Luckycat Leads to Attacks Against Several Industries
Data de publicação: quinta-feira, 5 de abril de 2012
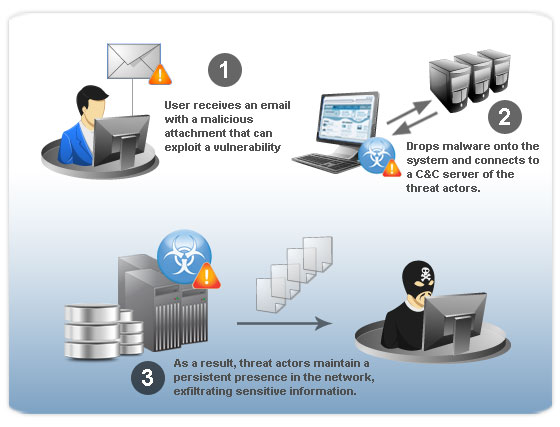
Reports of highly targeted attacks have dramatically increased in number. Highly targeted attacks differ from traditional threats as these attacks are similar to “cyber espionage.” Attackers work hard to make highly targeted attacks infiltrate a network and maintain its persistent presence to extract sensitive information.
What is Luckycat?
Luckycat is the name of a campaign that targeted Indian military research institutions, entities in Japan, as well as the Tibetan community. The campaign targeted particular industries such as aerospace, energy, engineering, shipping, and military research.
How did Luckycat start?
The campaign starts with email messages and/or malicious documents that claim to contain important information.
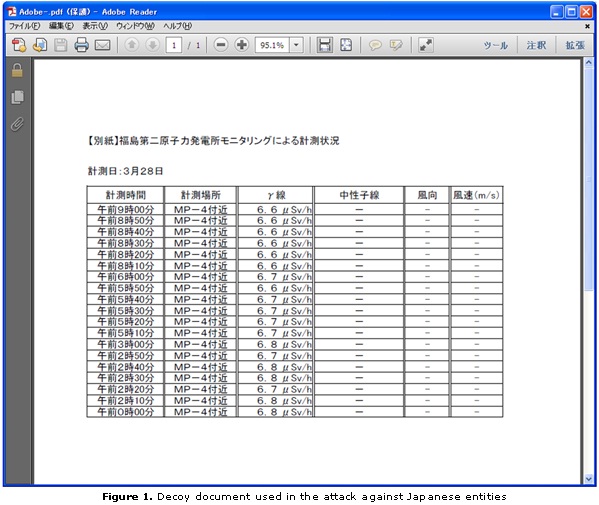
Below are a few examples of the different lures used in the Luckycat campaign. It should be noted that the content of these messages or documents often change depending on the targeted entity. For instance, Japan-based organizations received an attachment about measurement results of a radiation dose in Japan.
Entities in India, meanwhile, received a malicious document containing information on India's Ballistic Missile Defense System.

Others received malicious email with attachments that leverage Tibetan themes.
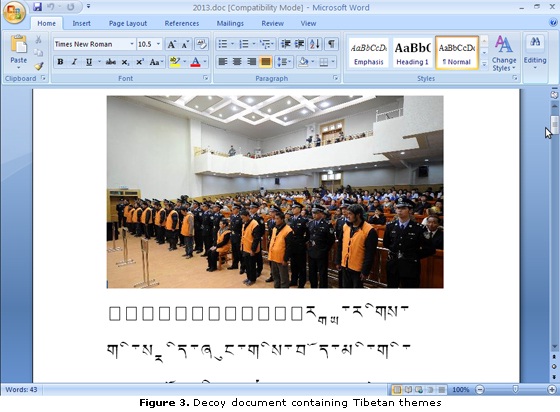
The malicious attachments illustrated above often contain malicious code that exploits certain vulnerabilities to drop malware, such as TROJ_WIMMIE.C, onto the target's system.
What happens when the malware is dropped onto the system?
TROJ_WIMMIE.C drops and executes VBS_WIMMIE.SMC onto the infected system. VBS_WIMMIE.SMC writes a malicious Windows Management Instrumentation (WMI) JavaScript. The WMI is a feature that is used for remote systems management. One of the capabilities of the WMI is to run commands on the managed systems, making it possible to be manipulated by attackers or threat actors.
The malicious JavaScript connects to a command-and-control (C&C) server to possibly download other malicious files and execute commands. VBS_WIMMIE.SMC registers a script that works as a backdoor to the WMI event handler and deletes files associated with it or TROJ_WIMMIE.C. As a result, the backdoor is effectively hidden from the user. It cannot be detected by antivirus software through simple file scanning.
Which vulnerabilities does this campaign take advantage of?
Most samples exploited CVE-2010-3333, otherwise known as the “Rich Text Format (RTF) Stack Buffer Overflow Vulnerability,” which causes a buffer overflow in the Microsoft Word RTF parser when the “pFragments” shape property is given a malformed value.
Other samples exploited the following vulnerabilities in Adobe Reader and Flash Player:
Is this an isolated incident?
Careful analysis of the Luckycat campaign has shown that the attackers behind Luckycat used several malware families that were used in previous campaigns. There are also similarities with regard to the targets. In this case, the targets are Tibetan activists and industries in India and Japan.
Are general users affected by this campaign?
The ordinary home user is not affected by Luckycat. Highly targeted attacks like Luckycat are focused on specific industries or communities. However, users such as employees of a company pose an entirely different matter. Humans are considered the weakest link in an organization yet an empowered human can be a core component for an organization’s defensive strategy.
How can organizations defend themselves from attacks like Luckycat?
Sufficiently motivated threat actors can penetrate networks that use advanced security measures. Standard and relevant preventive measures include solid patch management, endpoint and network security, and firewall use. However, organizations should employ local and external threat intelligence to detect threats. A good cleanup strategy should also be effective.
Organizations should also educate employees about social engineering schemes. As mentioned in the previous section, an empowered human can be a core component for an organization’s defensive strategy. It is not enough to rely on security-related policies and procedures. Employees should also be educated so that they develop a trained eye for reporting potential threats.
Finally, organizations should create data loss prevention (DLP) strategies, since the main goal of a targeted attack is acquiring sensitive data.
What are the steps Trend Micro has taken to address this threat?
The following table summarizes the Trend Micro solutions for the components of the Luckycat campaign.
The following table summarizes the Trend Micro solutions for the components of the Luckycat campaign.
| Attack Component | Protection Technology | Trend Micro Solution |
| HTTP C&C communication fingerprint count.php?m=c&n=[HOSTNAME]_[MAC_ADDRESS]_[CAMPAIGN_CODE]@ | Web Reputation | Endpoint (Titanium, Worry-Free Business Security, OfficeScan) Server (Deep Security) Messaging (InterScan Messaging Security, ScanMail Suite for Microsoft Exchange) Network (Deep Discovery) Gateway (InterScan Web Security, InterScan Messaging Security) Mobile (Mobile Security) |
| TROJ_WIMMIE VBS_WIMMIE |
File Reputation (Antivirus/Anti-malware) | Endpoint (Titanium, Worry-Free Business Security, OfficeScan) Server (Deep Security) Messaging (InterScan Messaging Security, ScanMail Suite for Microsoft Exchange) Network (Deep Discovery) Gateway (InterScan Web Security, InterScan Messaging Security) Mobile (Mobile Security) |
| Attack Component | Protection Technology | Trend Micro Solution |
| CVE-2010-3333 CVE-2010-2883 CVE-2010-3654 CVE-2011-0611 CVE-2011-246 |
Vulnerability Shielding / Virtual Patching | Server (Deep Security) Endpoint (OfficeScan with Intrusion Defense Firewall Plug-In) For CVE-2010-3333: Rule #1004498 (Microsoft Word .RTF File Parsing Stack Buffer Overflow Vulnerability) For CVE-2010-2883: Rule #1004393 (Adobe Reader SING Table Parsing Vulnerability) Rule #1004113 (identified malicious .PDF file) Rule #1004315 (identified malicious .PDF file - 3) For CVE-2010-3654: Rule #1004497 (Adobe Flash Player Unspecified Code Execution Vulnerability) For CVE-2011-0611: Rule #1004801 (Adobe Flash Player .SWF File Remote Memory Corruption Vulnerability) Rule #1004114 (identified malicious .SWF file) Rule #1004647 (restrict Microsoft Office file with embedded .SWF file) For CVE-2011-2462: Rule #1004871 (Adobe Acrobat/Reader U3D Component Memory Corruption Vulnerability) Rule #1004873 (Adobe Acrobat/Reader U3D Component Memory Corruption) |
| Attack Component | Protection Technology | Trend Micro Solution |
| {BLOCKED}e.1x.biz {BLOCKED}sbrain.shop.co {BLOCKED}llworldcup.website.org {BLOCKED}hales.shop.co {BLOCKED}2325.x.gg {BLOCKED}chow.shop.co {BLOCKED}hop.kilu.org {BLOCKED}t.shop.co {BLOCKED}orts.website.org {BLOCKED}rs.shop.co {BLOCKED}ort.shopping2000.com {BLOCKED}ll.all.co.uk {BLOCKED}uipment.website.org {BLOCKED}sport.website.org {BLOCKED}ool.website.org {BLOCKED}oomsite.com {BLOCKED}3.gwchost.com {BLOCKED}ees.net {BLOCKED}een.0fees.net {BLOCKED}nnets.0fees.net {BLOCKED}memaster.kilu.org {BLOCKED}choice.shop.co {BLOCKED}hecle.shop.co {BLOCKED}ith.0fees.net |
Web, Domain, and IP Reputation | Endpoint (Titanium, Worry-Free Business Security, OfficeScan) Server (Deep Security) Messaging (InterScan Messaging Security, ScanMail Suite for Microsoft Exchange) Network (Deep Discovery) Gateway (InterScan Web Security, InterScan Messaging Security) Mobile (Mobile Security) |
FROM THE FIELD: EXPERT INSIGHTS
“It is more useful to think of highly targeted attacks as campaigns—a series of failed and successful attempts to compromise a target’s network over a certain period of time. The attackers, in fact, often keep track of the different attacks within a campaign in order to determine which individual attack compromised a specific victim’s network. As the attackers learn more about their targets from open source research—relying on publicly available information, as well as previous attacks, the specificity of the attacks may sharply increase.” –Forward-Looking Threat Research Team