HKTL_COINMINE.GH
Application.BitCoinMiner.SX (BITFENDER)
Windows


Threat Type: Hacking Tool
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
Downloaded from the Internet
This Hacking Tool may be hosted on a website and run when a user accesses the said website.
TECHNICAL DETAILS
137,881 bytes
JS
No
21 Sep 2017
Connects to URLs/IPs
Arrival Details
This Hacking Tool may be hosted on a website and run when a user accesses the said website.
NOTES:
This JavaScript is embedded into websites to run a coinminer for Monero cryptocurrency miner.
It checks either of the following before it runs its coinminer:
- WebAssembly
- asm.js
The script accepts following relevant parameters:
- Target number of mining threads per tab
- Throttle rate
- execution / start - mode
- Target number of hashes to solve
It can have the following start modes:
- IF_EXCLUSIVE_TAB
The miner will only start if no other tabs are already mining. - FORCE_EXCLUSIVE_TAB
The miner will always start and immediately kill all miners in other tabs that have not specified CoinHive.FORCE_MULTI_TAB. - FORCE_MULTI_TAB
The miner will always start.
It has the capability to monitor the following events:
- open
- authed
- close
- error
- job
- found
- accepted
It sends events and other data to the following URLs:
- wss://ws001.{BLOCKED}ive.com/proxy
- wss://ws002.{BLOCKED}ive.com/proxy
- wss://ws003.{BLOCKED}ive.com/proxy
- wss://ws004.{BLOCKED}ive.com/proxy
- wss://ws005.{BLOCKED}ive.com/proxy
- wss://ws006.{BLOCKED}ive.com/proxy
- wss://ws007.{BLOCKED}ive.com/proxy
- wss://ws008.{BLOCKED}ive.com/proxy
- wss://ws009.{BLOCKED}ive.com/proxy
- wss://ws009.{BLOCKED}ive.com/proxy
- wss://ws010.{BLOCKED}ive.com/proxy
- wss://ws011.{BLOCKED}ive.com/proxy
- wss://ws012.{BLOCKED}ive.com/proxy
- wss://ws013.{BLOCKED}ive.com/proxy
- wss://ws014.{BLOCKED}ive.com/proxy
- wss://ws015.{BLOCKED}ive.com/proxy
- wss://ws016.{BLOCKED}ive.com/proxy
- wss://ws017.{BLOCKED}ive.com/proxy
- wss://ws018.{BLOCKED}ive.com/proxy
- wss://ws019.{BLOCKED}ive.com/proxy
- wss://ws020.{BLOCKED}ive.com/proxy
- wss://ws021.{BLOCKED}ive.com/proxy
- wss://ws022.{BLOCKED}ive.com/proxy
- wss://ws023.{BLOCKED}ive.com/proxy
- wss://ws024.{BLOCKED}ive.com/proxy
- wss://ws025.{BLOCKED}ive.com/proxy
- wss://ws026.{BLOCKED}ive.com/proxy
It implements a system where users has to solve certain number of hashes before proceeding to next website content, which act as an alternative on running ads:
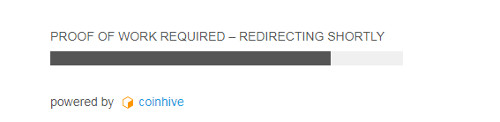
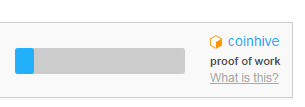
SOLUTION
9.850
Close all opened browser windows
NOTES:
Scan your computer with your Trend Micro product to delete files detected as MALWARE_NAME. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.

