Update as of 03/22/3023 2:50PM PHT: Updated the prevention and mitigation section for an additional step.
CVE-2023-23397 is a critical privilege elevation/authentication bypass vulnerability in Outlook, released as part of the March Patch Tuesday set of fixes. The vulnerability, which affects all versions of Windows Outlook, was given a 9.8 CVSS rating and is one of two zero-day exploits disclosed on March 14. We summarise the points that security teams need to know about this vulnerability and how they can mitigate the risks of this gap.
What is it?
CVE-2023-23397 is an elevation of privilege (EoP) vulnerability in Microsoft Outlook. It is a zero-touch exploit, meaning the security gap requires low complexity to abuse and requires no user interaction.
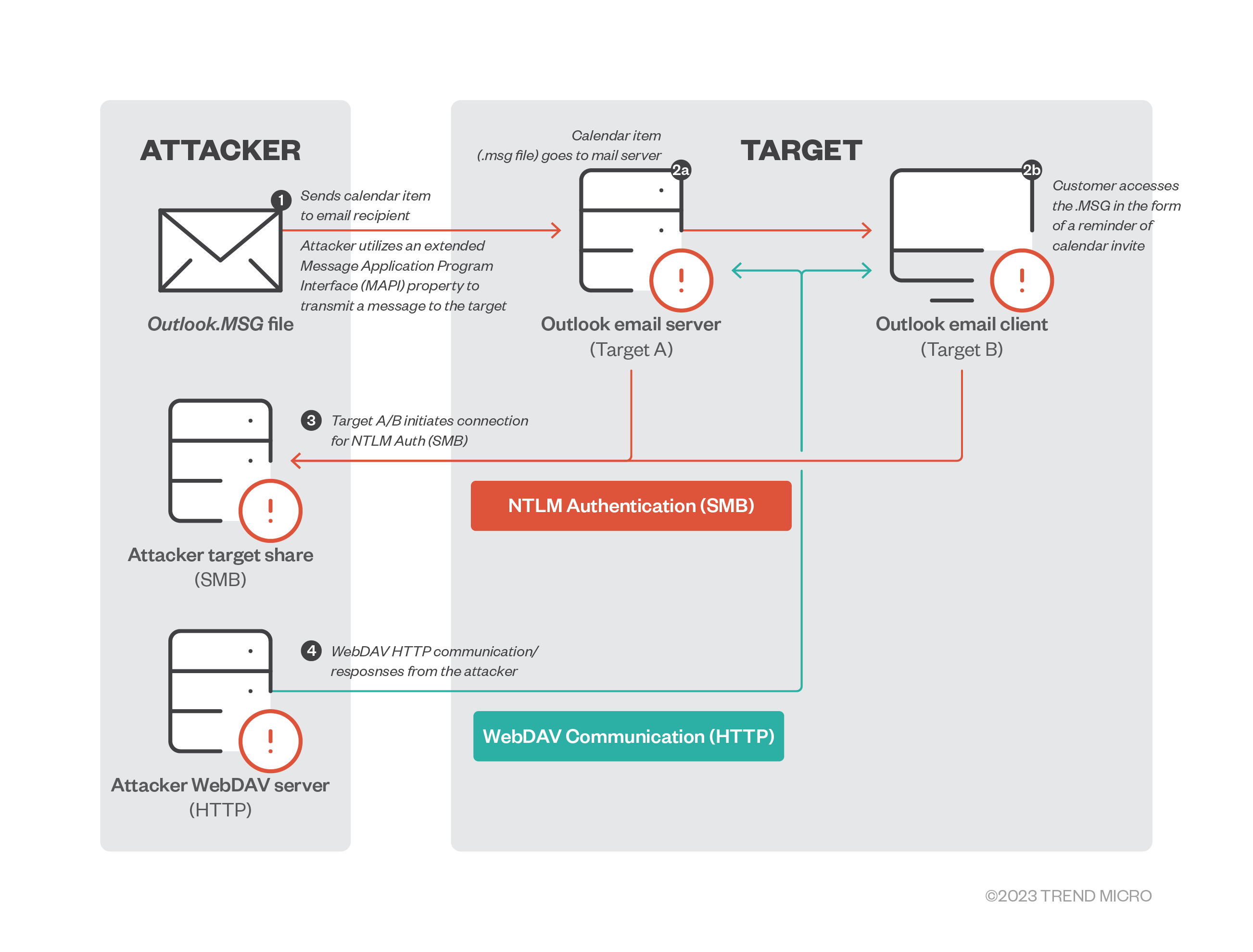
How is CVE-2023-23397 exploited?
The attacker sends a message to the victim with an extended Message Application Programme Interface (MAPI) property with a Universal Naming Convention (UNC) path to a remote attacker-controlled Server Message Block (SMB, via TCP 445). Share-hosted on a server controlled by the attacker, the vulnerability is exploited whether the recipient has seen the message or not. The attacker remotely sends a malicious calendar invite represented by.msg — the message format that supports reminders in Outlook — to trigger the vulnerable API endpoint PlayReminderSound using “PidLidReminderFileParameter” (the custom alert sound option for reminders).
When the victim connects to the attacker’s SMB server, the connection to the remote server sends the user’s New Technology LAN Manager (NTLM) negotiation message automatically, which the attacker can use for authentication against other systems that support NTLM authentication.
NTLMv2 hashes are the latest protocol Windows uses for authentication, and it is used for a number of services with each response containing a hashed representation of users’ information, such as the username and password. As such, threat actors can attempt a NTLM relay attack to gain access to other services, or a full compromise of domains if the compromised users are admins. While online services such as Microsoft 365 are not susceptible to this attack because they do not support NTLM authentication, the Microsoft 365 Windows Outlook app is still vulnerable.
How easy is it to exploit?
User interaction is not necessary to trigger (even before message preview) it, nor does it require high privileges. CVE-2023-23397 is a zero-touch vulnerability that is triggered when the victim client is prompted and notified (e.g., when an appointment or task prompts five minutes before the designated time). It is difficult to block outbound SMB traffic for remote users. The attacker could use the same credentials to gain access to other resources. We elaborate on this example in our webinar (at 04:23 of the video).
Is it in the wild? What versions and operating systems (OS) are affected?
There have been reports of limited attacks abusing this gap. Microsoft has been coordinating with the affected victims to remediate this concern. All supported versions of Microsoft Outlook for Windows are affected. Other versions of Microsoft Outlook, such as Android, iOS, Mac, as well as Outlook on the web and other M365 services, are not affected.
What are the possible attack scenarios?

1. Lateral movement, malicious navigation using the relayed NTLM hashes
Relay attacks gained notoriety as a use case for Mimikatz using the NTLM credential dumping routine via the sekurlsa module. In addition, pass-the-hat (PtH) (or pass-the hash) attacks and variations of data and information theft can be done. Once attackers are in the system, they can use the network for lateral movement and navigate the organisation’s lines over SMB.

2. WebDAV directory traversal for payload attacker routines
It’s possible for an attacker to leverage WebDAV services in cases where no valid SMB service for Outlook exists (i.e., is not configured) in the client. This is an alternative to the Web/HTTP service that can also be read as a UNC path by.msg and/or Outlook Calendar items. Attackers can set up a malicious WebDAV server to respond to affected victim clients with malicious pages. These pages may contain code that can range from leveraging a directory traversal technique similar to the Microsoft vulnerability CVE-2022-34713 (dubbed as DogWalk) to push any form of payload for remote code execution such as webshells.
What can I do to prevent and mitigate the risk of exploitation of CVE-2023-23397?
Here are some steps that security administrators can perform to reduce the risk of exploitation of CVE-2023-23397:
- Apply the vendor patches immediately. Microsoft has released a patch as part of their March 2023 Monthly Security Update.
- Block TCP 445/SMB outbound from your network. This will prevent the sending of NTLM authentication messages to remote file shares. If this cannot be done, we recommend monitoring outbound traffic over port 445 for unknown external IP addresses, then identifying and blocking them.
- Customers can disable the WebClient service. Note that this will block all WebDAV connections, including intranet.
- Add users to the Protected Users Security Group. This prevents the use of NTLM as an authentication mechanism, but note that this could impact applications that rely on NTLM in your environment.
- Enforce SMB signing on clients and servers to prevent a relay attack.
- Other researchers have noted that disabling the "Show reminders" setting in Outlook can prevent the leak of NTLM credentials.
How can I check if I’m affected?
Microsoft has provided a PowerShell script as a solution to the issue. The script is designed to scan emails, calendar entries, and task items, and to verify if they have the “PidLidReminderFileParameter” property. By running the script, administrators can locate problematic items that have this property and subsequently remove them or delete them permanently. Download the script here: https://github.com/microsoft/CSS-Exchange/blob/a4c096e8b6e6eddeba2f42910f165681ed64adf7/docs/Security/CVE-2023-23397.md.
Which Trend Micro solutions can address this vulnerability?
- Trend Micro Malware Detection Patterns (VSAPI, Predictive Learning, Behavioural Monitoring and Web Reputation Service) for Endpoint, Servers, Mail, and Gateway (e.g., Apex One, Worry-Free Business Security Services, Worry-Free Business Security Standard/Advanced, Deep Security with anti-malware, etc.):
- Starting with Trend Micro Smart Scan Pattern version 21474.296.07, known exploits associated with this vulnerability are being detected as Trojan.Win32.CVE202323397.
- Trend Micro Vision One: Use this solution as an investigation tool. In the “Search App,” select “Endpoint Activity Data” and enter the following query: - dpt: 445 AND eventSubId: 204 AND processcmd: *OUTLOOK*. This can be saved and added to a watchlist if desired.
- Cloud One Workload Security and Deep Security: IPS Rule 1009058, which will need to be changed to Prevent.
- TippingPoint Filters:
- 28471 SMB: SMBv1 Successful Protocol Negotiation
- 28472 SMB: SMBv2 Successful Protocol Negotiation
- Please note: Enabling these filters in Block mode will interrupt legitimate SMB traffic. Customers are advised to add exceptions for their Private IP address space.
- Trend Micro Deep Discovery Inspector: Rule 4479 NTLM v1 Authentication - SMB (Request).
- If NTLM v1 is configured by default, customers can use this rule to monitor attempts for outgoing NTLM handshakes. Please note this rule only detects and does not block, so it is best used as an investigative tool for follow-up.
Details for all available Trend Micro solutions are available here: https://success.trendmicro.com/dcx/s/solution/000292525?language=en_US.
To learn more about this vulnerability, you may view our technical webinar here: https://www.youtube.com/watch?v=j44vIhklTp4

