Cybercriminals have more tools than ever to disrupt business operations, steal data for ransom, and manipulate employees into exposing sensitive information. Generative AI (GenAI) is taking those capabilities to new levels by enhancing phishing attacks and enabling audio and video deepfakes.
Security professionals are also facing new pressures from chief executives and corporate boards who increasingly understand the legal, financial, and reputational risks cyber threats pose to businesses.
To find out how these and other developments are shaping the day-to-day experience of cybersecurity professionals worldwide, Trend conducted its inaugural Risk to Resilience World Tour Survey. We surveyed more than 750 cybersecurity professionals in 49 countries, with a focus on four key roles:
- Chief information security officer (CISO) – Read more here.
- Security operations center (SOC) team – Read more here
- IT operations staff
- Cloud security engineers
This blog explores our findings from IT operations staff respondents. Check out the full report, The Defenders, to read about the other roles.
IT operations: hands-on defense
IT operations teams bridge the gap between operational continuity and resilient security postures by ensuring security protocols are applied. Those protocols include deploying security agents onto devices, correcting misconfigurations, and patching vulnerabilities. To be effective and timely, IT operations teams need seamless, continuous communication with their SOC peers.
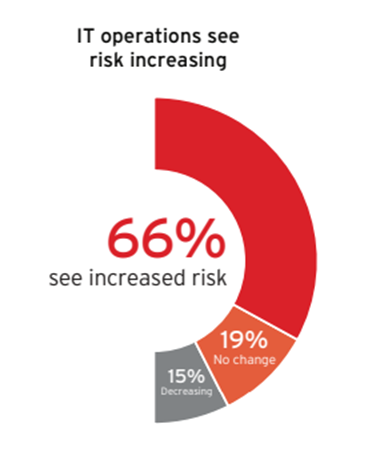
Risk on the rise
The majority (66%) of IT operations survey respondents say their organization’s risk level is increasing. Their ability to answer with confidence marks a shift even from five years ago, when teams had far less visibility into risk trends.
This sense of mounting risk may also be due to what IT operations teams cite as their topmost operational challenges: blind spots in the attack surface (17%) and the ability to prioritize remediations (13%). What goes unseen can’t be mitigated, and ineffective prioritization may cause critical vulnerabilities to linger. Identifying risks up front to proactively reduce breach potential helps to prevent this.
One particular risk on the minds of IT operations teams today is AI, primarily because they are involved directly in rolling out tools that use AI technology. Despite these continued and welcome innovations, corporate policies and user awareness of AI risks aren’t often current with the fast-changing AI reality.
Security posture is an all-in endeavor
Although CISOs are responsible for overall cybersecurity efficacy and SOC teams help take critical protective—and proactive—actions, every part of the business has a role to play in establishing and maintaining a strong security posture.
To ensure they’re working in complementary ways, IT operations require processes and regular cadence communication with the SOC. Platform-centric approaches support IT operations by integrating tools and telemetry while providing a foundation from streamlined communication, prioritization, and ticketing with other groups, including SOC and cloud teams.
The paths to managing cyber risk are converging
CISOs and security teams battle with resource constraints. IT operations seek greater integration. Cloud security engineers strive for expanded visibility. All of these needs can be addressed with the AI-powered automation, contextualized data, and integration of a platform-based approach to cybersecurity.
Consolidating security within a single platform that can integrate third-party toolsets gives security leaders what they need with more flexibility, greater efficiency, minimized sprawl, and reduced total cost of ownership.
This approach meets security teams where they’re at and respects the investments organizations have made to date, while transforming working models to drive strong user experience and security outcomes. Rich telemetry is more readily available, empowering teams to make more proactive and effective risk remediation decisions.
Trend Vision One™ delivers the benefits of a platform approach with comprehensive protection, prevention, detection, and response capabilities—all powered by AI and leading threat research and intelligence. It supports diverse hybrid IT environments, automates and orchestrates workflows, and delivers expert cybersecurity services to simplify and converge security operations holistically—all while measuring and communicating overall risk management and performance to stakeholders.
Explore more resources:
- Read the full report
- Intercepting Impact: 2024 Trend Micro Cyber Risk Report
- Explore our Trend Vision One platform

