The Unix-programming community commonly uses shell scripts as a simple way to execute multiple Linux commands within a single file. Many users do this as part of a regular operational workload manipulating files, executing programs, and printing text.
However, as a shell interpreter is available in every Unix machine, it is also an interesting and dynamic tool abused by malicious actors. We have previously written about payloads deployed via shell scripts to abuse misconfigured Redis instances, expose Docker APIs, or remove rival cryptocurrency miners. Here we take note of the ways shell scripts have changed in the hands of cybercriminals, and how it can be employed in the development of malware payloads in malicious routines.
Changing commands and programming techniques
The technique of abusing the command-line interpreter is not new; in fact, it's widely leveraged in the wild. However, we started to notice the increase in the scripts' changes and quality.
In the past, shell scripts were relatively straightforward combinations of simple commands with plain links directly deploying the payload. But as the threats started to evolve, malicious actors are now using more advanced commands and programming techniques.

Plain text links were replaced with Base64-encoded text, while some of the code chunks were downloaded or encoded payloads. This is likely done to hide direct payload links, evade security rules used for their identification, and make analysis more difficult.

The encoded text is decoded using Base64 and passed to a bash shell interpreter to execute the shell script.
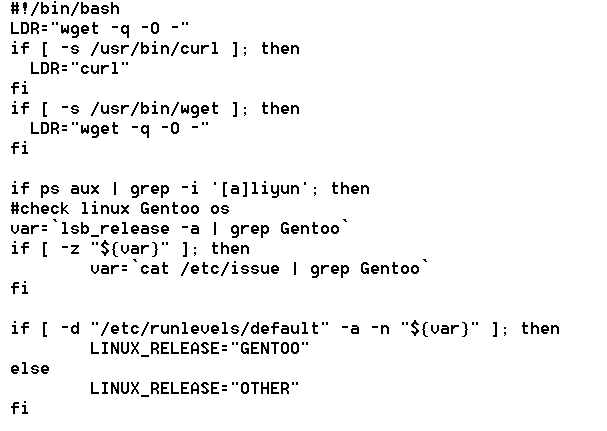
The commands were formerly executed regardless of the targeted service running on the server. Nowadays, the script is capable of checking if the service is running or not, and saving some of the CPU time for their payloads. It can be executed together with newer versions also encoded with Base64. It can also substitute variables for specific links.



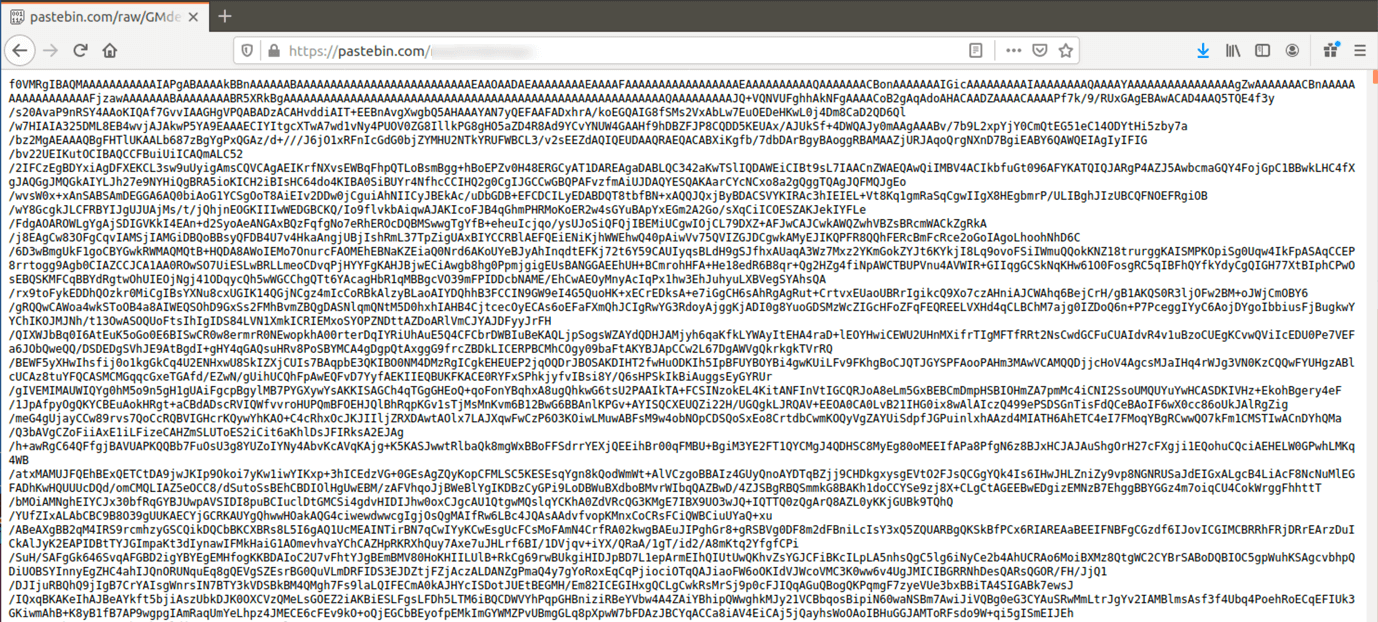
We also noticed another development in the use of Pastebin for storing parts of the script, such as in the URL and the whole payload or helper application, as in this case of a malicious routine dropping an XMrig cryptocurrency miner.

Conclusion
Malicious actors constantly improve and optimize their routines and techniques, such as their shell scripts capability to obfuscate and deliver payloads. To maximize profits and evade improving detection and mitigation technologies, cybercriminals will employ even previously documented and discovered techniques for other operating systems or combine them with new ones. While some of the techniques have been used in previously observed malware routines or environments, these are quite new for shell scripts and malware families.
In the past, most of the payloads deployments were in plain text and focused on their specific tasks. Now we're beginning to see obfuscation mechanisms inside shell scripts. We should expect even more obfuscation as malware authors try to hide actual payloads in the future.
It's still quite early to claim that these techniques signify that Linux obfuscations are becoming more sophisticated. However, this evolution of shell scripts, wherein they're being used to deliver payloads, is worth noting for further caution and observation. Moreover, researchers can expect plain text to be less common; they're going to need to decode several layers at a time for a complete analysis.
Trend Micro solutions
Trend Micro solutions powered by XGen™ security, such as ServerProtect for Linux and Trend Micro Network Defense, can detect related malicious files and URLs and protect users' systems. Trend Micro Smart Protection Suites and Trend Micro Worry-Free™ Business Security, which have behavior monitoring capabilities, can additionally defend against these types of threats by detecting malicious files, thwarting behaviors and routines associated with malicious activities, as well as blocking all related malicious URLs.
Indicators of Compromise (IoCs)
SHA256 |
Detection Name |
1aaf7bc48ff75e870db4fe6ec0b3ed9d99876d7e2fb3d5c4613cca92bbb95e1b |
Trojan.SH.MALXMR.UWEKK |
bea4008c0f7df9941121ddedc387429b2f26a718f46d589608b993c33f69b828 |
|
0742efecbd7af343213a50cc5fd5cd2f8475613cfe6fb51f4296a7ec4533940d |
Trojan.SH.HADGLIDER.TSE |
3c7faf7512565d86b1ec4fe2810b2006b75c3476b4a5b955f0141d9a1c237d38 |
Coinminer.Linux.MALXMR.UWELH |
3eeaa9d4a44c2e1da05decfce54975f7510b31113d8361ff344c98d3ddd30bf4 |
|
543ceebd292e0e2c324372f3ab82401015f78b60778c6e38f438f98861fd9a2d |
|
882473c3100389e563b05051ae1b843f8dd24c807a30acf0c6749cd38137876b |
|
c82074344cf24327fbb15fd5b8276a7681f77ccacef7acc146b4cffa46dabf62 |
|
eaf9dd8efe43dcf606ec0a531d5a46a9d84e80b54aa4a019fa93884f18c707c3 |
|
f65bea9c1242ca92d4038a05252a70cf70f16618cf548b78f120783dfb9ccd0e |

