MJ Spam Attack Results in Double Malware Infection
Data de publicação: quarta-feira, 6 de janeiro de 2010
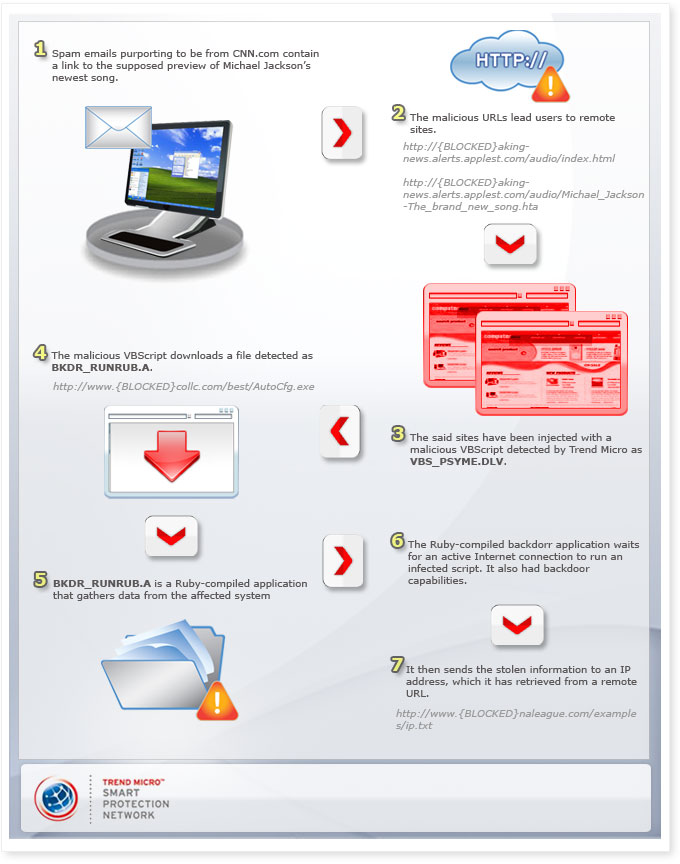
How does this threat get into users' systems?
This threat arrives via spammed messages containing a malicious link that led users to a site injected with a malicious VBScript detected by Trend Micro as VBS_PSYME.DLV.
What social-engineering ploy does this malware use?
This threat rides on Michael Jackson's popularity to trick users into clicking the link embedded in the spammed messages sent a day before the release of his new song.
Who is at risk?
Internet users who are not careful about clicking links embedded in email messages, particularly those coming from unknown senders, are at risk. Michael Jackson fans who are curious to know the latest news on the demised icon are particularly vulnerable as well.
How does this threat affect users?
VBS_PSYME.DLV downloads BKDR_RUNRUB.A, which gathered data from affected systems and sent them to a remote IP address. The malware also has backdoor capabilities that made it capable of retrieving local computer names, user names, and IP addresses and of retrieving a file from a remote URL without the users' knowledge.
This threat arrives via spammed messages containing a malicious link that led users to a site injected with a malicious VBScript detected by Trend Micro as VBS_PSYME.DLV.
What social-engineering ploy does this malware use?
This threat rides on Michael Jackson's popularity to trick users into clicking the link embedded in the spammed messages sent a day before the release of his new song.
Who is at risk?
Internet users who are not careful about clicking links embedded in email messages, particularly those coming from unknown senders, are at risk. Michael Jackson fans who are curious to know the latest news on the demised icon are particularly vulnerable as well.
How does this threat affect users?
VBS_PSYME.DLV downloads BKDR_RUNRUB.A, which gathered data from affected systems and sent them to a remote IP address. The malware also has backdoor capabilities that made it capable of retrieving local computer names, user names, and IP addresses and of retrieving a file from a remote URL without the users' knowledge.