ANDROIDOS_DORDRAE.M
Information Stealer, Malicious Downloader
Android OS


Threat Type: Trojan
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This malware variant is related to the Android malware, DroidDreamLight, which steals mobile-specific data. The detected files are Trojanized Android applications which are hosted in the Android Market and infected almost a hundred users before it was pulled out.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
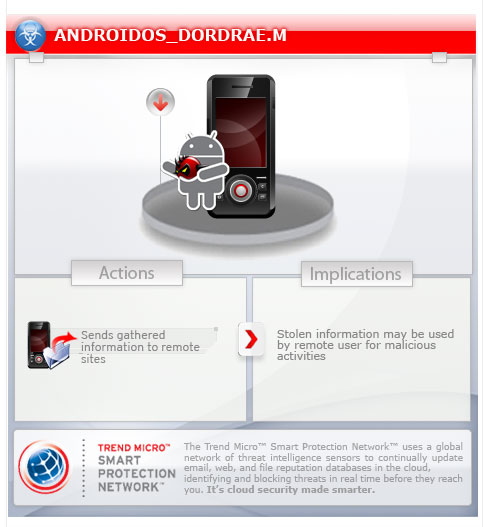
The malware service AppUseService runs every time the call state of the affected device changes. It then gathers the certain information. It sends the information to the remote servers.
Based on the analysis of its codes, this Trojan can also receive notification messages to display and download links from the said sites. It uses the notifications to trick users into downloading and installing the applications hosted in the links.
This Trojan may be manually installed by a user.
TECHNICAL DETAILS
Arrival Details
This Trojan may be manually installed by a user.
This malware arrives via the following means:
- Via Trojanized Android applications
NOTES:
The malware service AppUseService runs every time the call state of the affected device changes.
It then gathers the following information:
- Country
- Device model
- Device language setting
- IMEI
- IMSI
- Installed applications (application name, package name, package version)
It sends these information to the following remote servers:
- http://{BLOCKED}5a.com/lsda.jsp
- http://{BLOCKED}j5.com/pqwo.jsp
- http://{BLOCKED}8m.com/ijnh.jsp
Based on the analysis of its codes, this Trojan can also receive notification messages to display and download links from the said sites. It uses the notifications to trick users into downloading and installing the applications hosted in the links.
SOLUTION
Step 1
Trend Micro Mobile Security Solution
Trend Micro Mobile Security Personal Edition protects Android smartphones and tablets from malicious and Trojanized applications. The App Scanner is free and detects malicious and Trojanized apps as they are downloaded, while SmartSurfing blocks malicious websites using your device's Android browser.
Download and install the Trend Micro Mobile Security App via Google Play.
Step 2
Remove unwanted apps on your Android mobile device
Did this description help? Tell us how we did.


