
Check out the Essential Cybersecurity Compliance series:
- Essential Cybersecurity Compliance Standards
- Use PCI DSS Checklist with Automation
- How to Reach Compliance with HIPAA
- Deliver ISO Compliance with Automation
Cloud computing has become the de-facto method for developing applications thanks to its convenient, self-service, on-demand computing capabilities, often at a fraction of the cost of on-premises solutions. Companies using the cloud also experience more agility, allowing them to provide indispensable resources. This includes the ability to expand and contract services based on utilisation and demand and access those services from anywhere in the world. Enterprises using cloud-native programmes like Microsoft 365, Dropbox™, and Google Workspace™ can sustain their business while employees work remotely. However, using a cloud computing model has its challenges. Security, interoperability, and legal and regulatory compliance are amongst the chief hurdles to overcome.
With much at stake, companies are thinking about how to meet their compliance requirements with standards and laws like GDPR, HIPAA, and ISO. In this article we will review why meeting compliance obligations are important to you and how to use the National Institute of Standards and Technology (NIST) to meet compliance obligations.
What is NIST?
To put it simply, NIST uses its Cybersecurity Framework (CSF) to help business better understand and manage their cybersecurity risks.
The NIST CSF is made up of five central elements:
- Identify: A common understanding to manage cybersecurity risks for systems, people, data, amongst others.
- Protect: A security plan to ensure the organisation runs smoothly.
- Detect: Timely discovery of cybersecurity events.
- Respond: Quick remediation to minimise impact to the business and its customers.
- Recover: Like reviewing the game film—you need to adapt your strategy to protect against new and evolving threats.
In addition, the NIST CSF is made up of three essential components:
- Framework core: Standards, guidelines, and practises that help produce desired outcomes by improving communication of cybersecurity activities and results across the entire organisation.
- Implementation tiers: Context on how organisations view risks and what processes are in place to manage said risks. The tiers also “rank” the business’ risk management throughout time.
- Framework profiles: The framework, like cybersecurity, is not one-size-fits-all. The profile reflects the specific needs of the business and helps identify opportunities for improvement.
NIST and the cloud
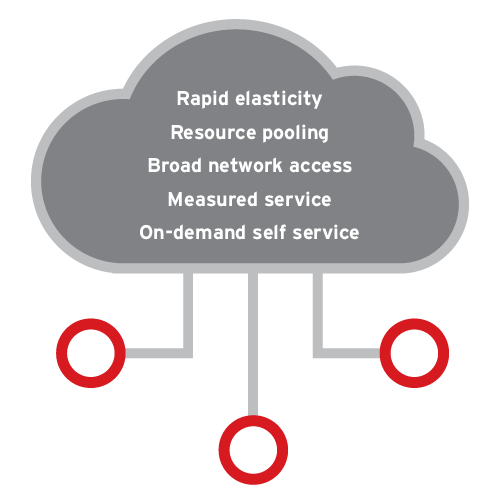
While the NIST CSF evaluates the organisation’s general cybersecurity posture, the NIST Cloud Computing Programme (NCCP) is a model that promotes cloud adoption through cost-effectiveness, availability, high-performance, and convenience. The cloud computing model is composed of five essential characteristics:
Along with three service models:
- Software as a service (SaaS)
- Platform as a service (PaaS)
- Infrastructure as a service (IaaS)
And four deployment models:
- Private
- Community
- Public
- Hybrid
Who has to comply?
While, for those in private sector, NIST compliance isn’t mandatory, all federal government agencies and their federal contractors (and subcontractors) working with government data are required to comply. The root this can be drawn to the Federal Information Security Modernization Act of 2014 (FISMA). Since then, US government agencies and their contractors have been required to implement “effective information security programmes” that include risk management, security governance, security evaluation and testing, and incident response capabilities.
While, according to (ISC) ², the global cyber workforce gap increased by 26.2% in 2022, it’s no secret that there is a significant knowledge gap between organisations when it comes to securing high-value assets. This is often because security laws and regulations have been implemented, but many fail to tell you how to be secure. NIST aims to eliminate these gaps by providing detailed guidance, no matter the industry or organisation size. That’s why many companies have voluntarily started leveraging NIST guidelines and standards to implement, manage, operate, monitor, and improve their security programmes for a stronger defence posture.
NIST in action
Since NIST is more of a guidebook than an actual law, one cannot accurately say a breach occurred because the organisation didn’t follow NIST. But, if you look at the cause of breaches, you’ll recognise how leveraging NIST could’ve led to a better outcome. Intel recently implemented the NIST framework voluntarily, reporting that "the Framework can provide value to even the largest organisations and has the potential to transform cybersecurity on a global scale by accelerating cybersecurity best practises".
However, all organisations don’t have the same level of insight. Here are some recent breaches that could’ve used a little help from NIST:
Meta
The 2021 Facebook data breach resulted in mobile numbers and email addresses of 533 million users being exposed and posted on a popular hacker forum. Facebook responded that it was not a cause for concern because the breach occurred in 2019, which is actually more concerning.
The fact this breach happened two years ago brings elements #4 and #5 of NCF into the conversation. Facebook claims they “found and fixed” the issue in August 2019, but since then they’ve experience similar email/phone number breaches in September and December 2019 and early 2020. Also, Facebook did a poor job on the recovery front—as the scraped data went on to be exposed nearly two years later.
Estee Lauder
The cosmetic giant exposed more than 440 million data pieces due to an unsecured database, as there was no password protection in place. Estee Lauder could have avoided this breach by following NCF element #1 and identifying which systems need to be protected, while working toward a more secure and protected infrastructure.
U.S. Cellular
In January 2021, threat actors targeted retail employees of the fourth-largest wireless carrier in the US. Through an undisclosed method, cybercriminals were able to trick employees into downloading malicious software. This allowed them to gain remote access to the company’s customer relationship management (CRM) software and company devices containing records for nearly 5 million customers. Luckily, U.S. Cellular detected it just two days after the attack. While many believe that breaches only take place on servers, it nonetheless shows that the human attack vector needs to be secured as well. This demonstrates the importance of NCF element #1—security isn’t just about configurations, it’s also educating employees on the signs of a potential scam.
Why does this matter to you?
It’s your responsibility to safeguard your organisation’s assets against security breaches. Employing a zero-trust approach paired with regular backups and cultivating an organisation-wide cybersecurity culture to security are the first steps towards employing NIST compliancy.
Many U.S. organisations have been taking a federal-first approach to compliance. As the federal government is a prime target for today’s most advanced cyberattacks, implementing government standards will ensure that any lesser requirements will also be covered.
Thanks to automation, leveraging NIST and meeting compliance regulations doesn’t have to be as time-consuming or complicated as anticipated. Automating security scans for misconfigurations saves cybersecurity teams time from manually scanning and reduces the chances of breaches caused by human error (the #1 cause of cloud misconfigurations).
Automate and accelerate your audits with Trend Micro Cloud One™ – Conformity
Automating security audits allows your IT teams to work at lightning speed while meeting business’ compliance needs. Conformity provides your team with:
- Real-time configuration scans against hundreds of industry best practise cheques for Amazon Web Services (AWS) and Microsoft Azure™ environments.
- Standardised and custom reports to audit your environment, including all the ones your business cares about, including NIST, SOC2, ISO 27001, CIS, GDPR, PCI DSS, and HIPAA.
- A library of over 800 cloud service configuration remediation guides so that no matter your team’s cloud or security skill level, your misconfigurations can get fixed.
- Seamless integration into your CI/CD pipeline due to powerful APIs.
- Infrastructure as code (IaC) to ensure only the most secure and compliant templates are deployed.
- Connection to preferred third-party providers, including Slack, Jira, Zendesk, PagerDuty, and Microsoft Teams.
What’s next?
See how automated cloud security posture management can help you secure your cloud infrastructure with clarity and simplicity.

