What is Identity Threat Detection and Response (ITDR)?
Identity Threat Detection and Response (ITDR) is a cybersecurity approach focused on identifying and mitigating identity-related threats, safeguarding digital entities and identities from unauthorized access, and providing reliable proactive threat detection.
ITDR vs. XDR vs. EDR
Identity threat detection and response (ITDR)
Identity Threat Detection and Response, or ITDR, focuses on identity-related threats, targeting areas like credential theft, misused privilege, and other identity-based issues. It offers an additional layer of security by integrating with Identity and Access Management (IAM) systems.
Extended detection and response (XDR)
Extended Detection and Response, or XDR, offers threat detection and response capabilities across an organization’s entire infrastructure—including endpoints, servers, cloud workloads, and networks. While XDR aims to unify and correlate data across different environments for better threat detection, ITDR narrows down its focus to identity threats specifically.
Endpoint detection and response (EDR)
Endpoint Detection and Response, or EDR, works to detecting and responding to threats targeting endpoint devices, such as laptops, desktops, or servers. Unlike ITDR, which deals with identities, EDR focuses exclusively on endpoint devices and does not provide comprehensive insights into identity-based threats.
Key differences and use cases
Aspect |
ITDR |
XDR |
EDR |
Focus |
Identity and access threats |
IT infrastructure |
Endpoint devices |
Technology |
Identity analytics and IAM integration |
Multi-layered correlation |
Endpoint monitoring and analytics |
Key Features |
User analytics and MFA |
Centralized threat detection |
Endpoint threat detection |
Use Case |
Prevention of identity theft and similar threats |
Comprehensive threat visibility |
Endpoint ransomware detection |
How ITDR works
ITDR systems work by monitoring identity activities and identifying anything that could reveal bad actors. They collect identity-related logs and use special algorithms to detect strange behaviors as well.
Machine learning and artificial intelligence are important components of ITDR as well. They can help facilitate threat detection through adaptive learning. Algorithms can sort through massive datasets to find patterns and create alerts for any suspicious activity in real time.
The ITDR process itself starts with monitoring identity-related anomalies and pursuing them in real time. When a suspicious activity is flagged, ITDR tools can automatically generate alerts to also send through a response. That alerts the security team to what's happening and kicks off a series of automated actions.
ITDR integrates with existing security frameworks like IAM, EDR, and XDR to create a layered security approach. That lets ITDR create context-rich alerts and extend its capabilities across the IT ecosystem for a more effective threat detection system.
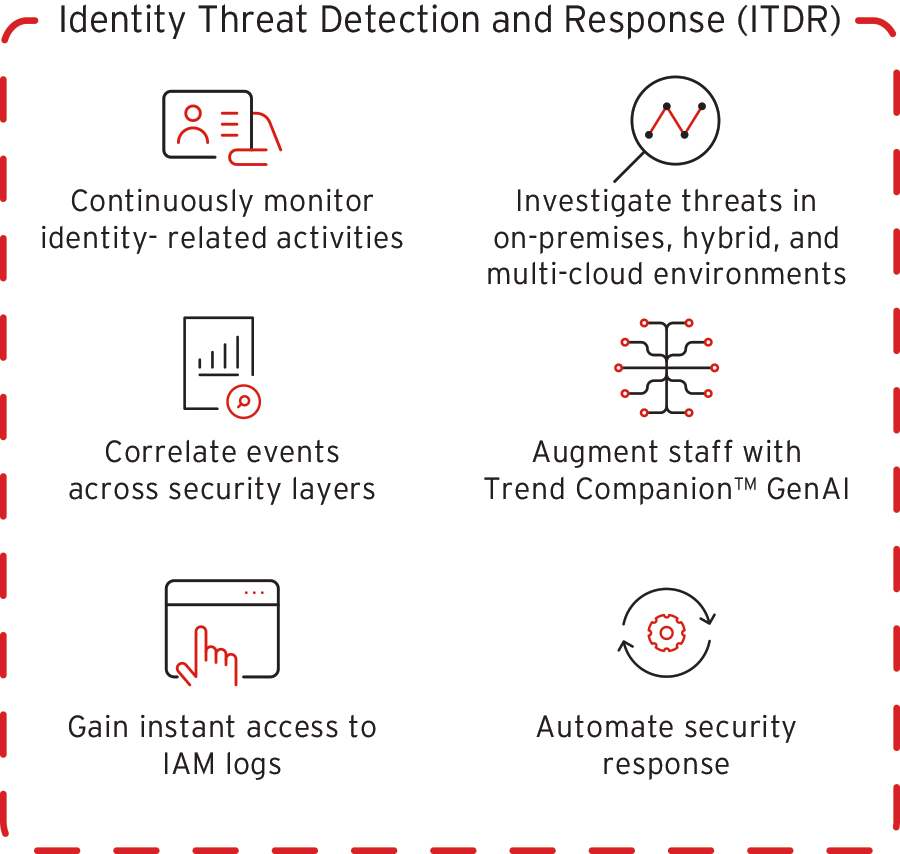
Benefits and key features of ITDR
ITDR enhances an organization's security posture by working proactively to identify threats. That can significantly reduce the time needed to detect and mitigate attacks. By addressing these types of threats in real-time, ITDR can keep attackers from escalating or getting deeper access within the network. Many more traditional detection tools can spin up too many false positives, which can become difficult to sift through. Instead, ITDR leverages AI to distinguish between legitimate users and actual threats. That leaves teams open to deal with real threats.
ITDR can achieve this via real-time monitoring, automated responses, and detailed analytics. Real-time monitoring helps tracking activities across each environment and automated responses help mitigate risks by locking compromised accounts and using analytics to detect anomalies.
Organizations adopting ITDR can also benefit from the stronger overall security posture it provides, as well as a reduction in identity-related incidents. It's especially valuable in environments with a growing attack surface, like organizations moving to the cloud. By focusing on identities, ITDR can offer better visibility and control over how identities are used and managed. This can lead to fewer breaches, faster incident response times, and better compliance.
ITDR strategies
A successful ITDR strategy should include elements like comprehensive identity monitoring, authentication options, and a variety of automated response actions. Incorporating ITDR into a cybersecurity roadmap means setting up proactive defenses against identity-based threats.
ITDR should be aligned with the organization’s overall cybersecurity strategy instead of being siloed. That way it can support additional goals like reducing risk and staying compliant. For any successful implementation and ongoing management of ITDR, organizations should give full visibilities into every type of identity, including employees, contractors, and others.
Real-time identity monitoring is important for detecting threats as they arise. ITDR can also be integrated with other security tools like IAM, SIEM, and EDR for better visibility and response options.
The evolving landscape of ITDR
ITDR is an essential tool for organizations who want to protect their digital assets in an increasingly complex threat landscape. By focusing on identity, ITDR can secure more comprehensive protection across identity-focused ecosystems.
Businesses and organizations must adopt ITDR practices to stay ahead of the curve when it comes to cyber crime. Implementing ITDR is one huge, proactive step toward a secure and resilient identity infrastructure that can help safeguard credentials and more.
The role of identity in cybersecurity is only going to continue to get larger with more services and becoming identity-driven. The landscape is always changing, which is important to remember. The future should always be kept top of mind with that fact considered. For organizations that want to improve their security framework, ITDR can be a huge asset to their defense strategy overall.
Related Articles
Trend 2025 Cyber Risk Report
From Event to Insight: Unpacking a B2B Business Email Compromise (BEC) Scenario
Understanding the Initial Stages of Web Shell and VPN Threats: An MXDR Analysis
The Forrester Wave™: Enterprise Detection and Response Platforms, Q2 2024
It’s Time to Up-Level Your EDR Solution
Silent Threat: Red Team Tool EDRSilencer Disrupting Endpoint Security Solutions
Modernize Federal Cybersecurity Strategy with FedRAMP
2025 Gartner® Magic Quadrant™ for Endpoint Protection Platforms (EPP)