powerful tool that cybercriminals have repeatedly used to their advantage. Sending spammed messages purportedly from a legitimate social media site is a common social engineering tactic.
What types of attacks do users encounter?
As previously mentioned, users now have several options when it comes to creating posts. Sadly, attackers are also using them to come up with different types of threats on social media sites:
Facebook
How do these attacks affect users?
In addition to the usual consequences like spamming, phishing attacks and malware infections, the greater challenge that social media sites pose for users has to do with keeping data private. The ultimate goal of social media is to make information accessible to others and to enable communication among users.
Unfortunately, cybercrime thrives on publicly available information that can be used to carry out targeted attacks. Some users falsely believe that cybercriminals will not gain anything from stealing their social media credentials. What they don’t realize is that once attackers gain access to one of their accounts, they can easily find a way to mine more information and to use this to access their other accounts. The same is true for corporate accounts, which are publicly available on sites like LinkedIn. In fact, mapping an organization’s DNA using information from social media sites is actually easier than most people think.
Are Trend Micro product users protected from these attacks?
Yes, the Trend Micro™ Smart Protection Network™ email reputation technology prevents spammed messages from even reaching users’ inboxes. Web reputation technology blocks access to malicious sites that host malware and that serve spam. File reputation technology likewise prevents the execution of and deletes all known malicious files from users’ systems.
What can users to do to prevent these attacks from affecting their systems?
Basic online precautionary measures for Web and email still apply to avoid becoming a victim of social media threats. Users simply need to be more wary of bogus notifications that take on the guise of legitimate prompts from the popular social media sites. When browsing users' profiles or pages, they should also keep in mind that not everything on these pages is safe. Despite the circle of trust that social media sites create, users should not forget that cybercriminals are constantly lurking behind virtual corners, just waiting for opportunities to strike.
In addition, users should exert effort to protect the privacy of their data. It is best to adapt the mindset that any information posted online is publicly available. Apart from exercising caution when posting on personal accounts, users should also avoid sharing sensitive business information via social media private messages or chats. Doing so can easily lead to data leakage once their accounts are hacked.
To prevent this, users need to know and understand the security settings of the social media sites they become members of. For instance, Facebook allows users to create lists and to control the types of information that people who belong to certain lists can see. Finally, enabling the secure connection options (HTTPS) for both Facebook and Twitter can help add a layer of protection via encrypted pages.
Expert Insights
“KOOBFACE knows: KOOBFACE has the capability to steal whatever information is available in your Facebook, MySpace, or Twitter profile. The profile pages of these social networking sites may contain information about one’s contact details (address, email, phone), interests (hobbies, favorite things), affiliations (organizations, universities), and employment (employer, position, salary). So beware, KOOBFACE knows a lot!” —Ryan Flores, Trend Micro Senior Threat Researcher
"It is also interesting to note that since social networking sites have thousands or even millions of user profiles, locating a suspicious account is difficult, especially if cybercriminals take time out to cover their tracks.” —Ranieri Romera, Trend Micro Senior Threat Researcher
“If you see that the messages and websites contained several glaring grammatical errors—a common issue for phishing attacks in general—this should warn you that the site you’re visiting is not legitimate.”—Marco Dela Vega, Trend Micro Threats Researcher
“Another aspect of this privacy issue is how users tend to behave online. With or without Facebook, unenlightened users will make a mistake and divulge private information no matter what social network you drop them in to.”—Jamz Yaneza, Trend Micro Threat Research Manager
“Social networking accounts are even more useful for cybercriminals because besides plundering your friends’ email addresses, the bad guys can also send bad links around and try to steal the social networking credentials of your friends. There is a reason why there is a price for stolen social networking accounts.”—David Sancho, Trend Micro Senior Threat Researcher
With a captured audience and various means by which cybercriminals can initiate contact with users, it is not surprising that social media sites are constant targets for spam, scams and other attacks. Furthermore, there are now several options for creating and sharing content. Users can post 140-character status updates, links, images and videos. Sending private or direct messages are likewise possible, a feature that attackers did not lose time in exploiting.
How do these attacks start? These attacks primarily proliferate on social media websites such as Facebook and Twitter, both of which currently have millions of active users. Their popularity makes them perfect venues for executing cybercriminal activities.
Users typically encounter social media threats when they log in to the social networking sites. They may encounter the malicious posts while browsing people's profiles or while visiting social media sites. These posts typically include malicious URLs that can lead to malware download pages and/or phishing sites or can trigger spamming routines.
However, social media threats are not contained within the social networking sites’ walls. Public interest in social media is in itself a powerful tool that cybercriminals have repeatedly used to their advantage. Sending spammed messages purportedly from a legitimate social media site is a common social engineering tactic.
What types of attacks do users encounter?
As previously mentioned, users now have several options when it comes to creating posts. Sadly, attackers are also using them to come up with different types of threats on social media sites:
- Likejacking attacks: The idea behind these attacks is simple: Cybercriminals create interesting posts that act as baits. Typical social engineering tactics include the use of intriguing posts that ride on seasonal events, celebrity news and even disasters.
Users who click the links then inadvertently act as accomplices to the attacker because the malicious scripts would automatically re-posts the links, images or videos on their contacts’ walls. A more popular version of this attack causes user profiles to "like" a Facebook page without their consent. In some instances, spammed posts eventually lead users to survey sites from which cybercriminals can profit. - Rogue applications: Facebook applications enable users to play games, to add profile features and to do more stuff. Its open platform allows practically anyone to develop and submit applications that users can access. Of course, cybercriminals also use this opportunity to create rogue applications that may be used for spamming posts or for phishing attacks.
- Attacks via Facebook chat: Facebook’s built-in chat feature makes it easier for users and cybercriminals alike to strike up conversations with friends and to communicate with their contacts in real time. In previous attacks, chat messages were used to spread malware and to promote phishing applications
- Spammed Tweets: Despite the character limit in Twitter, cybercriminals have found a way to actually use this limitation to their advantage by creating short but compelling posts with links. Examples include promotions for free vouchers, job advertisement posts and testimonials for effective weight loss products. A Twitter kit was even created to make spamming even easier for cybercriminals to do.
- Malware downloads: Apart from using Twitter for basic spamming activities, it has also been used to spread posts with links to malware download pages. There have been several incidents to date, including posts that used blackhat search engine optimization (SEO) tricks to promote FAKEAV and backdoor applications, a Twitter worm that sent direct messages, and even malware that affected both Windows and Mac OSs. The most notorious social media malware, however, is still KOOBFACE, which targeted both Twitter and Facebook. Its more popular social engineering tactic is the use of video-related posts, which eventually lead users to a fake YouTube page where they could download the malicious file. It also uses blackhat SEO tactics, which are usually based on trending topics on Twitter.
- Twitter bots: As if propagating spam and malware isn’t enough, cybercriminals also found a way to use Twitter to manage and control botnet zombies. Compromised machines infected with WORM_TWITBOT.A can be controlled by the bot master running the Mehika Twitter botnet by simply sending out commands through a Twitter account. Using the microblogging site has its advantages and disadvantages but it is interesting to see how cybercriminals managed to use a social media site in lieu of a traditional command-and-control (C&C) server.
How do these attacks affect users?
In addition to the usual consequences like spamming, phishing attacks and malware infections, the greater challenge that social media sites pose for users has to do with keeping data private. The ultimate goal of social media is to make information accessible to others and to enable communication among users.
Unfortunately, cybercrime thrives on publicly available information that can be used to carry out targeted attacks. Some users falsely believe that cybercriminals will not gain anything from stealing their social media credentials. What they don’t realize is that once attackers gain access to one of their accounts, they can easily find a way to mine more information and to use this to access their other accounts. The same is true for corporate accounts, which are publicly available on sites like LinkedIn. In fact, mapping an organization’s DNA using information from social media sites is actually easier than most people think.
Are Trend Micro product users protected from these attacks?
Yes, the Trend Micro™ Smart Protection Network™ email reputation technology prevents spammed messages from even reaching users’ inboxes. Web reputation technology blocks access to malicious sites that host malware and that serve spam. File reputation technology likewise prevents the execution of and deletes all known malicious files from users’ systems.
What can users to do to prevent these attacks from affecting their systems?
Basic online precautionary measures for Web and email still apply to avoid becoming a victim of social media threats. Users simply need to be more wary of bogus notifications that take on the guise of legitimate prompts from the popular social media sites. When browsing users' profiles or pages, they should also keep in mind that not everything on these pages is safe. Despite the circle of trust that social media sites create, users should not forget that cybercriminals are constantly lurking behind virtual corners, just waiting for opportunities to strike.
In addition, users should exert effort to protect the privacy of their data. It is best to adapt the mindset that any information posted online is publicly available. Apart from exercising caution when posting on personal accounts, users should also avoid sharing sensitive business information via social media private messages or chats. Doing so can easily lead to data leakage once their accounts are hacked.
To prevent this, users need to know and understand the security settings of the social media sites they become members of. For instance, Facebook allows users to create lists and to control the types of information that people who belong to certain lists can see. Finally, enabling the secure connection options (HTTPS) for both Facebook and Twitter can help add a layer of protection via encrypted pages.
Expert Insights
“KOOBFACE knows: KOOBFACE has the capability to steal whatever information is available in your Facebook, MySpace, or Twitter profile. The profile pages of these social networking sites may contain information about one’s contact details (address, email, phone), interests (hobbies, favorite things), affiliations (organizations, universities), and employment (employer, position, salary). So beware, KOOBFACE knows a lot!” —Ryan Flores, Trend Micro Senior Threat Researcher
"It is also interesting to note that since social networking sites have thousands or even millions of user profiles, locating a suspicious account is difficult, especially if cybercriminals take time out to cover their tracks.” —Ranieri Romera, Trend Micro Senior Threat Researcher
“If you see that the messages and websites contained several glaring grammatical errors—a common issue for phishing attacks in general—this should warn you that the site you’re visiting is not legitimate.”—Marco Dela Vega, Trend Micro Threats Researcher
“Another aspect of this privacy issue is how users tend to behave online. With or without Facebook, unenlightened users will make a mistake and divulge private information no matter what social network you drop them in to.”—Jamz Yaneza, Trend Micro Threat Research Manager
“Social networking accounts are even more useful for cybercriminals because besides plundering your friends’ email addresses, the bad guys can also send bad links around and try to steal the social networking credentials of your friends. There is a reason why there is a price for stolen social networking accounts.”—David Sancho, Trend Micro Senior Threat Researcher
