Coinminers are one of the more profitable types of malware for malicious actors, and they require little maintenance once installed on a victim’s device. The malicious actor can have a coinminer masquerade itself as a legitimate app, trick susceptible users into running it on their systems, and just wait for the profits to roll in. In this light, it would be in the best interest of developers to put in the work and continuously improve these miners.
In this post, we share the results of our analysis of a coinminer sample sourced in early January 2022. This sample uses several modified open-source components that the malicious actor modified for their purposes. The sample was also found using i2pd (aka I2P Daemon) to hide its network traffic. I2pd is a C++ implementation of the Invisible Internet Protocol or I2P client. I2P is a universal anonymous network layer that allows for anonymous end-to-end encrypted communications — the participants do not reveal their real IP addresses. Previously, other Mac malware samples (Eleanor, DOK, Keranger) used Tor to hide their network activity, so this usage of i2pd is new.
Arrival of the coinminer on a device
The main malware sample is detected as Coinminer.MacOS.MALXMR.H (SHA 256 9518906dc416de6c6a5d17479244cf698b062c1d6b4425d86ee6895ce66c7c39). It is a Mach-O file that was flagged by several vendors early since it contains XMRig-related strings that can be easily caught by sourcing tools such as Yara. XMRig is a command-line app for mining Monero cryptocurrency and is typically used by other malware to perform cryptomining because of its availability and ease of use.
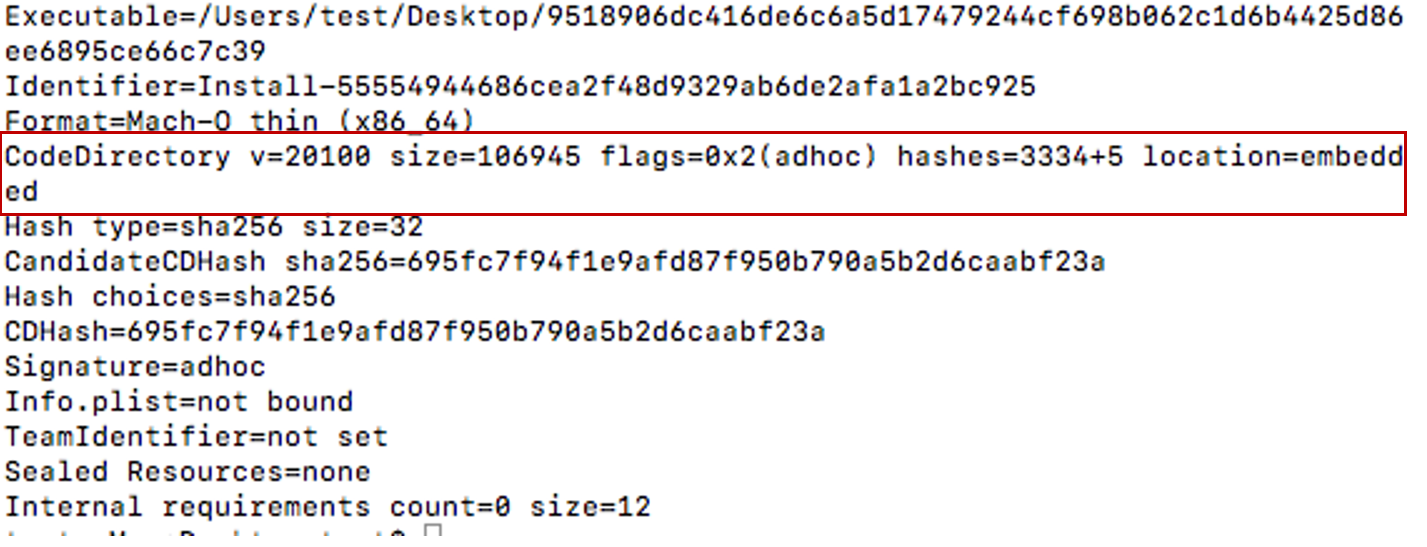
The main Mach-O sample was found to be ad hoc-signed, as seen in Figure 1. This means that the Mach-O binary will not easily run on Mac systems and might be blocked by Gatekeeper, which is a built-in security feature for macOS that enforces code signing.
We suspected that the Mach-O sample arrived packaged in a DMG (an Apple image format used to compress installers) for Adobe Photoshop CC 2019 v20.0.6. However, the parent file was not successfully sourced. We reached this conclusion based on the snippet of code in Figure 2, which was found in one of its dropped files. In this code, the sample attempts to launch a non-existent file in the /Volumes path. It is important to note that for DMG files, they are mounted by default in the /Volumes directory when double-tapped on macOS.

Installation of the coinminer
The main Mach-O sample (detected as Coinminer.MacOS.MALXMR.H) was found to contain several embedded Mach-O files. When executed, it leverages the AuthorizationExecuteWithPrivileges API to escalate privileges by prompting the user for credentials.


The sample will then drop the following files into the system:
- /tmp/lauth
- /usr/local/bin/com.adobe.acc.localhost
- /usr/local/bin/com.adobe.acc.network
- /usr/local/bin/com.adobe.acc.installer.v1
lauth file used for persistence
lauth is the Mach-O file responsible for creating the following file for the malware’s persistence routine: /Library/LaunchDaemons/com.adobe.acc.installer.v1.plist. It is this file that launches the /usr/local/bin/com.adobe.acc.installer.v1 on every startup.

The sample also attempts to launch the following non-existent file: /Volumes/Adobe Photoshop CC 2019 v20.0.6/Adobe Zii 2019 4.4.2.app/Contents/MacOS/.Patch.

com.adobe.acc.installer.v1 file for launching binaries
The file com.adobe.acc.installer.v1 is a Mach-O binary launched by com.adobe.acc.installer.v1.plist on every startup. Upon execution, it sleeps for 60 seconds then launches the following Mach-O binaries:
- /usr/local/bin/com.adobe.acc.localhost
- /usr/local/bin/com.adobe.acc.network

com.adobe.acc.localhost used for mining routine
The Mach-O binary com.adobe.acc.localhost is responsible for the mining routine. The file is a modified XMRig command-line app. It can be seen by typing --help or --version in the parameters when launching the app. The --version parameter displays the version of the XMRig binary, and the --help parameter displays the list and description of the parameters that can be used.

XMRig is an open-source, cross-platform command-line app used for mining cryptocurrency. A user can input their mining server address as well as the username/password for the mining server from the command-line as parameters. Alternately, users can also load a JSON-formatted configuration file instead of using parameters.

For this sample, we cross-examined the file with the XMRig we downloaded from https://xmrig.com/, and we were able to observe the following JSON-formatted config file in the com.adobe.acc.localhost binary. This embedded config file was not present in the other XMRig binaries we sourced.

Here are the following notable entries in the embedded config file:
- Mining server: 127.0.0.1:4545
- Username: pshp
- Password: x
It should be noted that the mining server address seems invalid since the 127.0.0.1 address is a local host address.

Identifying /usr/local/bin/com.adobe.acc.network as a modified i2pd app
Upon checking the readable strings in the com.adobe.acc.network Mach-O file, we were able to identify that it is a modified i2pd app. This finding is supported by the following display from the command line when using the --version or --help parameter.

As stated previously, i2pd is an open-source alternate implementation of I2P that is written in C++ (rather than Java).
I2P is an anonymous network layer (implemented as a mix network) that allows for censorship-resistant, peer-to-peer communication. Anonymous connections are achieved by encrypting the user's traffic (by using end-to-end encryption) and sending it through a volunteer-run network of roughly 55,000 computers distributed around the world. I2P can also be seen as an alternative to Tor.
We compared the malware binary with the official binary with the same version downloaded from this link: https://github.com/PurpleI2P/i2pd/releases/download/2.27.0/i2pd_2.27.0_osx.tar.gz.
Since the binary is around 10 MB, finding the malware routine is challenging. Because of this, we focused our attention on the readable strings and codes not found on the official version. We were then able to find the following suspicious string and the related code snippet: e4ppgzueqjiam3qvhzffwraakvcgzrjp5dzl3xzv24w6q5rjr7kq.b32.i2p:4545I.

The following information was taken from the image in Figure 13:
client: ""
client.type: client
client.address: 127.0.0.1
client.port:4545
client.destination: e4ppgzueqjiam3qvhzffwraakvcgzrjp5dzl3xzv24w6q5rjr7kq.b32.i2p:4545
client.keys: transient
We looked into the i2pd documentation and we were able to find some useful information from this link: https://i2pd.readthedocs.io/en/stable/user-guide/tunnels/#client-tunnels.

Based on the aforementioned information, we can conclude that the XMRig traffic to 127.0.0.1:4545 will be tunneled by i2pd to e4ppgzueqjiam3qvhzffwraakvcgzrjp5dzl3xzv24w6q5rjr7kq.b32.i2p:4545. We can view this connection using the lsof terminal command.

It should be noted that the site e4ppgzueqjiam3qvhzffwraakvcgzrjp5dzl3xzv24w6q5rjr7kq.b32.i2p:4545 can only be accessed through I2P.
Discovering older samples
We looked for other similar samples in VirusTotal and our sample collection using TLSH, Yara, and other tools. We were able to find the following samples that also uses i2pd to tunnel traffic to an I2P site to download possibly malicious samples.
| Sha256 | Date first seen |
| cbad9d6fd5b7d2e8860735e02f3bc54b9fc0d044df508f2293a60f2741ed7a66 | Oct 2019 |
| cc483d9aa67048f7249f970337e329280b5ceb05053796ea44476e153e392686 | Feb 2020 |
| f24da6301f95432a63eb98f8954e1da6f7275b73d0bde76052d66a6d2e587df5 | Mar 2020 |
| 42f982cde3d7aa9c5b86abe6c94119f7e4351fe84fe5ede41a1f1f2e0ab45be0 | Mar 2020 |
| 3028436248053280a93c3bedbefa65cacaf6e805e98a9bde09d858db974aab09 | May 2020 |
After analyzing the older samples, we found certain similarities:
- These samples were suspected to masquerade as Adobe Photoshop or Logic Pro X.
- All five samples use i2pd to access the same i2pd download server.
- The download server hosts several files.
- Some samples utilize random file names and zero-byte padding to evade detection.
- Four samples were observed to have a persistence routine. One sample attempts to overwrite the Mach-O executable in the installed Adobe Photoshop app.
- All samples were suspected to be packaged in a DMG file since these samples try to launch or copy from /Volumes directory where DMG files are mounted by default.
- For the downloaded file with suffix “_md5”, its content is expected to be an md5 hash. The hash will be compared to the md5 hash of the other downloaded file. If they are not equal, the file with the “_md5” suffix will retry the download.
- For the older samples, two tunnels were created but only 127.0.0.1:4546 is being used. The latest coinminer sample only creates one tunnel: 127.0.0.1:4545.

More details about these older samples can be seen in the Appendix.
Conclusion
In this blog, we investigated a coinminer sample that used several personalized open-source apps to augment its malicious routine. We found that even if the modifications were minimal, they seem to be effective. We also found that this malware leveraged i2pd to hide its network traffic from the untrained eye, a departure from other malware that use the better-known Tor.
An investigation of previous iterations of the malware also showed its evolution these past few years. More importantly, we can use these findings to create the necessary security measures should this malware continue to evolve and spread in the future.
For the indicators of compromise you may download this document, and the appendix can be downloaded here.
MITRE Tactics, Techniques, and Procedures (TTPs)
| Tactic | ID | Name | Description |
| Persistence | T1543.004 | Create or Modify System Process: Launch Daemon | Launches Daemon created for persistence routine |
| Privilege Escalation | T1548.004 | Abuse Elevation Control Mechanism: Elevated Execution with Prompt | Leverages the AuthorizationExecuteWithPrivileges API to escalate privileges by prompting the user for credentials. |
| Impact | T1496 | Resource Hijacking | Uses modified XMRig for cryptocurrency mining |
| Command and Control | T1090.003 | Proxy: Multi-hop Proxy | Uses modified i2pd to access darknet mining server |
| Defense Evasion | T1222.002 | File and Directory Permissions Modification: Linux and Mac File and Directory Permissions Modification | Uses chmod +x to modify dropped file execution privileges |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Name or Location | Dropped files have Adobe substring in the file name |

