Zero-day Exploit Hits All Versions of Internet Explorer
October 15, 2012
Microsoft has recently released MS12-063 to address vulnerabilities that affect all versions of Internet Explorer, namely versions 6, 7, 8, and 9. The following article is an in-depth look into the zero-day exploit and discusses its several repercussions.
What is MS12-063 all about?
MS12-063 is an out-of-band security bulletin that addresses attacks through vulnerabilities in all supported versions of Internet Explorer (9 and earlier). Microsoft gave MS12-063 a 'critical' rating.
These vulnerabilities in Internet Explorer (IE) were recently exploited in the wild. execCommand Use After Free Vulnerability or CVE-2012-4969 is the most severe of these vulnerabilities which leads to executing malicious code by remote attackers.This particular vulnerability was also exploited in a targeted attack that results in downloading the PlugX remote access Trojan (RAT).
What is the root cause of this exploit?
Prior to the out-of-band security update, unpatched IE browsers versions 6-9 were vulnerable to the exploit upon visiting compromised websites. This leads to attackers gaining the same privileges as the current user via the unpatched IE browsers. Additionally, stats have shown that this vulnerability puts more than 30% Internet users worldwide at risk.
Why is it called the "use after free" vulnerability?
"Use after free" refers to "referencing memory after it has been freed (which) can cause a program to crash, use unexpected values, or execute code."
How do attackers exploit this vulnerability?
Attackers make use of several components in order to successfully exploit IE. These include a malicious HTML file, a malicious .SWF file, and triggering a malicious .EXE as a final payload.
Will this exploit cause an impact IE 10?
No. The previously mentioned exploit is unrelated to the forthcoming IE 10 browser. But shortly after the zero-day exploit, Microsoft released a security update for users who have already downloaded the pre-released version of IE 10. Microsoft Security Advisory 2755801 addresses vulnerabilities in Adobe Flash Player in IE 10 on all supported editions of Windows 8 and Windows Server 2012.
Were there other attacks that exploited this vulnerability?
Yes. This exploit was also used in targeted attacks that dropped the PlugX remote access Trojan (RAT). These attacks were aimed toward government-related institutions and key industries.
What are other repercussions of unpatched systems?
Exploits generally allow attackers to drop or load malware that downloads other, more menacing malware onto vulnerable or unpatched systems. But even an up-to-date computer can be vulnerable to attacks through zero-day vulnerabilities. Zero-day exploits are more dangerous in nature as they target vulnerabilities that have yet to be resolved by the respective software vendors. Until the software vendor issues a workaround solution, i.e., a fix tool or the actual software update, users are left unprotected and vulnerable to threats.
How do I protect myself from this zero-day vulnerability?
Apart from applying the prescribed security updates, you can refer to reliable security blogs or software vendor advisory sites about new possible exploits and determine the infection vectors involved. If the exploit enters users’ computers through specific sites or targets certain browsers, it’s best to take a proactive approach. Switch to a different browser until you’re sure that all the fixes are in place. But using other Web browsers apart from IE may not be a viable option for some users due to limitations mandated by IT administrators in different institutions.
In any case, until the necessary patches are released, the browser exploit prevention built into Trend Micro™ Titanium™ 2013 also protects users against exploits targeting this vulnerability.
Are Trend Micro users protected from this threat?
Yes. The Trend Micro™ Smart Protection Network™ protects users by detecting the exploit and other malicious files and blocking access to the malicious servers. Refer to our vulnerability bulletin page for information on how Deep Security protects customers from these exploits. Additionally, users may refer to the official Microsoft Security Bulletins page for the patches and detailed information on the vulnerabilities.
What is MS12-063 all about?
MS12-063 is an out-of-band security bulletin that addresses attacks through vulnerabilities in all supported versions of Internet Explorer (9 and earlier). Microsoft gave MS12-063 a 'critical' rating.
These vulnerabilities in Internet Explorer (IE) were recently exploited in the wild. execCommand Use After Free Vulnerability or CVE-2012-4969 is the most severe of these vulnerabilities which leads to executing malicious code by remote attackers.This particular vulnerability was also exploited in a targeted attack that results in downloading the PlugX remote access Trojan (RAT).
What is the root cause of this exploit?
Prior to the out-of-band security update, unpatched IE browsers versions 6-9 were vulnerable to the exploit upon visiting compromised websites. This leads to attackers gaining the same privileges as the current user via the unpatched IE browsers. Additionally, stats have shown that this vulnerability puts more than 30% Internet users worldwide at risk.
Why is it called the "use after free" vulnerability?
"Use after free" refers to "referencing memory after it has been freed (which) can cause a program to crash, use unexpected values, or execute code."
How do attackers exploit this vulnerability?
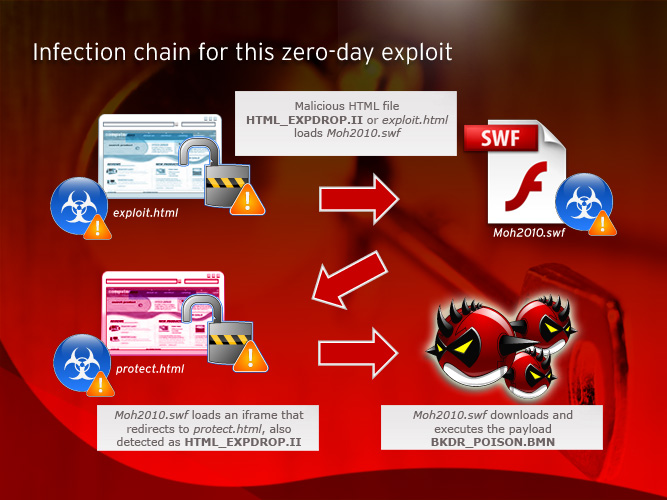
Attackers make use of several components in order to successfully exploit IE. These include a malicious HTML file, a malicious .SWF file, and triggering a malicious .EXE as a final payload.
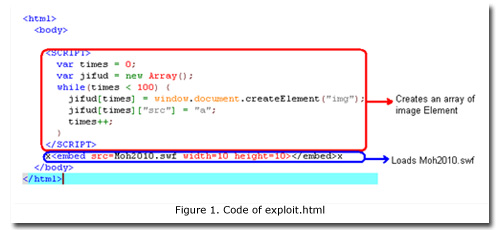
- When users connect to a compromised website, the malicious HTML file or exploit.html (HTML_EXPDROP.II) serves as the entry point of the attack. It creates multiple instances of the image element (array) in the document, or the current Web page. All of these set the value of src to string “a”. These values are stored in the heap memory. A heap refers to an area of pre-reserved memory that a program can use to store data in some variable amount.
HTML_EXPDROP.II then loads the malicious Moh2010.swf (SWF_DROPPR.II, SWF_DROPPR.IJ, SWF_DROPPR.IK or SWF_DROPPR.IL)
- Once Moh2010.swf loads, the .SWF then loads an iframe that redirects to protect.html, also detected as HTML_EXPDROP.II.
- Protect.html then triggers the vulnerability which follows the following sequence of events:
- Executing document.execCommand(“selectAll”) triggers the selectAll event "onselect=’TestArray()’”. It then creates the CmshtmlEd object in heap memory.
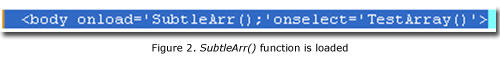
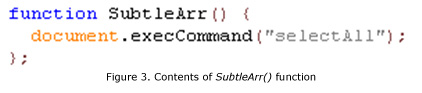
- When the TestArray() function triggers, it calls the document.write("L”" function to rewrite the .HTML document. It rewrites the .HTML document in order to "free" the heap memory of the created CmshtmlEd object. (This is the "free" part in the "use-after-free" vulnerability.)

- The method highlighted in Figure 5 below (parent.jifud[L].src = …) is executed 100 times to try to overwrite the freed heap memory of the CmshtmlEd object.
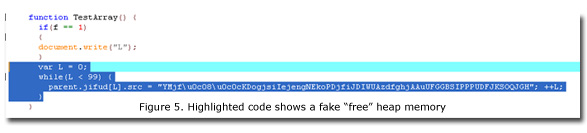
The CMshtmlEd::Exec method then tries to access the freed heap memory of the CmshtmlEd object. Calling the CMshtmlEd::Exec method leads to an exception error, which then leads to arbitrary code execution. (This is the "use" part in the "use-after-free" vulnerability.)
- Executing document.execCommand(“selectAll”) triggers the selectAll event "onselect=’TestArray()’”. It then creates the CmshtmlEd object in heap memory.
- Moh2010.swf contains the heap spray code (shellcode) which is already loaded in the memory. Once the use-after-free exception error occurs, it then executes the shellcode that is responsible for downloading and executing the payload http://{BLOCKED}.{BLOCKED}.104.149/public/help/111.exe or BKDR_POISON.BMN.
Will this exploit cause an impact IE 10?
No. The previously mentioned exploit is unrelated to the forthcoming IE 10 browser. But shortly after the zero-day exploit, Microsoft released a security update for users who have already downloaded the pre-released version of IE 10. Microsoft Security Advisory 2755801 addresses vulnerabilities in Adobe Flash Player in IE 10 on all supported editions of Windows 8 and Windows Server 2012.
Were there other attacks that exploited this vulnerability?
Yes. This exploit was also used in targeted attacks that dropped the PlugX remote access Trojan (RAT). These attacks were aimed toward government-related institutions and key industries.
What are other repercussions of unpatched systems?
Exploits generally allow attackers to drop or load malware that downloads other, more menacing malware onto vulnerable or unpatched systems. But even an up-to-date computer can be vulnerable to attacks through zero-day vulnerabilities. Zero-day exploits are more dangerous in nature as they target vulnerabilities that have yet to be resolved by the respective software vendors. Until the software vendor issues a workaround solution, i.e., a fix tool or the actual software update, users are left unprotected and vulnerable to threats.
How do I protect myself from this zero-day vulnerability?
Apart from applying the prescribed security updates, you can refer to reliable security blogs or software vendor advisory sites about new possible exploits and determine the infection vectors involved. If the exploit enters users’ computers through specific sites or targets certain browsers, it’s best to take a proactive approach. Switch to a different browser until you’re sure that all the fixes are in place. But using other Web browsers apart from IE may not be a viable option for some users due to limitations mandated by IT administrators in different institutions.
In any case, until the necessary patches are released, the browser exploit prevention built into Trend Micro™ Titanium™ 2013 also protects users against exploits targeting this vulnerability.
Are Trend Micro users protected from this threat?
Yes. The Trend Micro™ Smart Protection Network™ protects users by detecting the exploit and other malicious files and blocking access to the malicious servers. Refer to our vulnerability bulletin page for information on how Deep Security protects customers from these exploits. Additionally, users may refer to the official Microsoft Security Bulletins page for the patches and detailed information on the vulnerabilities.