Blackhole Exploit Kit Spam Run Using Wells Fargo
Data de publicação: 09 setembro 2012
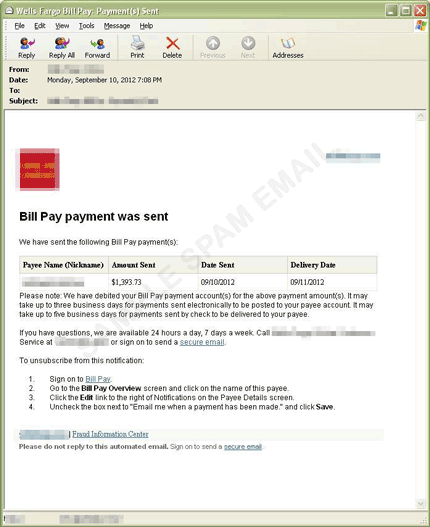
Spammers use an email notification supposedly from Wells Fargo, making it appear that the notification is indeed from the said company. The message intends to lure users into clicking a malicious link found in the email message. Once the URL is clicked, it redirects to a site hosting a malicious JavaScript. The redirect page is pictured below:

While users wait for the website to load, the running script redirects to a blackhole exploit kit server. An exploit code starts to execute to deliver a .JAR file, which then downloads other malicious files on the affected computer.
Trend Micro™ Smart Protection Network™ protects users from this threat by blocking the spam mail samples, as well as any related malicious URLs and malware.
Data/Hora do bloqueio de spam: 09 setembro 2012 GMT-8
TMASE
- Versão do mecan
- Patrón TMASE: 9174