In our midyear roundup report, we shared that in the first half of 2020, there was a 70% increase in inbound attacks on devices and routers compared with the second half of 2019. This data includes attacks on Internet of Things (IoT) systems, which remain alarming and prevalent.
With the aim of protecting customers effectively by continuously monitoring trends in IoT attacks, we examined Mirai and Bashlite (aka Qbot), two notorious IoT botnet malware types that we also analyzed in our paper. In this entry, we summarized the figures relating to these botnets’ command and control (C&C) servers, IP addresses, and C&C commands. Then, zeroing in on Mirai, we collected data on the most used attack methods in propagating the malware and examined the distribution of its variants.
To do this, we monitored C&C servers linked to Mirai and Bashlite. The IP addresses and ports of the C&C servers were obtained from analyzing related malware samples from both internal database and external open-source information, such as information collected from Twitter posts. The data analyzed in this article was collected from January 1, 2019 to August 31, 2020. As we always do with gathered data, we leveraged monitoring findings in order to enhance our security products and solutions.
Thousands of active C&C servers show prevalence of IoT attacks
Table 1 shows the numbers of C&C servers that were collected in the period covered. We gathered 7,030 addresses for Mirai and 5,010 for Bashlite. Most of them were considered as “dead” or inactive. In other words, this means that they did not accept any connection at the time of their discovery. However, the rest of the servers (2,951 for Mirai and 1,746 for Bashlite) were still alive or active. We also observed that at least 2,107 Mirai servers and 1,715 Bashlite servers issued Distributed Denial of Service (DDoS) commands to their infected clients. Figure 1 shows the number of C&C servers that accepted a connection at the time of their discovery.
|
Mirai variants |
Bashlite variants |
C&C server information collected |
7,030 |
5,010 |
C&C servers that accepted a connection at the time of discovery |
2,951 |
1,746 |
C&C servers that issued at least one DDoS command |
2,107 |
1,715 |
Table 1. Numbers of C&C servers
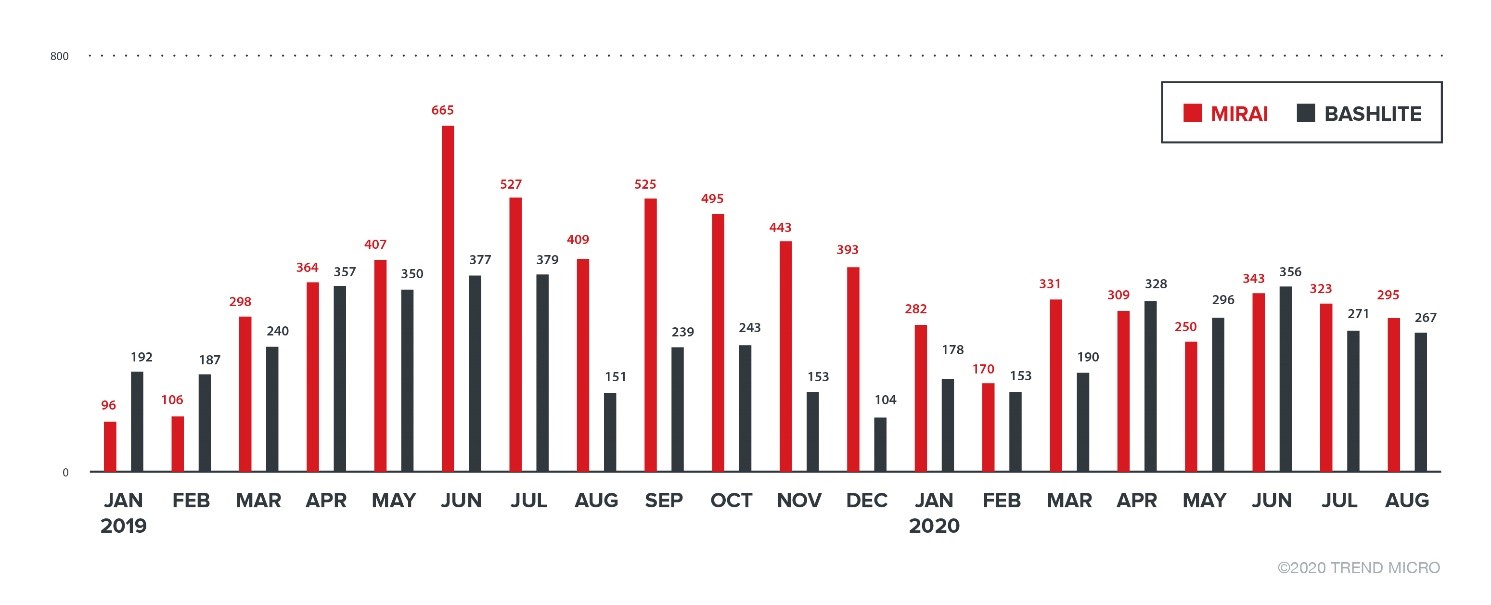
It is evident that the number of active C&C servers is still high, despite the fact that it has been years since these malware types were first exposed to the public (around 2016 in the case of Mirai and around 2014 in the case of Bashlite). We also found 573 common IP addresses among the C&C servers of the two malware families, so there is a possibility that some cybercriminals use both Mirai and Bashlite as tools. It is also possible that the same IP address was reused by another cybercriminal.
Hundreds of commands issued shed light on botnet activity
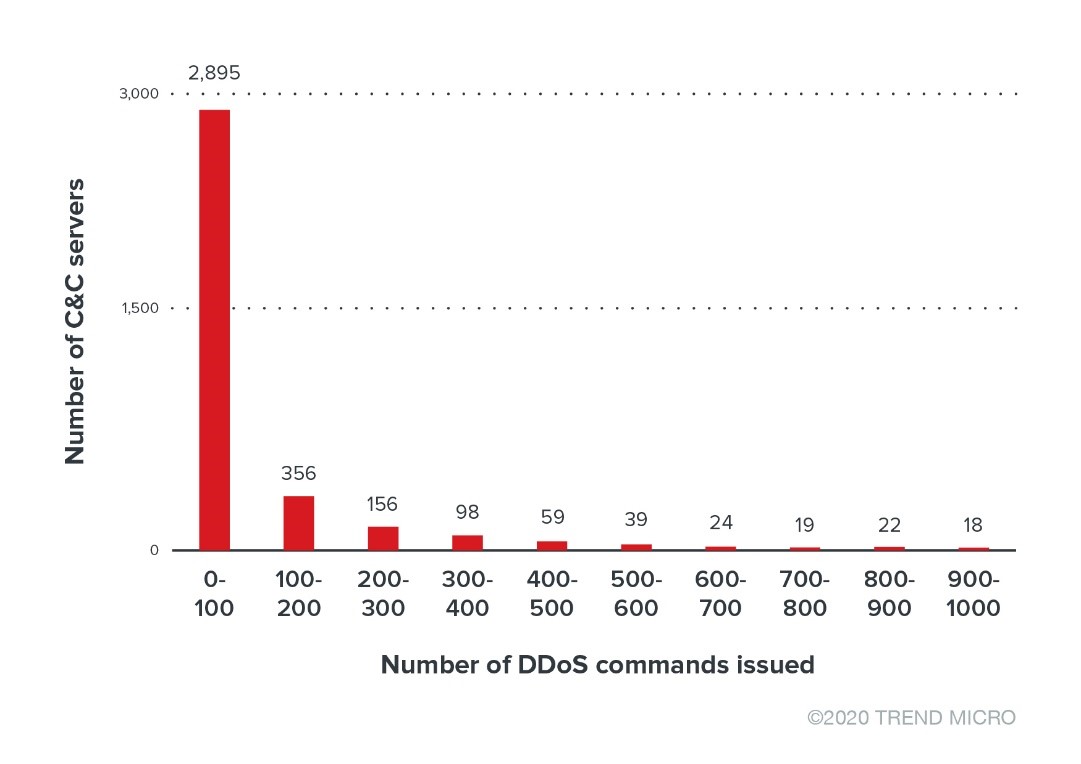
In total, we found 3,822 C&C servers that issued DDoS commands averaging at 248.8. Additionally, we saw a server issue an avalanche of 64,991 commands. Figure 2 shows a histogram of DDoS commands. Besides the data shown on the chart, we also found 136 C&C servers that issued over 1,000 commands. As seen in the illustrated distribution, most C&C servers issued less than 500 commands.
A relatively low number of servers were working actively, and it seems that some inactive C&C servers were either only used for testing purposes or are not well-operated.
We also queried information using WHOIS and discovered organizations behind the IP addresses of C&C servers. Most C&C servers were built upon hosting services. As a matter of fact, some of these are bulletproof and utilized by cybercriminals to operate C&C servers while anonymizing themselves. As we shared in our research on underground hosting, some documents explain how to build and operate a C&C server in a bulletproof hosting service. In another research, we also mentioned that IoT malware source codes are openly available in the underground. This availability of information, therefore, makes it easier for cybercriminals to build tools that they will use for compromise.
Zeroing in on Mirai
Attack methods used by Mirai
Mirai families can target various architectures such as ARM, x86, MIPS, SH4, and others. We analyzed Mirai samples collected in the aforementioned time frame and examined what kinds of attacks are deployed for them. Table 2 shows the top five types of attack methods employed.
From these observations, we found that relatively old vulnerabilities such as CVE-2017-17215, CVE-2014-8361, CVE-2018-10561 were still widely used. Also, a lot of the attacks utilized password listing to infiltrate devices with default or weak credentials.
Attack method name |
Explanation |
C&C servers connected to samples |
|
1 |
Command injection attack that targets Huawei HG532 router |
1423 |
|
2 |
Password listing |
The malware uses hard-coded credentials to log in to devices that have default or weak credentials. |
607 |
3 |
Command execution attack using UPnP SOAP vulnerability in Miniigd that targets devices developed with Realtek SDK |
520 |
|
4 |
An attack that exploits remote code injection vulnerability in ThinkPHP 5.0.23/5.1.31 |
422 |
|
5 |
Authentication Bypass and Command Injection vulnerabilities in GPON routers |
173 |
Table 2. Attack methods used by Mirai variants for infection
C&C servers related to prevalent Mirai variants
Multiple malware samples come from the same distribution servers. In this case, the contents of the samples are almost the same except for their target architectures. To describe attack methods more precisely, we counted the number of C&C servers connected to the samples.
Figure 3 shows the numbers of C&C servers related to specific strings that seem to carry a variant name. The top 11 strings shown in this chart are found to be related to a total of 5,740 servers, not including those servers related to other various strings (148) or servers with unknown string information (139). The strings, usually XOR-encoded, are revealed through sandbox analysis of malware samples associated with the servers. Note that most of these are only from open-sourced information; therefore, the sum of numbers does not match the figures in Table 1.

From this data, we found that the variant strings “LZRD”, “SORA”, “UNST”, “Cult”, and “Mirai” are the most prevalent. It should also be noted that although the variant string is the same among samples, this does not mean that the same cybercriminal or group uses these malware samples or C&C servers. In this case, we only perceive a high probability that these malware samples are based on the same source code.
Leveraging IOC data for enhanced protection
To protect our customers from cyberthreats, we utilize the Indicators of Compromise (IOCs) collected from data (including the monitoring activity mentioned in this article) for our various threat monitoring systems to bolster the threat detection ability of our products. We collect URLs for IoT malware downloads, add them to our Web Reputation Database, and tag them accordingly. This prevents customers’ devices from connecting to such malicious URLs. Our Trend Micro™ Home Network Security also blocks connections to C&C servers. Moreover, once we find a new sample during monitoring, we proactively create a detection pattern that enables our products to detect the sample as a threat.
Defending IoT systems from attacks
Most IoT malware utilize the vulnerabilities of IoT devices or vulnerable credentials for infection. To prevent being compromised by IoT malware, users are advised to perform the following best practices:
- Do not use default usernames and passwords. Instead, create strong passwords that can’t be guessed easily. This makes devices less vulnerable to brute-force attacks or password listing.
- Regularly apply software updates from vendors to patch vulnerabilities that allow infection.
- If unnecessary to its function, do not connect a device to the internet. Rather, keep it on an internal network under a gateway router to prevent attackers from accessing it.
The following Trend Micro solutions are recommended for IoT-related threats:
- Home Network Security – defends internet-connected devices against attacks by using intelligent network scanning technology to block threats at the router level.
- TippingPoint® Next-Generation Intrusion Prevention System (NGIPS) – analyzes and protects devices from advanced threats that exploit vulnerabilities.

