Evolving phishing threats, such as QR code attacks, pose significant risks to organizations across various industries, including retail, healthcare, construction, and engineering. Such modern attacks urge businesses targeted by cybercriminals to adopt robust protection to safeguard sensitive information against data breaches, exfiltration, un-authorization, or illegal access. These vulnerabilities could further be leveraged for additional attacks.
QR code attacks on the rise
Phishing emails continues to be the number one attack vector for organizations. A QR code phishing, or quishing attack, is a modern social engineering cyberattack technique manipulating users into giving away personal and financial information or downloading malware. It targets C-level executives and the highest strategic roles within a company.
Quishing can bypass traditional security email gateways, evading email filtering tools and identity authentication. This allows cyberattacks to move from a protected email to the user’s less secure mobile device, where cybercriminals can obtain confidential information, such as payment details, for fraudulent purposes. For instance, a malicious QR code hidden in PDF or an image (JPEG/PNG) file attached to an email can bypass email security protection, such as filtering and flagging. This allows the email to be delivered directly to the user’s inbox without being analyzed for clickable content.
According to Egress Report 2024, “phishing remains the top attack vector with 94% of organizations falling victim through modern attack techniques that have expanded beyond email to collaboration tools and Cybersecurity leaders admitted that they are stressed about email security.” Such attacks include compromised supply chain email accounts and account takeovers (ATO). Research also highlighted the impact of generative AI (GenAI) enabling attackers to develop targeted phishing emails and produce malware. With GenAI, sophisticated threats like QR code phishing, credential phishing, AI-based email threats, or business email compromise (BEC) attacks continue to evolve. This increases the risk of attack surface expansion in email and collaboration environments.
How can organizations mitigate the risk of QR code attacks?
Businesses are challenged to identify the risk and improve their security posture to avoid the costs and implications of data leakage, reputational consequences, IT downtime, and technological disruption.
To recognizing quishing, IT admin and SOC teams need real-time protection capabilities to prevent QR code malicious attacks.
Common signs include:
- Unusual sources. Be cautious of QR codes from unexpected or unverified sources, such as random flyers, unsolicited emails, or unknown websites.
- Too good to be true. Verify QR codes promising rewards, discounts, or prizes—they could be traps. Scammers often use enticing offers to lure victims.
- Complex URLs. Inspect the URL embedded in the QR code. If it is excessively long, convoluted, or contains random characters, it could lead to a phishing site.
- Misspellings or odd characters. Check for misspelled words or unusual characters within the QR code. Legitimate companies usually pay attention to details.
Employees require training to enhance their attentiveness in detecting quishing when receiving QR code-based emails or accessing embedded links.
Common signs include:
- No context. Exercise caution if the QR code lacks context or appears out of place, such as QR codes randomly placed in a public area.
- Web links. Avoid sites accessed through a QR codes that request payments. Instead, enter a known and trusted URL for transactions.
- Overlays. Be wary if the QR code is placed over existing signs or labels, as scammers may try to cover up legitimate information.
- Too much information: Be skeptical of QR codes that ask for excessive permissions (e.g., access to your camera, contacts, or location) beyond what is necessary.
The growing use of QR codes as a phishing vector underscores the importance of vigilance and security awareness when scanning them.
A proactive approach to QR code-based phishing attacks (quishing)
Trend Vision One™ – Email and Collaboration Security enables you to swiftly detect and respond to user-targeted threats. It disrupts the QR code phishing attack chain, and allows you to streamline detections, risk posture, and mitigation across your messaging environment.
Provide your team with enhanced security against malicious QR codes with AI-powered advanced analytics and pre-delivery scanning designed to intercept and neutralize phishing attacks before they reach your inbox.
Benefit from real-time extraction of QR code links from emails, followed by comprehensive scanning and remediation actions on various file and image formats (JPEG, PNG, BMP, TIFF, GIF, .webP) to ensure security.
When an email body and/or email attachment containing a QR code is detected, your IT admin can make contextualized decisions and take remedial actions conveniently from a centralized platform.
These actions include:
- Tag subject
- Add disclaimer
- Pass
- Quarantine
- Delete
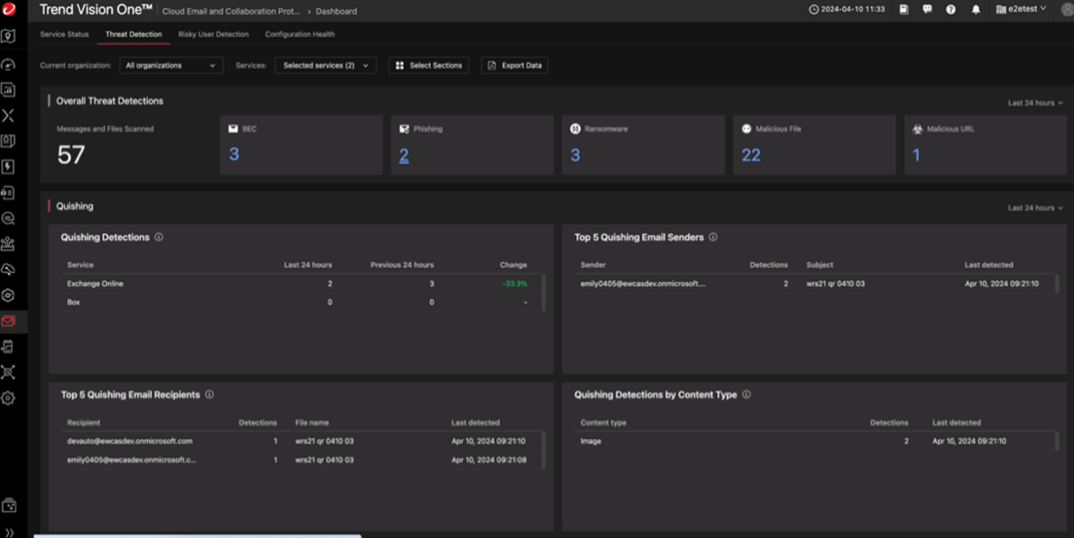
Gaining visibility to the attack surface boosts contextualized decision making
Building awareness, granting visibility, and improving readiness require embracing an agile approach with multi-layered security layers to detect, prevent and respond to the rapidly changing attack landscape.
Through centralized management and advanced analytics, you can remove silos and visibility gaps to effectively streamline your security operations.
Practices include:
- SOC teams can investigate the spread of an attack threat, eliminate blind spots, identify users at-risk, and explore related threats by using platform capabilities like XDR for advanced analytics and ASRM (attack surface risk management) for deep insights
- IT admins can implement response plans. They can leverage this information to lower the risk scores of users (i.e., employees at risk), make informed decisions to tag or quarantine phishing emails, or force them to reset their passwords and notify relevant security teams. Regular security audits can help ensure that your response plan is effective
- IT admins can educate users on the risks associated with QR codes. They can initiate personalized Security Awareness Training campaigns targeted at all employees or high-risk user groups. You can now monitor training attendance and completion as your training campaign progresses
By adopting these practices, you can improve the organization’s security posture, reduce the risk of falling victim to QR code phishing attacks, and improve your security awareness performance—all from a single platform.
Quishing Detection Demo in Trend Vision One™ platform:
In this demo, IT Admins and SOC team can automatically detect and respond to QR code phishing attacks with centralized visibility and management by leveraging a unified cybersecurity platform. The Cloud Email and Collaboration Protection dashboard lists the current threats including: 1 BEC, 7 phishing attacks, 1 quishing detection (1 sender and 1 recipient) with content type (1 image).
To test this capability, the video illustrates how a user could fall victim to a quishing attack via email phishing. The first attempt shows a malicious QR code found in an image (png.) to the body of an email, sent via MS Outlook email. The second attempt shows a malicious QR code embedded into a PDF file, sent via MS Outlook email as an attachment.
By adding these 2 attempts, IT Admin/SOC can inspect the details of the new phishing attacks in the Vision One Cloud Email and Collaboration Protection logs (time, source, threat type, security filter, risk, detection type, QR code file name, email info, etc.) and take remediation action to quarantine the emails.
Navigating to the dashboard, it is now refreshed to preview 2 new QR-code phishing detections with their related content types to have a total of: 1 BEC, 9 phishing, 3 quishing detections (3 senders and 3 recipients) with content type (2 images and 1 PDF). Moreover, IT Admin/SOC can investigate the source file type of the PFD and Images and check the email detection details for further analysis.
Our platform capability allows your team to automate remediation and response using advanced analysis, quarantine or delete malicious emails and/or isolate users, and proactively secure users and sensitive data.To learn more about how we protect your organization’s IT environment, download our data sheet: Trend Vision One™ - Email and Collaboration Security.

