PREDATOR


Threat Type: Others
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
The Predator malware first appeared in July 2018 and is used to steal usernames, passwords, browser data and the contents of cryptocurrency wallets, as well as take photos using the infected victim's webcam. The malware is commonly sold on underground hacking forums and was also featured as part of a bundle of six different forums of malicious software.
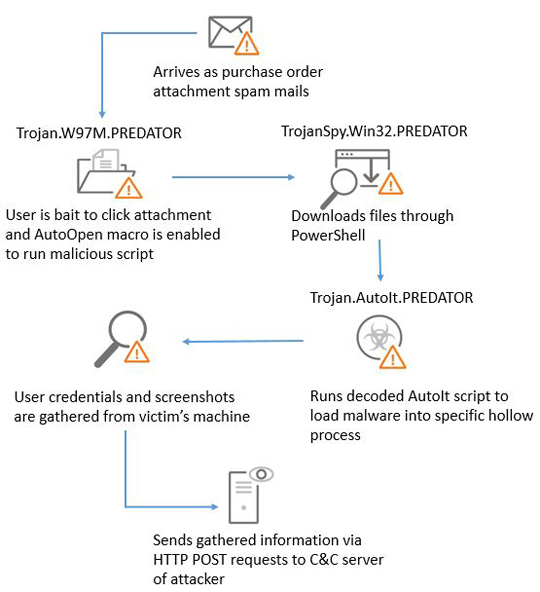
This malware is now delivered through spam with malicious attachments using fake purchase order documents as lure. It has tricks to avoid detection and analysis by using shellcode to effectively detect debuggers and sandboxes. It uses legitimate AutoIt software to execute payload of the malware. The AutoIt is a scripting language intended to automate basic tasks in Windows graphical user interface (GUI). The gathered information is packed and sent to the command and control (C&C) server of the malware attackers. The data package is sent via Hypertext Transfer Protocol (HTTP) POST requests, alongside fingerprint data and sensitive network configurations.
This malware gathers the following data and sends it to its servers:
- User credentials and other sensitive data such as computer software and specifications
- Credit card user credentials
- Information from various local and cloud folders
- Cryptocurrency files from Ethereum, Multibit, Electrum, Armory, Bytecoin and Bitcoin files
- Cookies from web browsers such as Chrome, Firefox
- File Transfer Protocol (FTP) credentials from FTP software such as FileZilla, WinFTP
- Gaming accounts from Steam, Discord
- Screenshots of desktop and photos of user from webcam
It is capable of the following:
- Information theft
Predator typically follows the infection chain below: